
Zero Trust Architecture Modern Security Model Mitigating use after free security vulnerabilities in c and c with language support for type isolating allocators oliver hunt llvm dev meeting 2024. Type based segregation of heap allocations has long been acknowledged as an effective mechanism to mitigate memory safety vulnerabilities in real world c and c .

Top 10 Llm Vulnerabilities Keeping Pace With Ai Security 2024 us llvm dev mtg program committee: i’m pleased to announce the 2024 llvm developers’ meeting program! as a quick reminder, early bird registration is ending september 20th. this is also the registration deadline to guarantee a t shirt. register here: …. Protecting against "use after free" vulnerabilities requires a multi faceted approach encompassing secure coding practices, robust memory management techniques, thorough testing, and proactive security measures. Full name oliver hunt pronoun s he him his job title engineer company affiliation apple, inc. speaker bio n a speaking at mitigating use after free security vulnerabilities in c and c with language support for type isolating allocators. In this paper, we present safeslab: a heap hardening extension that aims to mitigate use after free vulnerabilities via a novel and efficient address aliasing approach.

Top 10 Linux Vulnerabilities In 2024 Full name oliver hunt pronoun s he him his job title engineer company affiliation apple, inc. speaker bio n a speaking at mitigating use after free security vulnerabilities in c and c with language support for type isolating allocators. In this paper, we present safeslab: a heap hardening extension that aims to mitigate use after free vulnerabilities via a novel and efficient address aliasing approach. We show how llvm clang can be used to compile regular, freestanding c to target the gpu as well as show how to use this to create gpu libraries that can be stacked upon eachother. Mitigating use after free security vulnerabilities in c and c with language support for type isolating allocators oliver hunt llvm weekly #562, october 7th 2024. In this talk we take a look at llvm’s approach to supply chain security. The cve 2024 47691 vulnerability is a recently identified issue within the linux kernel, specifically affecting the f2fs or flash friendly file system. this vulnerability occurs due to a use after free condition in the f2fs stop gc thread () function.
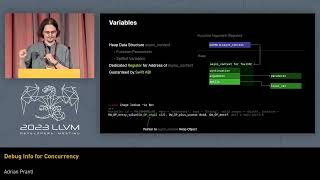
Llvm Dev Mtg 2023 Enhancing Llvms Debug Info For Concurrency Synthmind We show how llvm clang can be used to compile regular, freestanding c to target the gpu as well as show how to use this to create gpu libraries that can be stacked upon eachother. Mitigating use after free security vulnerabilities in c and c with language support for type isolating allocators oliver hunt llvm weekly #562, october 7th 2024. In this talk we take a look at llvm’s approach to supply chain security. The cve 2024 47691 vulnerability is a recently identified issue within the linux kernel, specifically affecting the f2fs or flash friendly file system. this vulnerability occurs due to a use after free condition in the f2fs stop gc thread () function.

2024 Mtg Set Already Has A Major Misprint In this talk we take a look at llvm’s approach to supply chain security. The cve 2024 47691 vulnerability is a recently identified issue within the linux kernel, specifically affecting the f2fs or flash friendly file system. this vulnerability occurs due to a use after free condition in the f2fs stop gc thread () function.
.png?width=353&height=200&name=fortimanager-blog-ET-preview (1).png)
August 2024 Latest Malware Vulnerabilities And Exploits