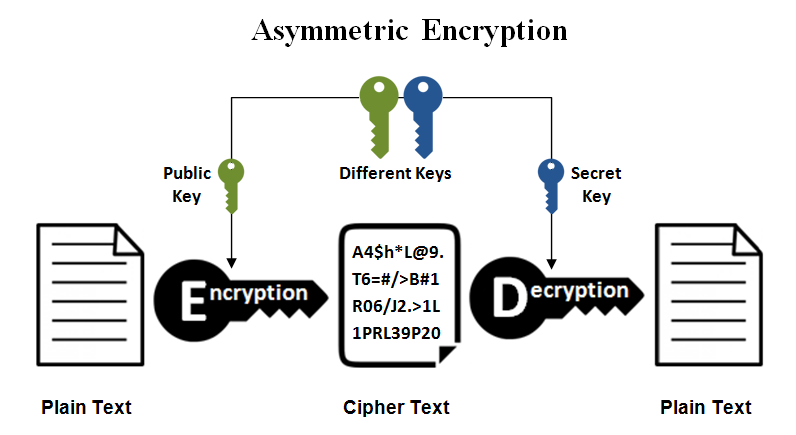
Asymmetric Key Encryption And Digital Signatures In Practice In this article, we will learn how asymmetric key encryption and digital signatures work from a practical perspective. in the previous article, we learned the basics of symmetric key encryption, including how to generate keys using a password based key derivation function called pbkdf2, how block ciphers work and how to encrypt decrypt data. This cryptographic system addresses two major challenges faced in traditional (symmetric) cryptography: key distribution and digital signatures. asymmetric algorithms use one key for encrypting data and another, related key for decrypting it.
Asymmetric Key Encryption And Digital Signatures In Practice If the sender and the recipient of the data use the same key to encrypt and decrypt the data, it’s called symmetric encryption and if the keys are different for encryption and decryption then it’s asymmetric encryption. The world of modern cryptography is built upon the concept of asymmetric encryption, and the pillars of asymmetric encryption are these three algorithms: rsa, diffie hellman, and dsa (digital signature algorithm). Akc offers several useful functions, such as: encryption and decryption to enable confidentiality of communications. digital signatures to ensure authenticity, integrity, and non repudiation. secure key exchange to facilitate subsequent use of symmetric cryptosystems. The asymmetric key cryptosystems provide key pair generation (private public key), encryption algorithms (asymmetric key ciphers and encryption schemes like rsa oaep and ecies), digital signature algorithms (like dsa, ecdsa and eddsa) and key exchange algorithms (like dhke and ecdh).
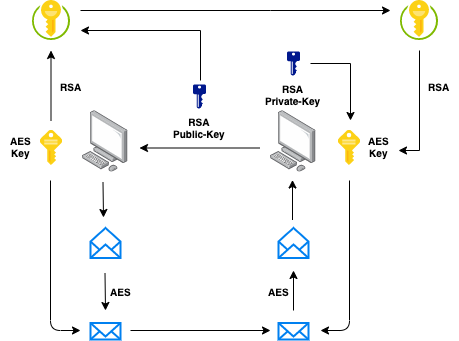
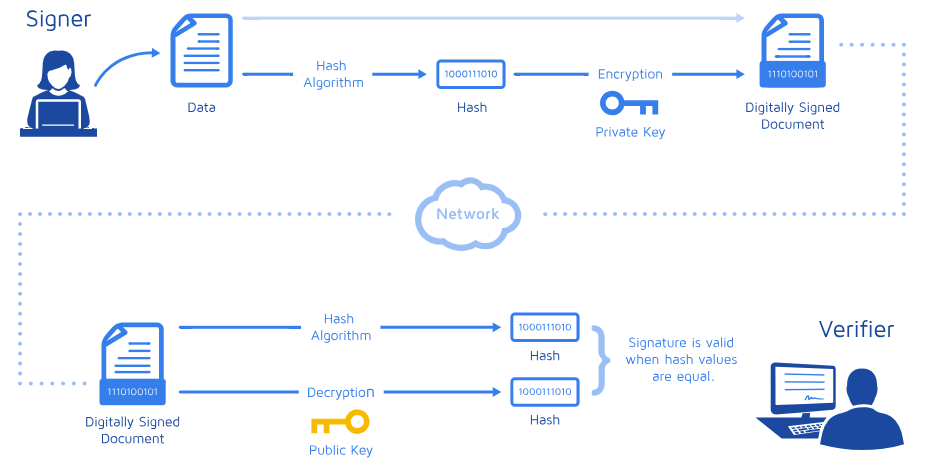
Asymmetric Key Encryption And Digital Signatures In Practice Akc offers several useful functions, such as: encryption and decryption to enable confidentiality of communications. digital signatures to ensure authenticity, integrity, and non repudiation. secure key exchange to facilitate subsequent use of symmetric cryptosystems. The asymmetric key cryptosystems provide key pair generation (private public key), encryption algorithms (asymmetric key ciphers and encryption schemes like rsa oaep and ecies), digital signature algorithms (like dsa, ecdsa and eddsa) and key exchange algorithms (like dhke and ecdh). E in a digital signature scheme. in an asymmetric encryption scheme, the holder of the secret key is a receiver, using the secret key to decrypt iphertexts sent to it by others. in a digital signature scheme, the holder of the secret key is a sender, using the secret key to tag its own messages so that th. Requirements for public key encryption key generation: computationally easy to generate a pair (public key pk, private key sk) encryption: given plaintext m and public key pk, easy to compute ciphertext c=epk(m) decryption: given ciphertext c=epk(m) and private key sk, easy to compute plaintext m infeasible to learn anything about m from c. Discover how public–private key pairs power secure communications, authentication, and digital signatures, forming the backbone of modern cryptographic security. Asymmetric encryption is built on the idea of key pairs: public key: shared openly, allowing anyone to encrypt data or verify digital signatures. private key: kept secret by the owner, used to decrypt data or create digital signatures.

Lecture 4 Asymmetric Key Cryptography Part I Pdf E in a digital signature scheme. in an asymmetric encryption scheme, the holder of the secret key is a receiver, using the secret key to decrypt iphertexts sent to it by others. in a digital signature scheme, the holder of the secret key is a sender, using the secret key to tag its own messages so that th. Requirements for public key encryption key generation: computationally easy to generate a pair (public key pk, private key sk) encryption: given plaintext m and public key pk, easy to compute ciphertext c=epk(m) decryption: given ciphertext c=epk(m) and private key sk, easy to compute plaintext m infeasible to learn anything about m from c. Discover how public–private key pairs power secure communications, authentication, and digital signatures, forming the backbone of modern cryptographic security. Asymmetric encryption is built on the idea of key pairs: public key: shared openly, allowing anyone to encrypt data or verify digital signatures. private key: kept secret by the owner, used to decrypt data or create digital signatures.

Pinterest Discover how public–private key pairs power secure communications, authentication, and digital signatures, forming the backbone of modern cryptographic security. Asymmetric encryption is built on the idea of key pairs: public key: shared openly, allowing anyone to encrypt data or verify digital signatures. private key: kept secret by the owner, used to decrypt data or create digital signatures.