
Aws Security Hub Containers Learn about amazon container features, container services including ecs, fargate and eks, and how to secure your containers in the aws cloud. Aws manages the security of the infrastructure that runs your containers. however, controlling access for your users and your container applications is your responsibility as the customer.

Aws Containers Security Approach These curated best practices are recommended by amazon web services (aws) container and security subject matter experts in order to help raise your container security posture. With aws container security, organizations can ensure secure containerized applications, leveraging features like network policies, secret management, and threat detection to protect against vulnerabilities and data breaches. At its core, container security is the process of safeguarding containerized apps against vulnerabilities across their entire lifecycle. it includes these key measures: these elements protect containers at each stage in the container lifecycle, from creating images to deployment. In this article, we’ll explore the key components of containers on aws, including their advantages over traditional virtual machines, popular aws container services, and best practices for.
Aws Containers Complete Guide To Aws Containers At its core, container security is the process of safeguarding containerized apps against vulnerabilities across their entire lifecycle. it includes these key measures: these elements protect containers at each stage in the container lifecycle, from creating images to deployment. In this article, we’ll explore the key components of containers on aws, including their advantages over traditional virtual machines, popular aws container services, and best practices for. In the following sections, we’ll explore key strategies, aws security services, and third party tools to fortify our docker containers, safeguard sensitive data, and protect against evolving threats in the cloud. Learn how to protect aws container environments with best practices for ecs, eks and the extension for on premises deployments. security is a key component in any infrastructure, and aws containers are no exception. aws containers use a shared responsibility model. Discover essential aws container security best practices and how suse can help to keep your containerized systems safe from external threats and risks. This visual provides security and compliance recommendations for protecting your information, systems, and other assets that are reliant on amazon ecs.
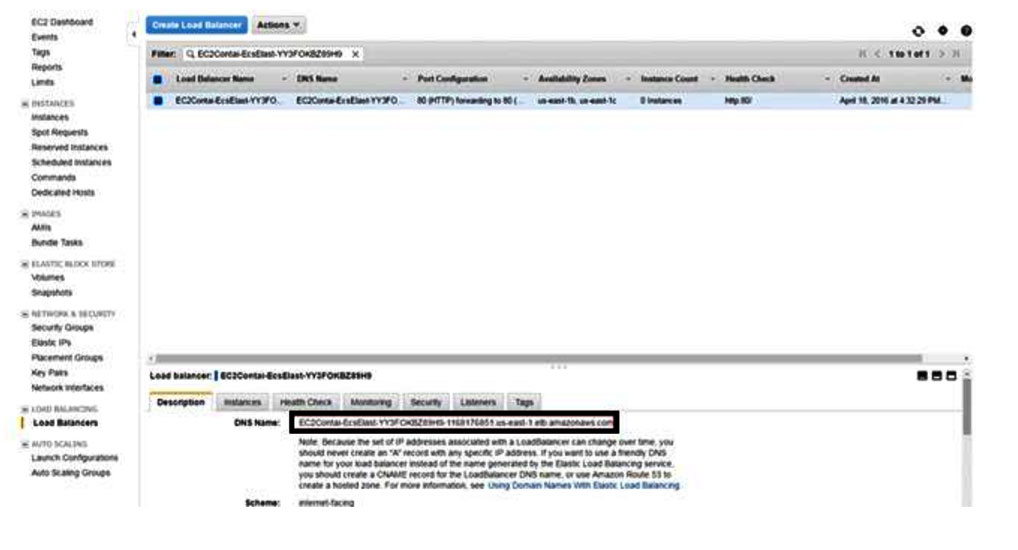
Aws Containers Complete Guide To Aws Containers In the following sections, we’ll explore key strategies, aws security services, and third party tools to fortify our docker containers, safeguard sensitive data, and protect against evolving threats in the cloud. Learn how to protect aws container environments with best practices for ecs, eks and the extension for on premises deployments. security is a key component in any infrastructure, and aws containers are no exception. aws containers use a shared responsibility model. Discover essential aws container security best practices and how suse can help to keep your containerized systems safe from external threats and risks. This visual provides security and compliance recommendations for protecting your information, systems, and other assets that are reliant on amazon ecs.
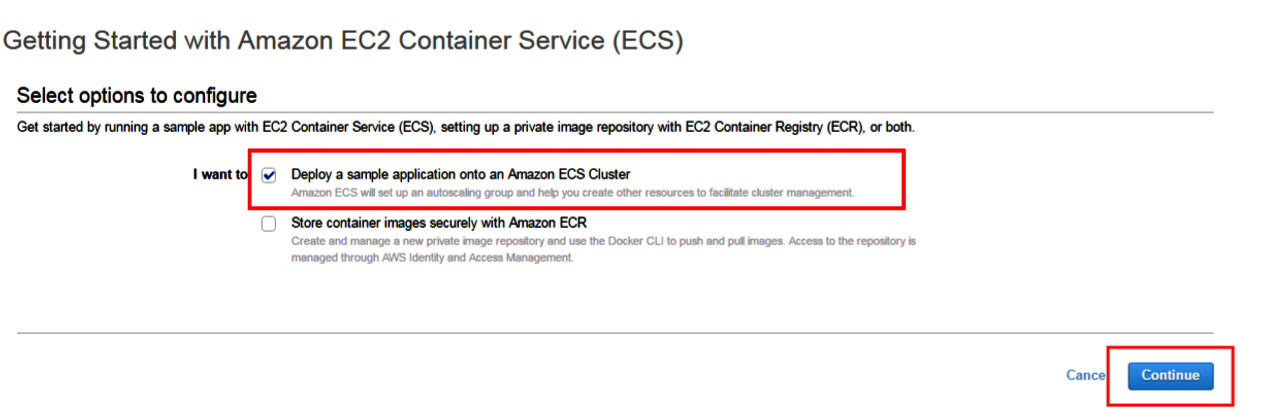
Aws Containers Complete Guide To Aws Containers Discover essential aws container security best practices and how suse can help to keep your containerized systems safe from external threats and risks. This visual provides security and compliance recommendations for protecting your information, systems, and other assets that are reliant on amazon ecs.