
Understanding The Basics Of Cryptography Digital Certificates And Xpertini. In this cryptography tutorial, we've covered basics and advanced concepts of cryptography including symmetric key cryptography, asymmetric key cryptography as well as cryptanalysis, public key cryptography and more.
Basics Of Cryptography Xpertini Start your journey through the basics of cryptographic thinking. we'll guide you from simple substitution ciphers to the mathematics that powers bitcoin, building your intuition along the way. dive deep into advanced topics, from elliptic curve cryptography to post quantum algorithms. After introducing basic cryptography concepts, this seminal textbook covers nearly all symmetric, asymmetric, and post quantum cryptographic algorithms currently in use in applications—ranging from cloud computing and smart phones all the way to industrial systems, block chains, and cryptocurrencies.a. While cryptography is the science of securing data, cryptanalysis is the science of analyzing and breaking secure communication. classical cryptanalysis involves an interesting combination of analytical reasoning, application of mathematical tools, pattern finding, patience, determination, and luck. Cryptography is the science of using mathematics to encrypt and decrypt data. cryptography enables you to store sensitive information or transmit it across insecure networks (like the internet) so that it cannot be read by anyone except the intended recipient.

An In Depth Look At Cryptography Concepts And Techniques Pdf Cipher While cryptography is the science of securing data, cryptanalysis is the science of analyzing and breaking secure communication. classical cryptanalysis involves an interesting combination of analytical reasoning, application of mathematical tools, pattern finding, patience, determination, and luck. Cryptography is the science of using mathematics to encrypt and decrypt data. cryptography enables you to store sensitive information or transmit it across insecure networks (like the internet) so that it cannot be read by anyone except the intended recipient. A major goal of cryptography ("hidden writing") is to define and construct operations that write, read, and attest to information using secrets in a way so that principals that do not know the secrets cannot perform the operations. This tutorial covers the basics of the cryptography. it explains how programmers and network professionals can use cryptography to maintain the privacy of computer data. While encryption is probably the most prominent example of a crypto graphic problem, modern cryptography is much more than that. in this class, we will learn about pseudorandom number generators, digital signatures, zero knowledge proofs, multi party computation, to name just a few examples. Below, we break down the principles that form the basis of secure ciphers. auguste kerckhoffs’ principle recommends that encryption algorithms should be public while the keys should be a secret.

Basics Of Cryptography Zsecurity A major goal of cryptography ("hidden writing") is to define and construct operations that write, read, and attest to information using secrets in a way so that principals that do not know the secrets cannot perform the operations. This tutorial covers the basics of the cryptography. it explains how programmers and network professionals can use cryptography to maintain the privacy of computer data. While encryption is probably the most prominent example of a crypto graphic problem, modern cryptography is much more than that. in this class, we will learn about pseudorandom number generators, digital signatures, zero knowledge proofs, multi party computation, to name just a few examples. Below, we break down the principles that form the basis of secure ciphers. auguste kerckhoffs’ principle recommends that encryption algorithms should be public while the keys should be a secret.

Cryptography Basics Virtual Lab Cybrary While encryption is probably the most prominent example of a crypto graphic problem, modern cryptography is much more than that. in this class, we will learn about pseudorandom number generators, digital signatures, zero knowledge proofs, multi party computation, to name just a few examples. Below, we break down the principles that form the basis of secure ciphers. auguste kerckhoffs’ principle recommends that encryption algorithms should be public while the keys should be a secret.
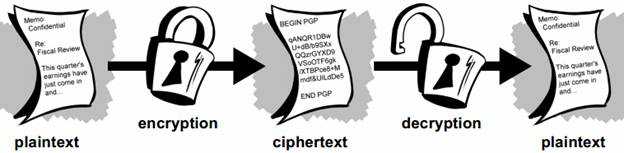
Cryptography Basics Tutorial