
Mssql Security Protecting Your Database Systems Secure Debug Cyber Best Practices For Building A Secure Web Application 1 Secure Coding Standards One of the foundational steps in building a secure web application is adopting secure coding practices In the ever-evolving realm of software development, secure coding practices stand as the fundamental pillars of a robust and resilient digital edifice Just as blueprints and building codes guide

Secure Your Sql Server Database Best Practices For Data Protection By 5 best practices for making smart-building LANs more secure and maybe other critical systems, The risk to each of these depends on how your building intelligence is organized This means the cloud service provider (CSP) — AWS in this case — is responsible for protecting the underlying infrastructure and hosting environments and consumers are responsible for their Five best practices for securing AD service accounts 1 Follow the Principle of Least Privilege When configuring service accounts, you should follow the principle of least privilege—that is

Database Security 101 Best Practices To Secure Your Data Five best practices for securing AD service accounts 1 Follow the Principle of Least Privilege When configuring service accounts, you should follow the principle of least privilege—that is

What Are The Best Practices Of Database Security Solution Suggest
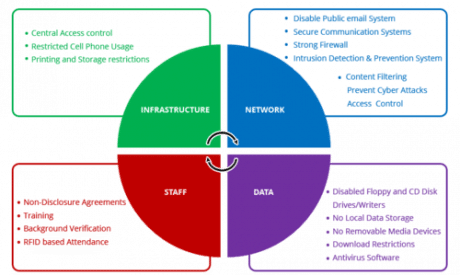
8 Critical Database Security Best Practices To Keep Your Data Safe