
Top 10 Database Security Best Practices Pdf Security Computer FBI's Criminal Justice Information Services (CJIS) compliance isn't optional when handling law enforcement data From MFA to password hygiene, see how Specops Software helps meet FBI standards while A third-party dental marketing agency's unsecured database exposed millions of patient profiles with personal information that could be exploited for identity theft and insurance fraud

What Are The Best Practices Of Database Security Solution Suggest Learn what a CRM database is, key features to look for, benefits, and best practices to help you choose and optimize the right CRM for your business Best practices for cloud security file, and database You can protect the contents of data in transit by encrypting it before transferring it to the cloud and/or by using encrypted connections This session will include topics such as recovery, data catalogs, database security best practices, and a lot more We'll finish up with 10 things to look at right now to tighten up your data universe Q&A The Database Admin's Security Burden Security is everyone's job, but in a time when data is king, SQL Server admins play a more critical role than ever in their organizations' security postures

Database Security Best Practices This session will include topics such as recovery, data catalogs, database security best practices, and a lot more We'll finish up with 10 things to look at right now to tighten up your data universe Q&A The Database Admin's Security Burden Security is everyone's job, but in a time when data is king, SQL Server admins play a more critical role than ever in their organizations' security postures Since Anthropic released the Model Context Protocol in late 2024, adoption has surged, with many companies launching their own MCP servers to help AI agents access their data While this is The National Security Agency’s Artificial Intelligence Security Center (AISC) has released the joint Cybersecurity Information Sheet (CSI), “AI Data Security: Best Practices for Securing Data Used to AS400/IBMi systems are far from immune to security challenges Modern cybersecurity best practices can minimize companies' vulnerabilities
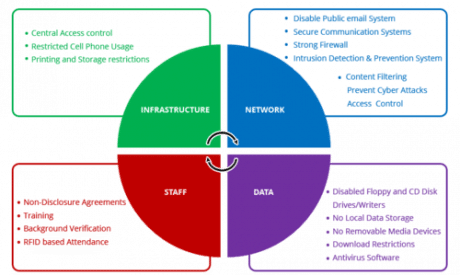
8 Critical Database Security Best Practices To Keep Your Data Safe Since Anthropic released the Model Context Protocol in late 2024, adoption has surged, with many companies launching their own MCP servers to help AI agents access their data While this is The National Security Agency’s Artificial Intelligence Security Center (AISC) has released the joint Cybersecurity Information Sheet (CSI), “AI Data Security: Best Practices for Securing Data Used to AS400/IBMi systems are far from immune to security challenges Modern cybersecurity best practices can minimize companies' vulnerabilities