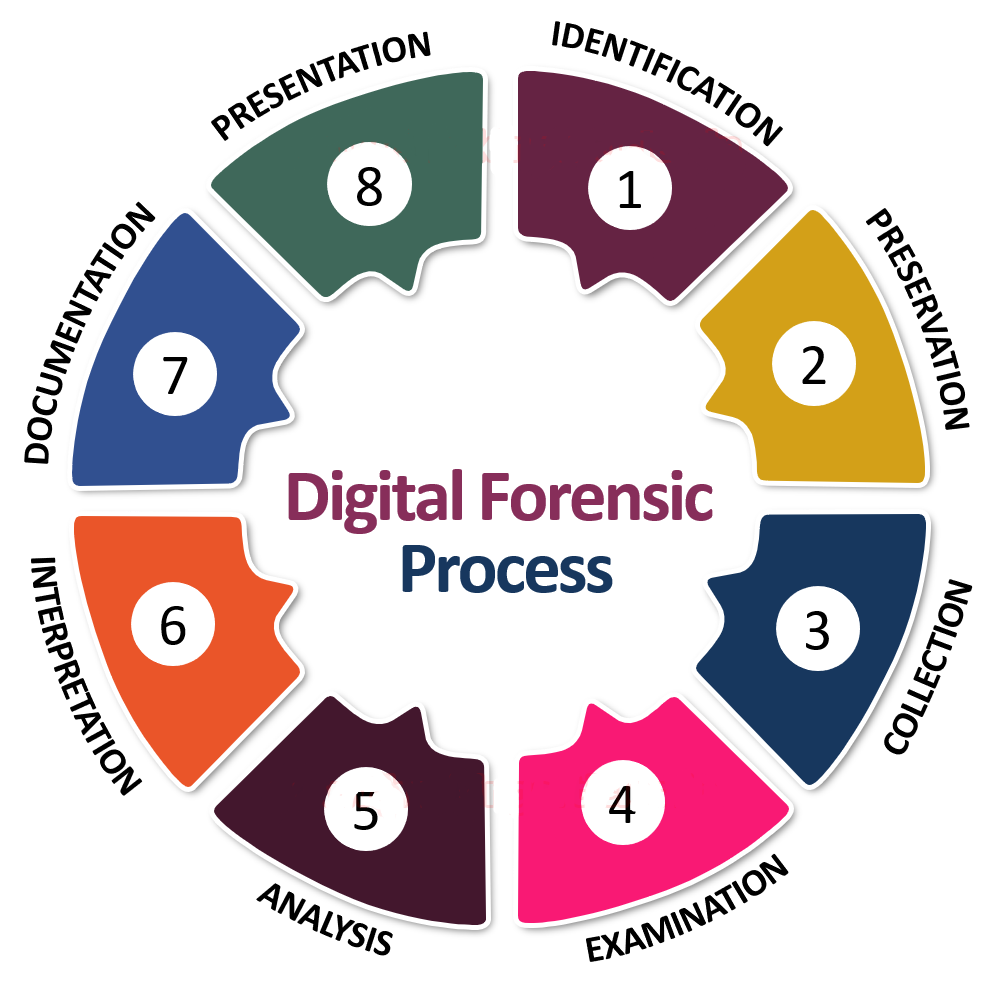
Digital Forensics Process Sino Atrium Dfir provides a deep understanding of cybersecurity incidents through a comprehensive forensic process. dfir experts gather and investigate vast amounts of data to fill in gaps of information about cyber attacks, such as who were the attackers, how they broke in, and the exact steps they took to place systems at risk. Digital forensics and incident response are branches of cybersecurity that involve identifying, investigating, containing, remediating and potentially testifying related to cyberattacks, litigations or other digital investigations.

Digital Forensics Process Sino Atrium Digital forensics plays a pivotal role in law enforcement, corporate investigations, incident response, and regulatory compliance. Digital forensics process add to wishlist categories: cyber forensics training, cybersecurity solution & products, global management training reviews (0). Digital forensics involves the process of collecting, analyzing, and preserving electronic data in order to investigate and establish evidence in cases of cybercrime or other digital misconduct. This document provides a new digital forensics and incident response (dfir) framework dedicated to operational technology. this framework expands the traditional technical steps of it incident response by giving an incident response procedure based on event escalation and provides techniques for ot digital forensics.

Sino Atrium Electronic Ind Ltd Digital forensics involves the process of collecting, analyzing, and preserving electronic data in order to investigate and establish evidence in cases of cybercrime or other digital misconduct. This document provides a new digital forensics and incident response (dfir) framework dedicated to operational technology. this framework expands the traditional technical steps of it incident response by giving an incident response procedure based on event escalation and provides techniques for ot digital forensics. This paper proposes a digital forensics framework called d4i (digital forensics framework for reviewing and investigating cyber attacks) whose aim is to enhance the examination and analysis phases of the digital forensics process. The paper demonstrates how the dfwm functions as a framework for unboxing the digital forensic investigation process based on the investigative strategy of the particular case, providing a detailed structure and depiction of the physical and investigative tasks and decisions. Sino atrium has designed and implemented a state of the art, highly redundant & fail safe architecture. sino atrium believes that having a strong and reliable infrastructure of systems and network is paramount to the success of secured solution. Comprehensive assessments and ethical hacking to identify security weaknesses and recommend actionable fixes before attackers can exploit them.

D F Incident Response Dfir Sino Atrium This paper proposes a digital forensics framework called d4i (digital forensics framework for reviewing and investigating cyber attacks) whose aim is to enhance the examination and analysis phases of the digital forensics process. The paper demonstrates how the dfwm functions as a framework for unboxing the digital forensic investigation process based on the investigative strategy of the particular case, providing a detailed structure and depiction of the physical and investigative tasks and decisions. Sino atrium has designed and implemented a state of the art, highly redundant & fail safe architecture. sino atrium believes that having a strong and reliable infrastructure of systems and network is paramount to the success of secured solution. Comprehensive assessments and ethical hacking to identify security weaknesses and recommend actionable fixes before attackers can exploit them.

Home Sino Atrium Sino atrium has designed and implemented a state of the art, highly redundant & fail safe architecture. sino atrium believes that having a strong and reliable infrastructure of systems and network is paramount to the success of secured solution. Comprehensive assessments and ethical hacking to identify security weaknesses and recommend actionable fixes before attackers can exploit them.