Github Pmvrak Container Devsecops Using Aws Codepipeline Container About container devsecops using aws codepipeline and anchore engine (inline scan). Inside the devsecops repo cd ~ environments devsecopspipeline we are going to manually push our application image to aws ecr. let’s push our docker image to ecr that was created from terraform. expand me in the console it would look this. us west 2.console.aws.amazon ecr repositories.
Container Devsecops Using Aws Codepipeline Devsecops Codepipeline We’ll make a simple code change in github to trigger the pipeline. codepipeline will kick off, codebuild will build and push the image to ecr, and amazon inspector will automatically scan it. if any critical cves are found, you’ll see them flagged right in the aws console. In this blog, i have shown how we can utilize open source dockerfile linting and container static scanning tools effectively within a sample pipeline built on aws codepipeline. Let us walk you through how i built a secure, aws native ci cd pipeline, with third party integrations like snyk and opa, to secure everything from code to infrastructure. 1. github aws codecommit: source stage. the source stage is the first and foundational step in your devsecops pipeline. Using aws codepipeline in conjunction with a devsecops approach ensures a comprehensive integration of security practices throughout the software development lifecycle.
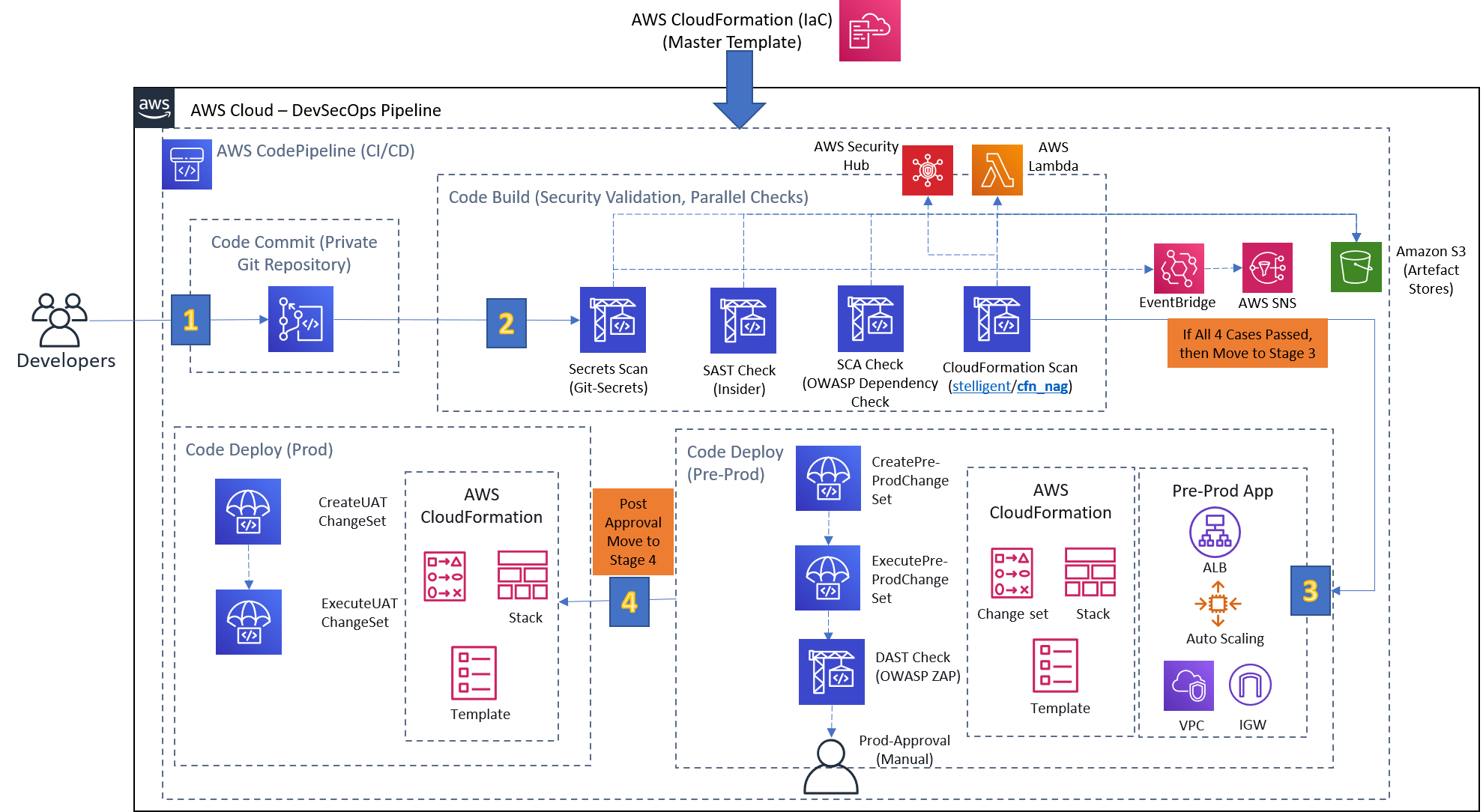
Github Dasgourav Build Devsecops Pipeline In Aws Let us walk you through how i built a secure, aws native ci cd pipeline, with third party integrations like snyk and opa, to secure everything from code to infrastructure. 1. github aws codecommit: source stage. the source stage is the first and foundational step in your devsecops pipeline. Using aws codepipeline in conjunction with a devsecops approach ensures a comprehensive integration of security practices throughout the software development lifecycle. Establishes a secure connection between aws codepipeline and a github repository. uses a random id resource to generate a unique connection name for traceability. Hosted runners for every major os make it easy to build and test all your projects. run directly on a vm or inside a container. use your own vms, in the cloud or on prem, with self hosted runners. matrix builds. In this article, we will explore a hands on guide for achieving continuous docker deployment to aws fargate from a github repository using terraform. this devops pipeline will allow developers to push code changes to a github repository and have them automatically deployed to an aws fargate cluster. This guide outlines how to deploy a node.js express app to aws using docker, aws codepipeline, codebuild, ecr, ecs (fargate), and alb (application load balancer). the deployment process is fully automated using github as the source. codepipeline → automates the ci cd process. codebuild → builds the docker image and pushes it to ecr.
Github Aws Samples Devsecops Workshop On Aws In This Workshop We Establishes a secure connection between aws codepipeline and a github repository. uses a random id resource to generate a unique connection name for traceability. Hosted runners for every major os make it easy to build and test all your projects. run directly on a vm or inside a container. use your own vms, in the cloud or on prem, with self hosted runners. matrix builds. In this article, we will explore a hands on guide for achieving continuous docker deployment to aws fargate from a github repository using terraform. this devops pipeline will allow developers to push code changes to a github repository and have them automatically deployed to an aws fargate cluster. This guide outlines how to deploy a node.js express app to aws using docker, aws codepipeline, codebuild, ecr, ecs (fargate), and alb (application load balancer). the deployment process is fully automated using github as the source. codepipeline → automates the ci cd process. codebuild → builds the docker image and pushes it to ecr.
Github Srinivasbathula9 Devsecops Pipeline In this article, we will explore a hands on guide for achieving continuous docker deployment to aws fargate from a github repository using terraform. this devops pipeline will allow developers to push code changes to a github repository and have them automatically deployed to an aws fargate cluster. This guide outlines how to deploy a node.js express app to aws using docker, aws codepipeline, codebuild, ecr, ecs (fargate), and alb (application load balancer). the deployment process is fully automated using github as the source. codepipeline → automates the ci cd process. codebuild → builds the docker image and pushes it to ecr.

Github Aakashayachit Simple Pipeline Using Aws Use Codepipeline To