Github Sumitsahoo Pgp Encryption Python Pgp Encryption In Python I have generated keys using gpg, by executing the following command gpg gen key now i need to export the key pair to a file; i.e., private and public keys to private.pgp and public.pgp, respecti. Gpg keyserver hkp: keyserver.ubuntu recv key f23275e4bf10afc1df6914a6dbd2ce893e2d1c87 gpg: keyserver receive failed: no route to host.
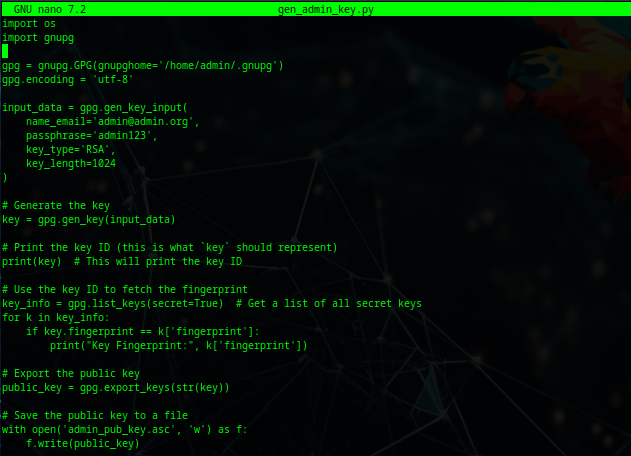
Github Barbarossa01 Pgp Encryption Decryption Python Pgp Encryption When i export a gpg private or public key, and specify armored as a switch, i get plain text key, however, the gnupgp website seems to state that these keys are actually encrypted. what's the point. Gpg: refreshing 85 keys from hkp: pool.sks keyservers gpg: keyserver refresh failed: no keyserver available ==> error: a specified local key could not be updated from a keyserver. I find it odd that gpg is the thing reporting errors, yet pacman keyring works without complaint and installing archlinux keyring (with package signatures off) also works fine. is there a direct gpg command i can use to verify a package signature in the same way pacman does, to see if that sheds any light on what the issue might be?. Reading through the script, how about `type a gpg` and `gpg version`? it looks like it uses gpg to create that file before it chmods it.

Gpg Pgp Tutorial Getbutterfly I find it odd that gpg is the thing reporting errors, yet pacman keyring works without complaint and installing archlinux keyring (with package signatures off) also works fine. is there a direct gpg command i can use to verify a package signature in the same way pacman does, to see if that sheds any light on what the issue might be?. Reading through the script, how about `type a gpg` and `gpg version`? it looks like it uses gpg to create that file before it chmods it. Alternate public pgp key servers that support access via hkp (like sks keyservers used to): keys.openpgp.org (based on hagrid) keyserver.ubuntu (based on hockeypuck) keys.mailvelope (based on mailvelope) access via other protocols that are supported by gnupg: ldap: keyserver.pgp (based on broadcom pgp universal server) due to the fact that the sks key servers were taken down due to. From my understanding the keyserver options auto key retrieve should tell gpg to automatically download the public key from the keyserver to verify the iso, but i don't know why it is not doing this?. 13 i can't decrypt my passwords with pass neither with gpg directly. gpg: encrypted with rsa4096 key, id id, created creation date "name