
Dsa Lecture 13 Hash Tables Pdf Password Algorithms And Data Has detailed articles on hash tables and cryptographic hash functions. what are you looking for that isn't in those?. The main difference between hash functions and pseudorandom number generators is that a hash function gives a unique value for each input. this is important for applications such as hash tables and message verification: in hash tables, a hash function is used to choose the location at which an input is put.
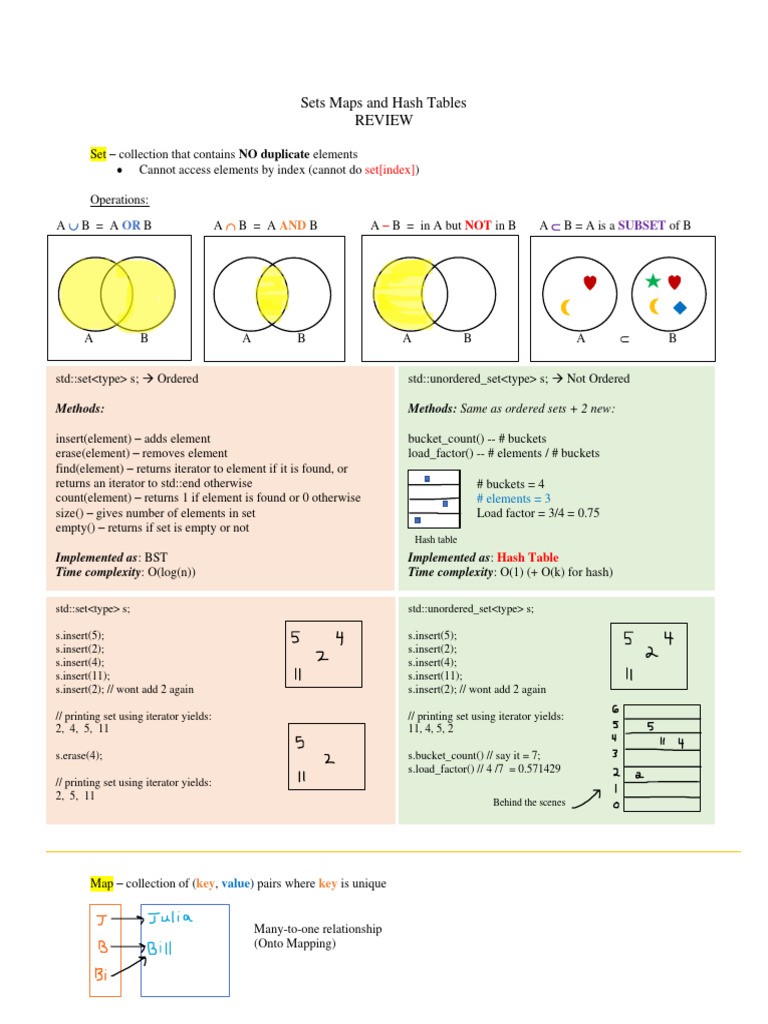
Sets Maps And Hash Tables Review Pdf Computer Science Computer Data This is possible in practice if the hash function includes a random factor which is based on a secret seed. you could use a hash function that uses actual randomness and a lookup table for reproducibility to satisfy the definition with high probability for any input set (if you assume "equal number" means "approximately equal"). Given an open address hash table with α α < 1, the expected number of probes in a successful search is at most 1 αln 1 1−α 1 α ln 1 1 α i read this in a book and the proof starts by saying searching for k follows the same probe sequence as inserting it. if k k is the i 1 i 1 th key inserted into the table, then 1 1− i m 1 1 m is the maximum expected number of probes for the. 由于他的调皮,导致客户挑妹纸的时间大幅延长,从10秒到了800秒。 在代码中,一般都有一些比较复杂的算法去运算而得出这个hash值,一旦破解了这个算法,就又可以调皮啦。 在java中,hash算法在hashmap中有体现,有兴趣的可以去看看源码。. I am reading the "introduction to algorithms" by thomas cormen et al. particularly the theorem which says that given an open address hash table with load factor $\\alpha = n m < 1$, the expected.

Sets Maps And Hash Tables Review Pdf Sets Maps And Hash Tables Review 由于他的调皮,导致客户挑妹纸的时间大幅延长,从10秒到了800秒。 在代码中,一般都有一些比较复杂的算法去运算而得出这个hash值,一旦破解了这个算法,就又可以调皮啦。 在java中,hash算法在hashmap中有体现,有兴趣的可以去看看源码。. I am reading the "introduction to algorithms" by thomas cormen et al. particularly the theorem which says that given an open address hash table with load factor $\\alpha = n m < 1$, the expected. The birthday attack applies to any hash function, regardless of its structure, and also to hi h i. for your first question, here is a possible hint. note that if we can find a collision in hi h i then we can find a collision in h0 h 0 (by considering the top most h0 h 0, for instance). if we can find a collision in h0 h 0 then, we can find a collision for hi h i (by replacing one of the inner. For example, suppose we wish to allocate a hash table, with collisions resolved by chaining, to hold roughly n = 2000 n = 2000 character strings, where a character has 8 bits. we don't mind examining an average of 3 elements in an unsuccesful search, so we allocate a table of size m = 701 m = 701. 6 hash tables resolve collisions through two mechanisms, separate chaining or open hashing and open addressing or closed hashing. though the first method uses lists (or other fancier data structure) in hash table to maintain more than one entry having same hash values, the other uses complex ways of skipping n elements on collsion. Speed of calculating the hash function of large keys: you don't actually have to process the whole key. for example if the key is a string, you might process only the first and last 40 characters to calculate the hash function. the biggest advantage of hashing vs. binary search is that it is much cheaper to add or remove an item from a hash table, compared to adding or removing an item to a.

Lecture 7 Hash Tables Pdf Dsa1002 Data Structures And Algorithms The birthday attack applies to any hash function, regardless of its structure, and also to hi h i. for your first question, here is a possible hint. note that if we can find a collision in hi h i then we can find a collision in h0 h 0 (by considering the top most h0 h 0, for instance). if we can find a collision in h0 h 0 then, we can find a collision for hi h i (by replacing one of the inner. For example, suppose we wish to allocate a hash table, with collisions resolved by chaining, to hold roughly n = 2000 n = 2000 character strings, where a character has 8 bits. we don't mind examining an average of 3 elements in an unsuccesful search, so we allocate a table of size m = 701 m = 701. 6 hash tables resolve collisions through two mechanisms, separate chaining or open hashing and open addressing or closed hashing. though the first method uses lists (or other fancier data structure) in hash table to maintain more than one entry having same hash values, the other uses complex ways of skipping n elements on collsion. Speed of calculating the hash function of large keys: you don't actually have to process the whole key. for example if the key is a string, you might process only the first and last 40 characters to calculate the hash function. the biggest advantage of hashing vs. binary search is that it is much cheaper to add or remove an item from a hash table, compared to adding or removing an item to a.
Core Hash Tables Hash Maps And Edit Distance Coursera 6 hash tables resolve collisions through two mechanisms, separate chaining or open hashing and open addressing or closed hashing. though the first method uses lists (or other fancier data structure) in hash table to maintain more than one entry having same hash values, the other uses complex ways of skipping n elements on collsion. Speed of calculating the hash function of large keys: you don't actually have to process the whole key. for example if the key is a string, you might process only the first and last 40 characters to calculate the hash function. the biggest advantage of hashing vs. binary search is that it is much cheaper to add or remove an item from a hash table, compared to adding or removing an item to a.