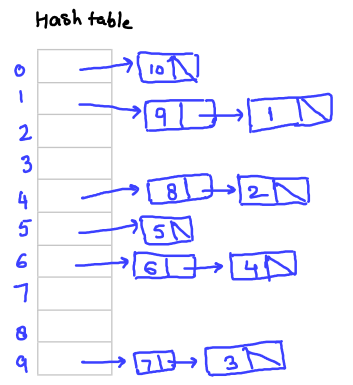
Separate Chaining Hashing Collision Handling Technique Ritambhara Hashing is the process of converting data — text, numbers, files, or anything, really — into a fixed length string of letters and numbers. data is converted into these fixed length strings, or hash values, by using a special algorithm called a hash function. Hashing is a technique used in data structures that efficiently stores and retrieves data in a way that allows for quick access. hashing involves mapping data to a specific index in a hash table (an array of items) using a hash function.

Separate Chaining Hashing Collision Handling Technique Ritambhara Hashing is a computationally and storage space efficient form of data access that avoids the non constant access time of ordered and unordered lists and structured trees, and the often exponential storage requirements of direct access of state spaces of large or variable length keys. Hashing is a one way process that turns data into a fixed length hash value using a hash function. the primary goal of hashing is to ensure data integrity and validate the original data. Hashing is a one way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. in the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure. Hashing means using some function or algorithm to map object data to some representative integer value. this so called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map.

Solution Hashing Techniques Collision Handling Techniques Open Hashing Hashing is a one way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. in the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure. Hashing means using some function or algorithm to map object data to some representative integer value. this so called hash code (or simply hash) can then be used as a way to narrow down our search when looking for the item in the map. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. unlike standard encryption, hashing is always used for one way encryption, and hashed values are very difficult to decode. In this tutorial, we’ll discuss hashing and its application areas in detail. first, we’ll discuss the core concepts and principles of hashing. second, we’ll analyze cryptographic hash functions. then, we’ll define a few hashing algorithms and possible attacks on them. finally, we’ll look over common hash based data structures. 2. hashing. 2.1. Hashing technology plays a crucial role in ensuring the integrity and authenticity of digital data. by generating unique hash values for each document or piece of evidence, hashing facilitates accurate verification, minimizing the risk of tampering or unauthorized modifications. While it might sound complex, hashing is simply a way of converting data into a fixed size string that acts like a digital fingerprint. in this guide, you’ll learn the hashing meaning, how it compares to encryption, key hashing algorithms, and how businesses use hashing to secure data.
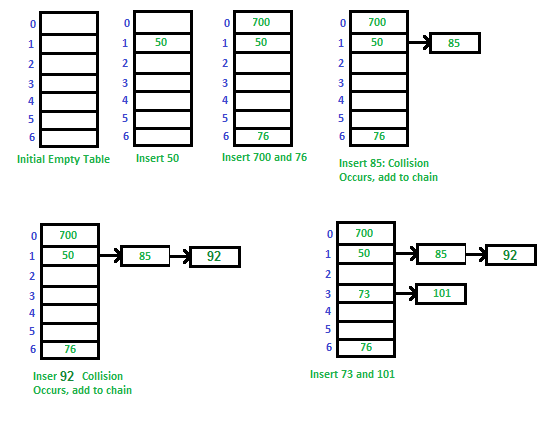
Separate Chaining Collision Handling Technique In Hashing Geeksforgeeks Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. unlike standard encryption, hashing is always used for one way encryption, and hashed values are very difficult to decode. In this tutorial, we’ll discuss hashing and its application areas in detail. first, we’ll discuss the core concepts and principles of hashing. second, we’ll analyze cryptographic hash functions. then, we’ll define a few hashing algorithms and possible attacks on them. finally, we’ll look over common hash based data structures. 2. hashing. 2.1. Hashing technology plays a crucial role in ensuring the integrity and authenticity of digital data. by generating unique hash values for each document or piece of evidence, hashing facilitates accurate verification, minimizing the risk of tampering or unauthorized modifications. While it might sound complex, hashing is simply a way of converting data into a fixed size string that acts like a digital fingerprint. in this guide, you’ll learn the hashing meaning, how it compares to encryption, key hashing algorithms, and how businesses use hashing to secure data.

Solved Using Division Hashing Technique If A Collision Occurs Solve Hashing technology plays a crucial role in ensuring the integrity and authenticity of digital data. by generating unique hash values for each document or piece of evidence, hashing facilitates accurate verification, minimizing the risk of tampering or unauthorized modifications. While it might sound complex, hashing is simply a way of converting data into a fixed size string that acts like a digital fingerprint. in this guide, you’ll learn the hashing meaning, how it compares to encryption, key hashing algorithms, and how businesses use hashing to secure data.