
How Cryptographic Algorithms And Hashing Secure Blockchains Coincentral Cryptography algorithms are at the very heart of blockchain technology. this guide will explain everything you need to know about how they work. Cryptography is used to encrypt messages in a p2p network and hashing is used to secure the block information and the link blocks in a blockchain. cryptography primarily focuses on ensuring the security of participants, transactions, and safeguards against double spending.

How Cryptographic Algorithms And Hashing Secure Blockchains Coincentral Cryptographic methods, consensus algorithms, and distributed ledger systems are blockchain security mechanisms that maintain data integrity, confidentiality, and immutability. blockchain vulnerabilities, such as 51% attacks and phishing scams, pose significant risks to decentralized networks. Discover how hashing ensures data integrity and security in blockchain. learn its role in transactions, block formation, smart contracts, and more. Cryptographic hashing has been an integral part of the cybersecurity spectrum. in fact, it is widely used in different technologies including bitcoin and other cryptocurrency protocols. in this article, we will go through hashing in cryptocurrency where we learn about cryptographic hashes, their examples, history, and so on. Various cryptographic algorithms, including public key cryptography and hashing functions, are used to secure blockchain systems and promote trustless transactions. in this blog, we’ll explore the types of cryptography used in blockchain and the key algorithms that keep networks secure and decentralized.

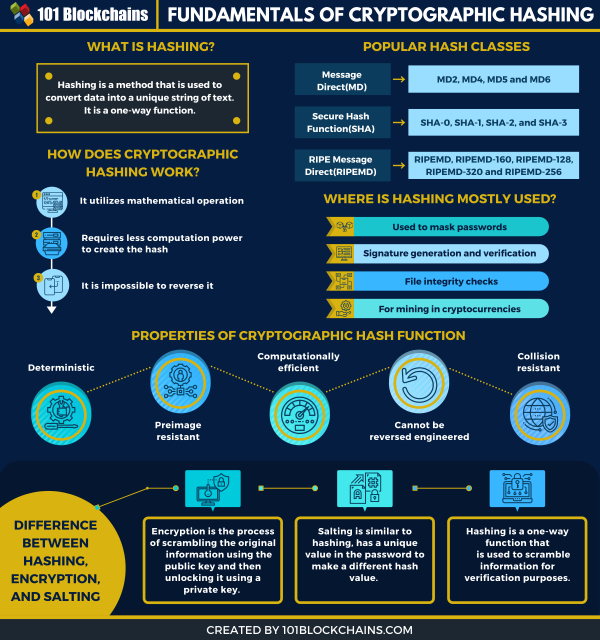
How Cryptographic Algorithms And Hashing Secure Blockchains Coincentral Cryptographic hashing has been an integral part of the cybersecurity spectrum. in fact, it is widely used in different technologies including bitcoin and other cryptocurrency protocols. in this article, we will go through hashing in cryptocurrency where we learn about cryptographic hashes, their examples, history, and so on. Various cryptographic algorithms, including public key cryptography and hashing functions, are used to secure blockchain systems and promote trustless transactions. in this blog, we’ll explore the types of cryptography used in blockchain and the key algorithms that keep networks secure and decentralized. To guarantee data safety and confidentiality, blockchain cryptography operates the following elements: hashes, digital signatures, and keys. hash. hashing operates on unlimited input data by guaranteeing flexibility when transforming them into output data. Cryptographic hashing is a process of creating a fixed size hash value from a variable size input message. the hash value, also known as a digest, is unique to the input message and can be used. In this article, sarah rothrie explores a brief history of cryptography, how it applies to blockchain, and why hashing is necessary for the integrity of the chain. Hash functions are a crucial component of the blockchain's underlying data structure, guaranteeing both its scalability and security. the blockchain's security may be assessed by analyzing the hash functions it employs in light of several security criteria.

How Cryptographic Algorithms And Hashing Secure Blockchains Coincentral To guarantee data safety and confidentiality, blockchain cryptography operates the following elements: hashes, digital signatures, and keys. hash. hashing operates on unlimited input data by guaranteeing flexibility when transforming them into output data. Cryptographic hashing is a process of creating a fixed size hash value from a variable size input message. the hash value, also known as a digest, is unique to the input message and can be used. In this article, sarah rothrie explores a brief history of cryptography, how it applies to blockchain, and why hashing is necessary for the integrity of the chain. Hash functions are a crucial component of the blockchain's underlying data structure, guaranteeing both its scalability and security. the blockchain's security may be assessed by analyzing the hash functions it employs in light of several security criteria.

The Importance Of Cryptographic Hashing Algorithms In this article, sarah rothrie explores a brief history of cryptography, how it applies to blockchain, and why hashing is necessary for the integrity of the chain. Hash functions are a crucial component of the blockchain's underlying data structure, guaranteeing both its scalability and security. the blockchain's security may be assessed by analyzing the hash functions it employs in light of several security criteria.
Cryptographic Hashing A Beginner S Guide 101 Blockchains