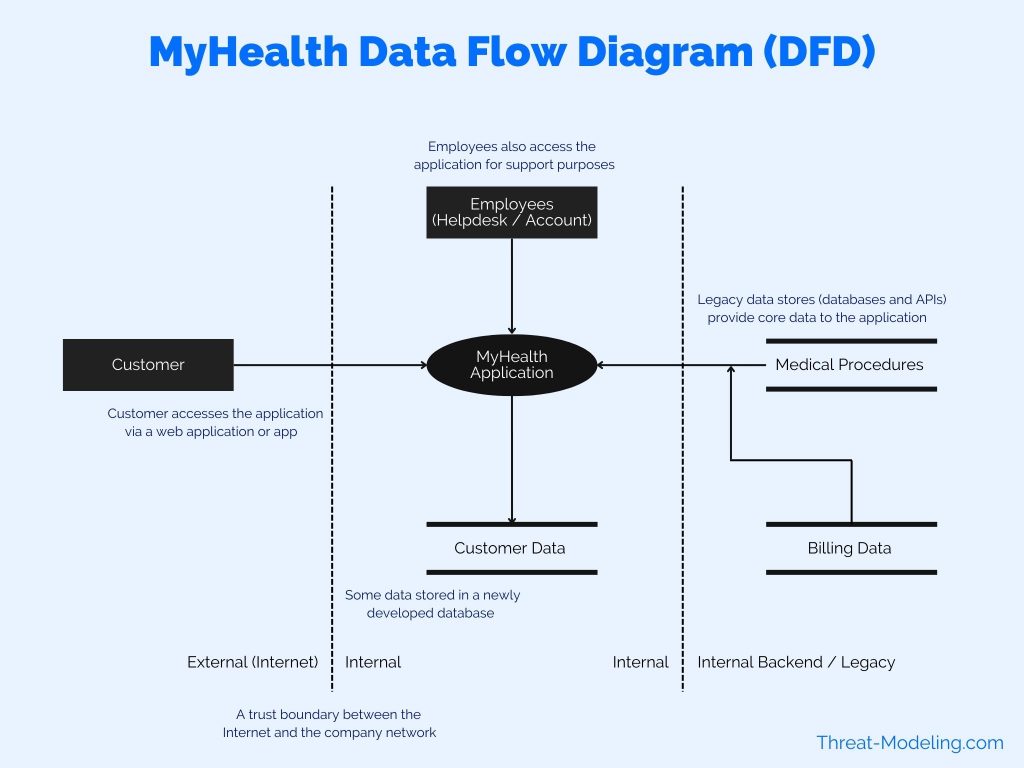
How To Use Data Flow Diagrams In Threat Modeling Threat Modeling Data flow diagrams provide readers and threat modelers with a simple technical diagram, to depict flows of data and interactions between key components of an application or it system. Data flow diagrams are graphical representations of your system and should specify each element, their interactions, and helpful context. in this module, you learn how to: distinguish between the shape and function of each element. include the right context for an element when creating a data flow diagram.

How To Use Data Flow Diagrams In Threat Modeling Threat Modeling Although different techniques may be used in this first step of threat modeling, data flow diagrams (dfds) are arguably the most common approach. dfds allow one to visually model a system and its interactions with data and other entities; they are created using a small number of simple symbols. Data flow diagrams (dfds) are frequently used to show what we’re working on. the dfds show the different paths through the system, highlighting the privilege or trust boundaries. It can be done in two ways: data flow diagram: it helps in showing how the flow of data occurs in the system. process flow diagram: it helps in finding the process of the system that from where users interact in the system, and how the system works internally. 3. threat identification. Data flow diagrams are visual representations used to document the flow of data through a system. in the context of threat modeling, dfds help teams understand and map attack surfaces by visually representing system components, data flows, and trust boundaries. sources: course materials bctl l0 dfd.json 14 712.
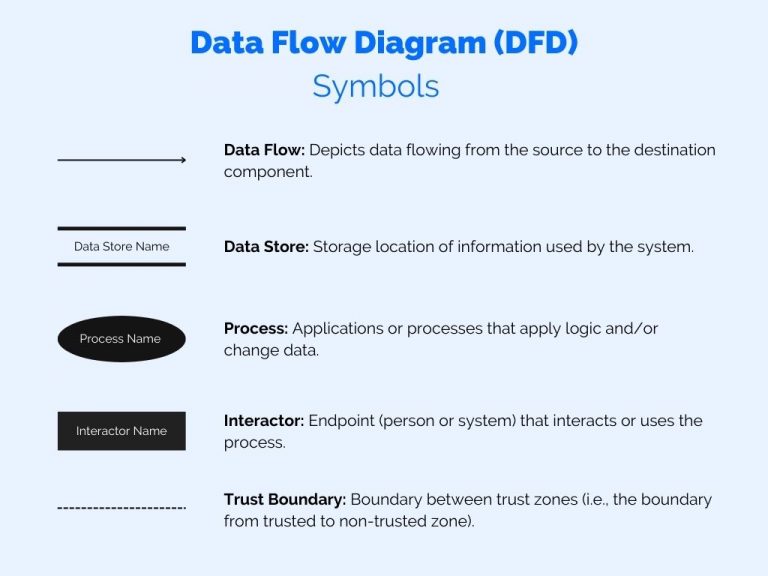
How To Use Data Flow Diagrams In Threat Modeling Threat Modeling It can be done in two ways: data flow diagram: it helps in showing how the flow of data occurs in the system. process flow diagram: it helps in finding the process of the system that from where users interact in the system, and how the system works internally. 3. threat identification. Data flow diagrams are visual representations used to document the flow of data through a system. in the context of threat modeling, dfds help teams understand and map attack surfaces by visually representing system components, data flows, and trust boundaries. sources: course materials bctl l0 dfd.json 14 712. Threat modeling using data flow diagrams (dfds) is a powerful method that helps to achieve robust defenses against threats. this blog will guide you through the process of creating dfds for threat modeling by enabling you to visualize and address potential vulnerabilities in your system’s data flow. In this longest episode of the world's shortest threat modeling videos, i introduce the five. Operational or infrastructure threat models (otms) are a specific type of data flow diagram, visualising how the independent, grouped, and shared components communicate with each other and external entities via connection pathways. these are used by agile teams to build application threat models (atms). Learn to leverage data flow diagrams for effective threat modeling. secure your application development process with security compass.
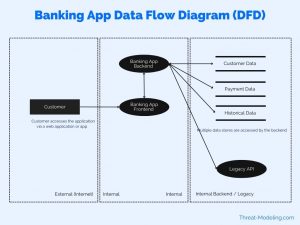
How To Use Data Flow Diagrams In Threat Modeling Threat Modeling Threat modeling using data flow diagrams (dfds) is a powerful method that helps to achieve robust defenses against threats. this blog will guide you through the process of creating dfds for threat modeling by enabling you to visualize and address potential vulnerabilities in your system’s data flow. In this longest episode of the world's shortest threat modeling videos, i introduce the five. Operational or infrastructure threat models (otms) are a specific type of data flow diagram, visualising how the independent, grouped, and shared components communicate with each other and external entities via connection pathways. these are used by agile teams to build application threat models (atms). Learn to leverage data flow diagrams for effective threat modeling. secure your application development process with security compass.