
Known Threat Modeling Tooling Techniques Tooling Threat Modeling You can identify your protection needs, analyze possible threats and calculate the resulting risks. the underlying assessment model and calculation logic are highly customizable and can be integrated into existing toolchains. cybersage inc. Find a tool that supports various threat modeling methodologies, such as stride or capec, to tailor your approach to different projects or organizational requirements. choose a tool that integrates seamlessly with your existing devsecops tools and workflows.
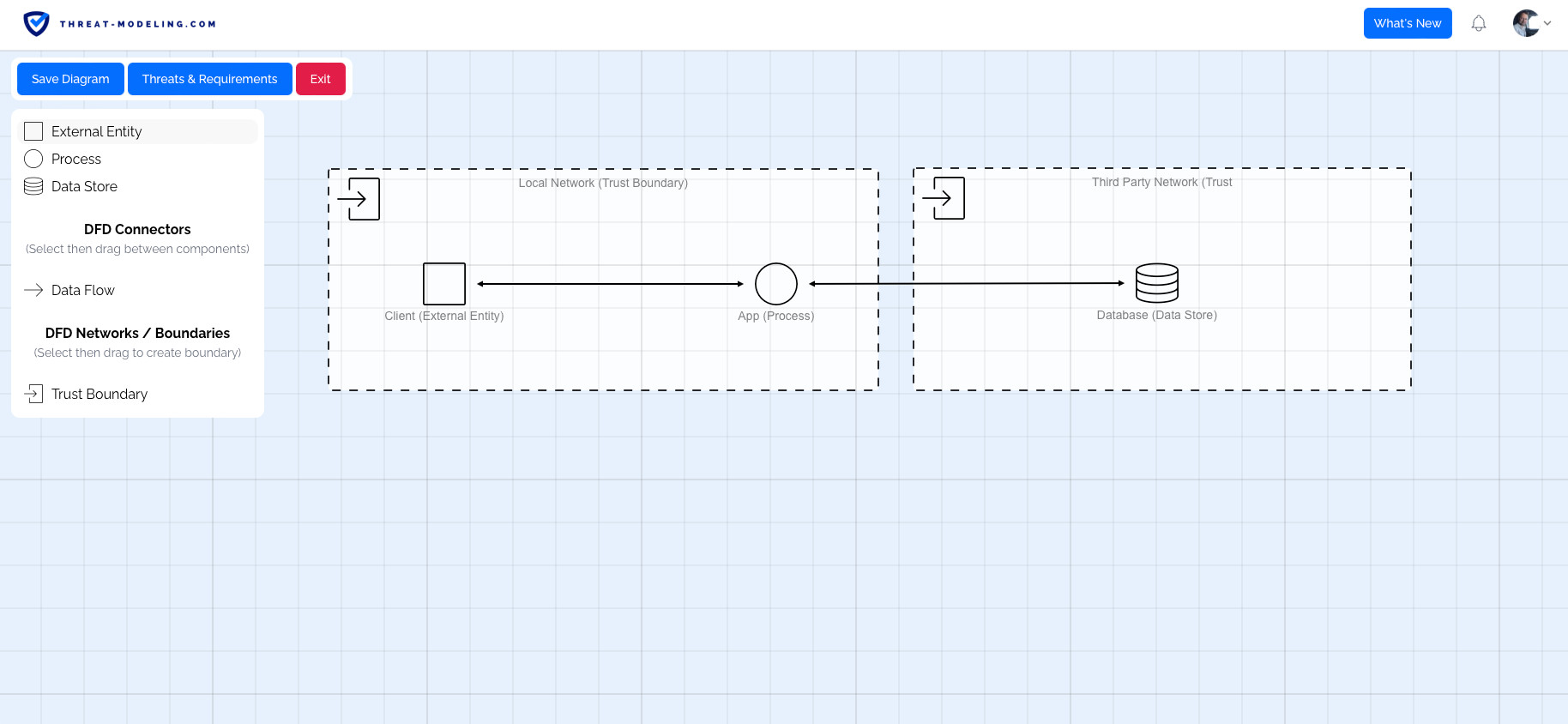
Threat Modeling Tool Threat Modeling Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as well as those that may cripple mitigations and countermeasures. threat modeling ranges from simple flow diagrams to highly complex mathematical algorithms and frameworks. Threat modeling assists threat intelligence analysts in identifying, categorizing, and prioritizing threats in order to guarantee successful recording and reporting, which is the overarching goal of a threat intelligence program. Threat modeling, a systematic approach to identifying and mitigating potential security risks, is an essential component of your toolkit. to help you stand out in your role, we’ve compiled a. Threat modelling techniques map the flow of data within your network and the different stages of a prospective cyber attack. the most popular threat modelling techniques are data flow diagrams and attack trees.
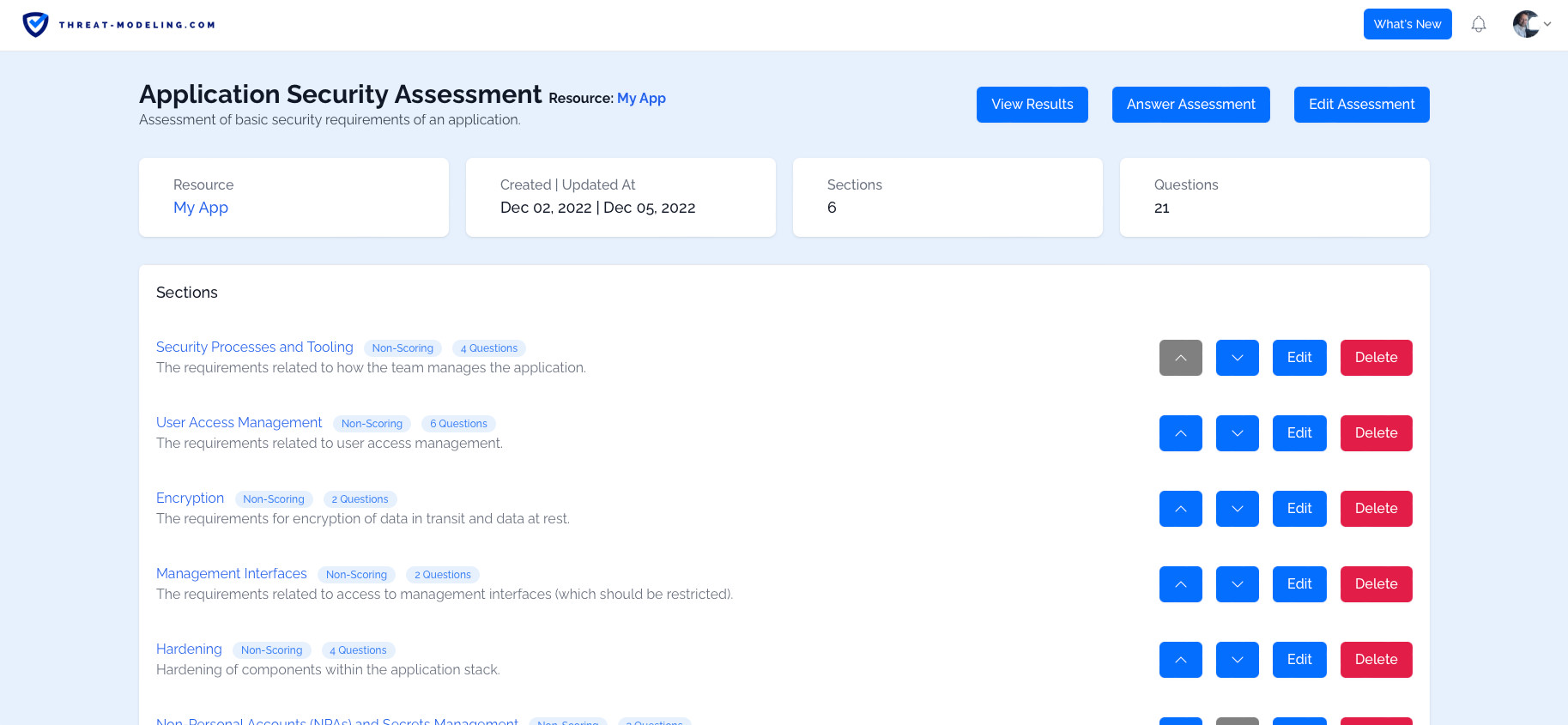
Threat Modeling Tool Threat Modeling Threat modeling, a systematic approach to identifying and mitigating potential security risks, is an essential component of your toolkit. to help you stand out in your role, we’ve compiled a. Threat modelling techniques map the flow of data within your network and the different stages of a prospective cyber attack. the most popular threat modelling techniques are data flow diagrams and attack trees. Inspired by these commonalities and guided by the four key questions of threat modeling discussed above, this cheatsheet will break the threat modeling down into four basic steps: application decomposition, threat identification and ranking, mitigations, and review and validation. To achieve this, threat modeling methodologies are employed to identify and analyze potential threats that could harm the system, network, or organization. A typical threat modeling process includes five steps: threat intelligence, asset identification, mitigation capabilities, risk assessment, and threat mapping. each of these provides different insights and visibility into the organization’s security posture. Discover what threat modeling is, why it matters in cybersecurity, key methodologies, step by step processes, and the best tools for secure software development.

Threat Modeling Tool Threat Modeling Inspired by these commonalities and guided by the four key questions of threat modeling discussed above, this cheatsheet will break the threat modeling down into four basic steps: application decomposition, threat identification and ranking, mitigations, and review and validation. To achieve this, threat modeling methodologies are employed to identify and analyze potential threats that could harm the system, network, or organization. A typical threat modeling process includes five steps: threat intelligence, asset identification, mitigation capabilities, risk assessment, and threat mapping. each of these provides different insights and visibility into the organization’s security posture. Discover what threat modeling is, why it matters in cybersecurity, key methodologies, step by step processes, and the best tools for secure software development.
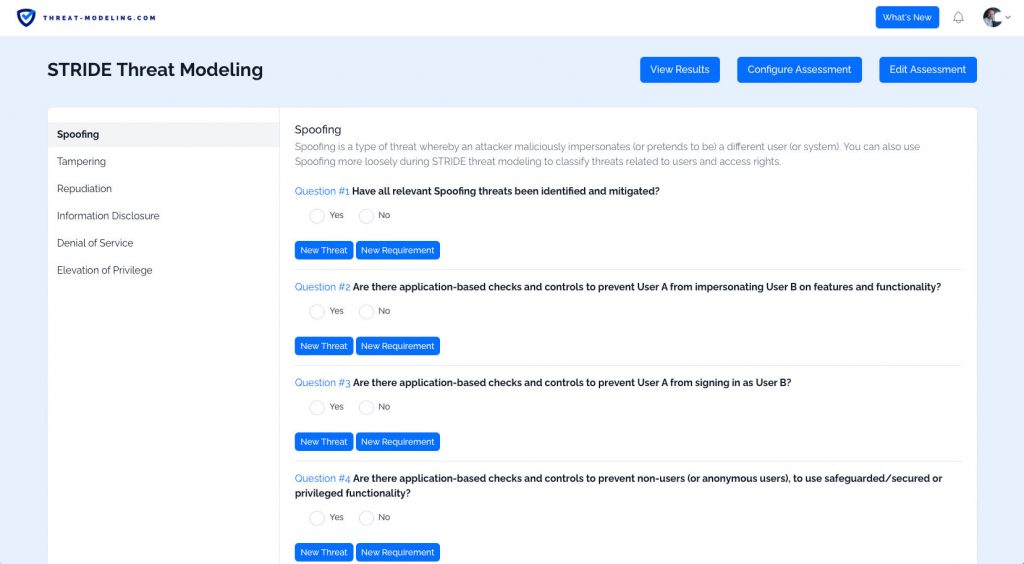
Threat Modeling Threat Modeling A typical threat modeling process includes five steps: threat intelligence, asset identification, mitigation capabilities, risk assessment, and threat mapping. each of these provides different insights and visibility into the organization’s security posture. Discover what threat modeling is, why it matters in cybersecurity, key methodologies, step by step processes, and the best tools for secure software development.