
Sample Data Flow Diagram Using Threat Modeling Tool Download Data flow diagrams are graphical representations of your system and should specify each element, their interactions, and helpful context. In this article, i describe how to use data flow diagrams in threat modeling, including the symbols used, and how to use them step by step.

Sample Data Flow Diagram Using Threat Modeling Tool Download Ready to elevate your security analysis? transform your threat modeling practice with our template, built on years of real world security consulting experience. get started with professional grade security documentation that speaks the language of both technical teams and stakeholders. Threat dragon is a tool that can help development teams with their threat modeling process. it provides for creating and modifying data flow diagrams which provide the context and direction for the threat modeling activities. It's available as a free download from the microsoft download center. this latest release simplifies working with threats and provides a new editor for defining your own threats. We show how the formal modeling language altarica, primarily dedicated to safety analyses, can assess this illustrative example by representing the system and automatically extracting sequences.
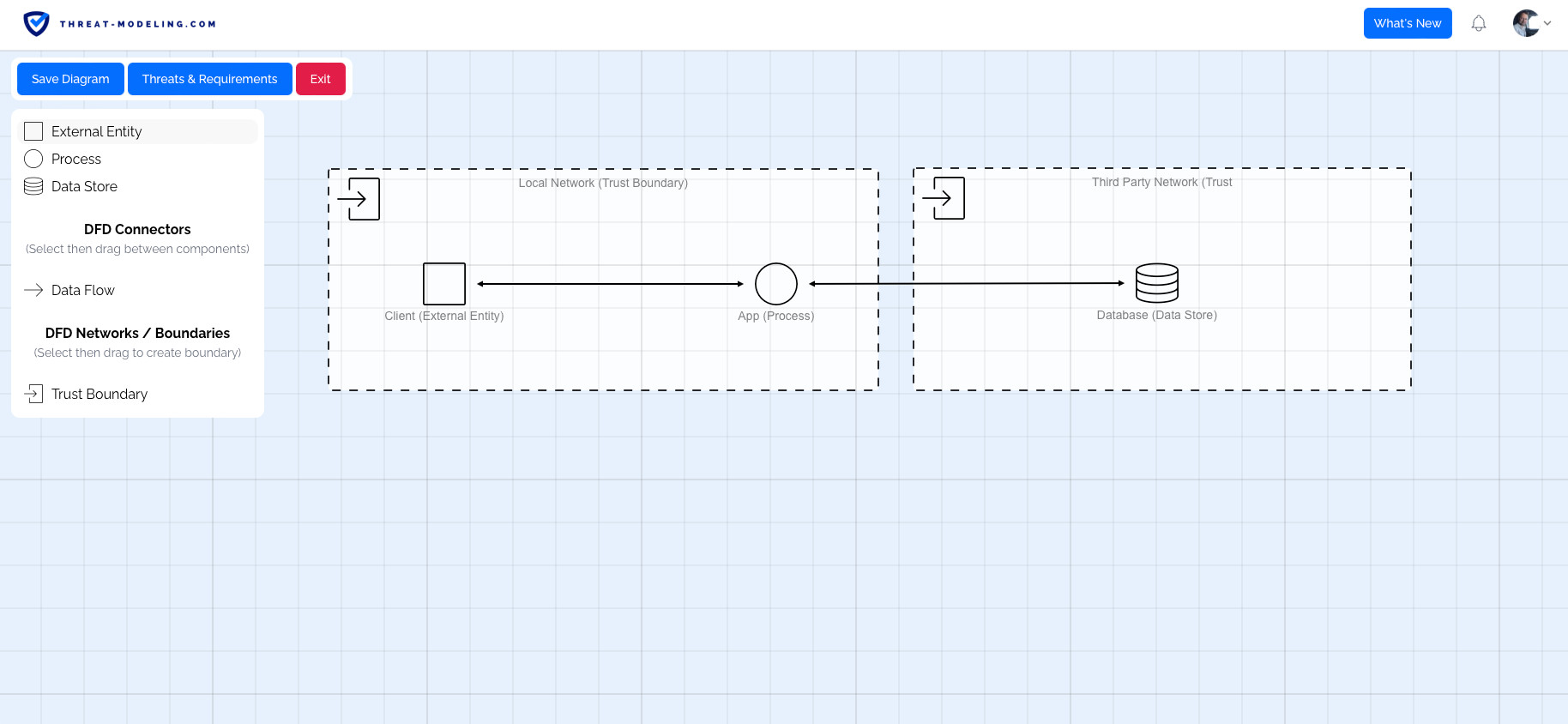
Threat Modeling Tool Threat Modeling It's available as a free download from the microsoft download center. this latest release simplifies working with threats and provides a new editor for defining your own threats. We show how the formal modeling language altarica, primarily dedicated to safety analyses, can assess this illustrative example by representing the system and automatically extracting sequences. The document introduces the microsoft threat modeling tool and how to use it. it explains how to build a model using the tool by drawing a data flow diagram and trust boundaries. You can download the microsoft threat modeling tool 2016 for free from the microsoft website. just search for "microsoft threat modeling tool 2016" and follow the instructions to download and install the tool. This article takes you through the process of getting started with the microsoft sdl threat modeling approach and shows you how to use the tool to develop great threat models as a backbone of your security process.
Threat Modeling Tool Threat Modeling The document introduces the microsoft threat modeling tool and how to use it. it explains how to build a model using the tool by drawing a data flow diagram and trust boundaries. You can download the microsoft threat modeling tool 2016 for free from the microsoft website. just search for "microsoft threat modeling tool 2016" and follow the instructions to download and install the tool. This article takes you through the process of getting started with the microsoft sdl threat modeling approach and shows you how to use the tool to develop great threat models as a backbone of your security process.
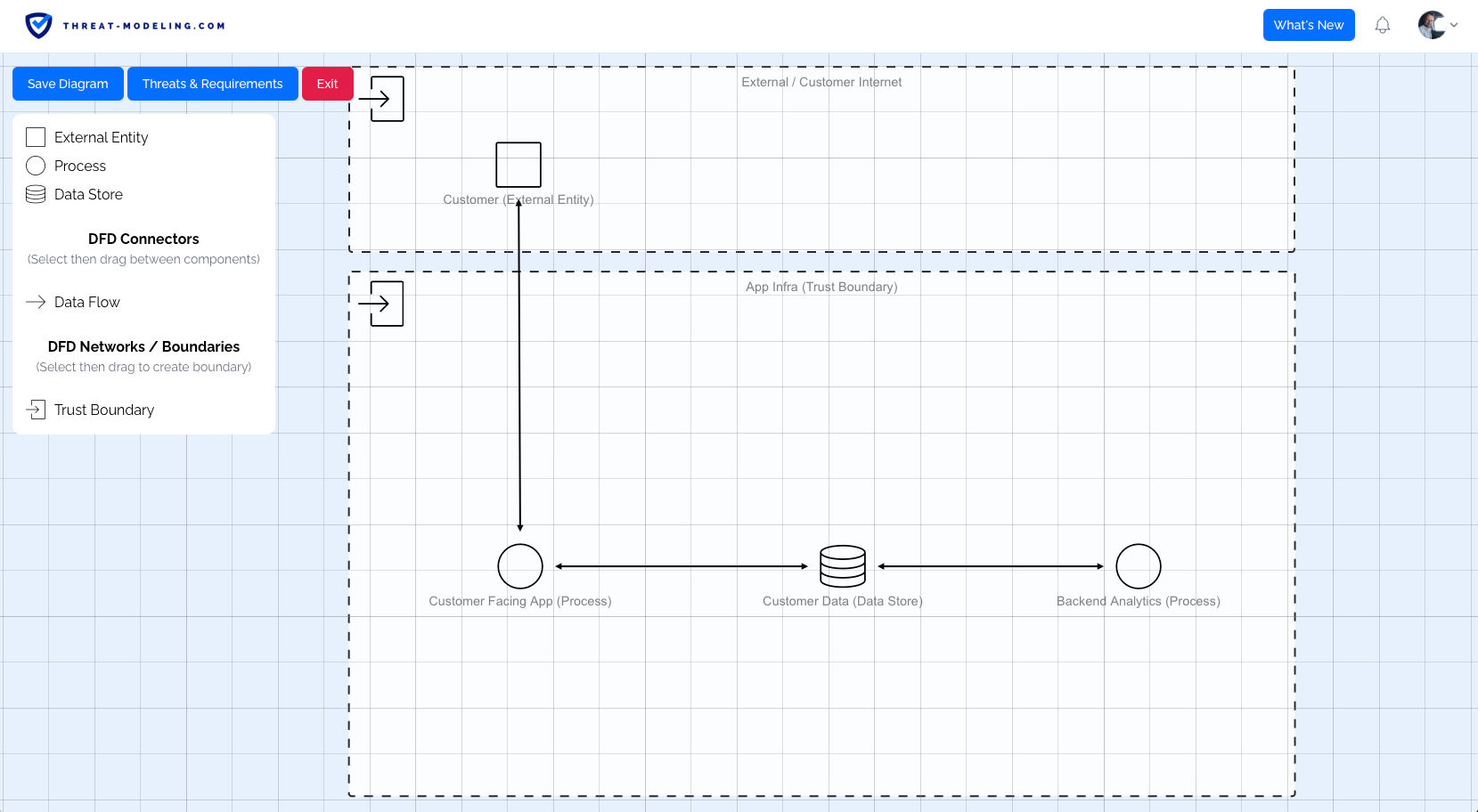
Threat Modeling With Stride Using A Threat Modeling Tool Threat This article takes you through the process of getting started with the microsoft sdl threat modeling approach and shows you how to use the tool to develop great threat models as a backbone of your security process.