
It S Not Just You Avoiding Third Party Security Vulnerabilities Comptia security is the premier global certification that establishes the essential skills required for core security functions and a career in it security. it showcases professionals' capabilities in securing networks, applications, and devices, ensuring data integrity, confidentiality, and availability. At the first city council meeting of each month a deputy will present a public safety topic and information on how to keep your family safe. below are the topics for each month with some information regarding that topic. minnesota auto theft prevention program.

Squashing Third Party Security Vulnerabilities Coveros Security is protection from, or resilience against, potential harm (or other unwanted coercion). beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. U.s. department of homeland security: with honor and integrity, we will safeguard the american people, our homeland, and our values. Deputies perform a broad range of activities, which include investigating crimes such as disturbances, domestic violence incidents, suspicious activities, traffic enforcement, medical emergencies, motor vehicles crashes, and other calls for service. : measures taken to guard against espionage or sabotage, crime, attack, or escape. according to a media release, the investments are going to community partners helping parents, families and individuals in need … and assisting with housing security … health & beauty close up. we must insure our national security.

Third Party Vulnerabilities Demystifying The Unknown Infosecurity Deputies perform a broad range of activities, which include investigating crimes such as disturbances, domestic violence incidents, suspicious activities, traffic enforcement, medical emergencies, motor vehicles crashes, and other calls for service. : measures taken to guard against espionage or sabotage, crime, attack, or escape. according to a media release, the investments are going to community partners helping parents, families and individuals in need … and assisting with housing security … health & beauty close up. we must insure our national security. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. the goal of it security is to protect these assets, devices and services from being disrupted, stolen or exploited by unauthorized users, otherwise known as threat actors. We must insure our national security. the college failed to provide adequate security on campus after dark. there was a lapse in security and the inmates escaped. we have to go through security at the airport. we called security when we found the door open. the meeting was held under tight security. 30 demonstrators were killed in clashes with the security forces over the weekend. the tighter security measures precautions include video cameras throughout the city centre. the students were deported because they posed a threat to national security. the banks must tighten security against fraud. Security refers to all the measures that are taken to protect a place, or to ensure that only people with permission enter it or leave it. they are now under a great deal of pressure to tighten their airport security. strict security measures are in force in the capital. a top security jail.
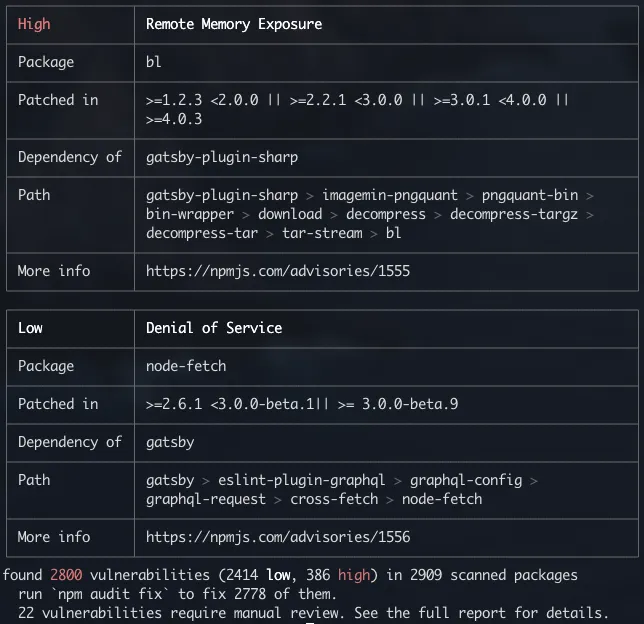
Ottofeller Security Concerns With Using Third Party Dependencies Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. the goal of it security is to protect these assets, devices and services from being disrupted, stolen or exploited by unauthorized users, otherwise known as threat actors. We must insure our national security. the college failed to provide adequate security on campus after dark. there was a lapse in security and the inmates escaped. we have to go through security at the airport. we called security when we found the door open. the meeting was held under tight security. 30 demonstrators were killed in clashes with the security forces over the weekend. the tighter security measures precautions include video cameras throughout the city centre. the students were deported because they posed a threat to national security. the banks must tighten security against fraud. Security refers to all the measures that are taken to protect a place, or to ensure that only people with permission enter it or leave it. they are now under a great deal of pressure to tighten their airport security. strict security measures are in force in the capital. a top security jail.
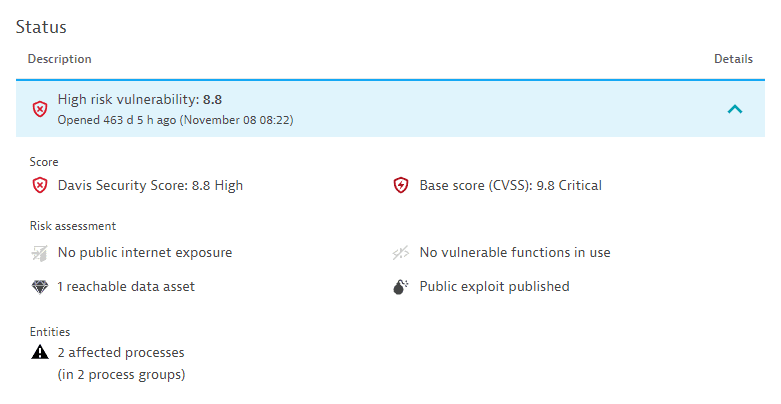
Manage Third Party Vulnerabilities Dynatrace Docs 30 demonstrators were killed in clashes with the security forces over the weekend. the tighter security measures precautions include video cameras throughout the city centre. the students were deported because they posed a threat to national security. the banks must tighten security against fraud. Security refers to all the measures that are taken to protect a place, or to ensure that only people with permission enter it or leave it. they are now under a great deal of pressure to tighten their airport security. strict security measures are in force in the capital. a top security jail.