
Should You Stop Using Vpn For Security Dev Community In an era where digital privacy seems like a distant dream, vpns have emerged as the knights in shining armor for many internet users. but do they truly live up to the hype? vpns can protect your privacy only if you use them right. checkout this video which explains. what vpns do ? what they don't ? how to stay yourself protected ?. Many privacy and security arguments for using a vpn no longer apply to ordinary users, some experts say, now that most websites have encryption built in.

Should You Stop Using Vpn For Security Dev Community If you are engaged in illegal activities espionage organised crime, hacktivism through a public network then a vpn alone likely isn't enough but if you are a nice law abiding citizen using the network legally then a vpn is safer and worth using. If you have one or more of those sites in your daily rotation, you should consider using your vpn to access them because it adds a much needed layer of security when viewing or using. Learn the risks of using vpns. understand their limitations, potential privacy issues, and why vpns aren't a one size fits all solution for security. If a vpn endpoint is only required temporarily (e.g. a service access point for a third party), you should disable vpn access on the server side, when no one needs to log in.
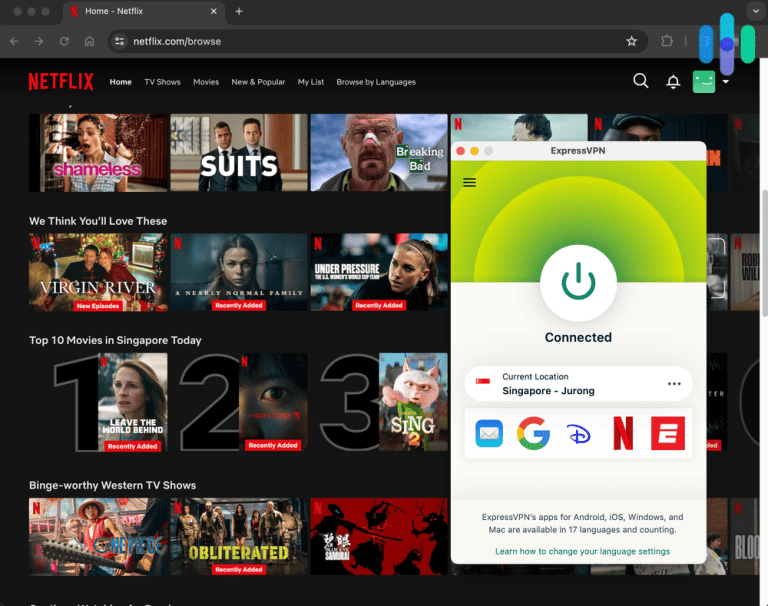
How To Disable A Vpn On Any Device Security Org Learn the risks of using vpns. understand their limitations, potential privacy issues, and why vpns aren't a one size fits all solution for security. If a vpn endpoint is only required temporarily (e.g. a service access point for a third party), you should disable vpn access on the server side, when no one needs to log in. Some reasons not to use a vpn include being blocked from certain websites, slower internet speeds, and violating censorship laws — but the best vpns can usually avoid these cons by providing top quality servers that are hard to detect and don't make a noticeable difference to your speed. If your internet provider is slowing your speed on certain websites, a vpn can hide your activity, letting you reclaim what you already paid for. and if you're working with sensitive material research, financial data, or legal documents it keeps your trail locked and your information safe. Vpns are often pitched as a one stop solution for protection on the internet. from privacy to security, and even access across geographical regions, it is true that the best vpn services can offer. When you setup the vpn, you and the vpn provider mutually agree on the encryption algorithm, hashing algorithm, and preshare keys (or certificates). this is so that when one side receives encrypted traffic, the other knows how to decrypt it.
Do Vpns Stop Or Prevent Ddos Attacks Security Org Some reasons not to use a vpn include being blocked from certain websites, slower internet speeds, and violating censorship laws — but the best vpns can usually avoid these cons by providing top quality servers that are hard to detect and don't make a noticeable difference to your speed. If your internet provider is slowing your speed on certain websites, a vpn can hide your activity, letting you reclaim what you already paid for. and if you're working with sensitive material research, financial data, or legal documents it keeps your trail locked and your information safe. Vpns are often pitched as a one stop solution for protection on the internet. from privacy to security, and even access across geographical regions, it is true that the best vpn services can offer. When you setup the vpn, you and the vpn provider mutually agree on the encryption algorithm, hashing algorithm, and preshare keys (or certificates). this is so that when one side receives encrypted traffic, the other knows how to decrypt it.
Is A Vpn Encrypted Does It Encrypt All Traffic Security Org Vpns are often pitched as a one stop solution for protection on the internet. from privacy to security, and even access across geographical regions, it is true that the best vpn services can offer. When you setup the vpn, you and the vpn provider mutually agree on the encryption algorithm, hashing algorithm, and preshare keys (or certificates). this is so that when one side receives encrypted traffic, the other knows how to decrypt it.

Stream 8 Security Threats Every Vpn User Should Be Aware Of By Spl Vpn