Pptp Vs L2tp Ipsec Vs Sstp Vs Ikev2 Vs Openvpn It Network Consulting In this article we explain some of the most common vpn protocols to help you better understanding how p2p tunnel protocols work. enjoy the nerd talk!. This article will delve deep into the following five popular vpn protocols: pptp, l2tp, sstp, ikev2, and openvpn, covering their functioning, use cases, pros, and cons.
Vpn Protocols Pptp Vs Sstp Vs L2tp Ipsec Vs Ipsec Ikev2 Vs Openvpn Vs Want to use a vpn? if you're looking for a vpn provider or setting up your own vpn, you'll need to choose a protocol. some vpn providers may even provide you with a choice of protocols. In this session we’ll compare common vpn protocols and explain pros and cons for each of them. before we dive into comparing the vpn protocols, let’s first understand there are two main categories of vpn implementations. Vpn protocols are sets of programs and processes that determine how that tunnel is actually formed. each one is a different solution to the problem of secure, private, and somewhat anonymous internet communication. There are three major vpn protocols that you’re likely to see offered by most providers: pptp, l2tp ipsec and openvpn. there is also one called sstp that hasn’t been adopted as widely as the other three.
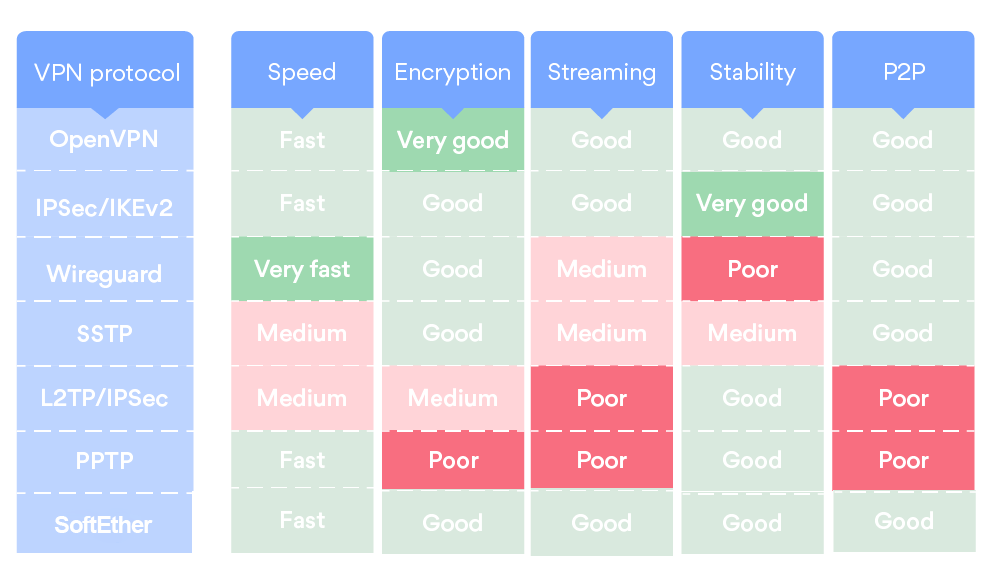
Vpn Protocols Pptp Vs Sstp Vs L2tp Ipsec Vs Ipsec Ikev2 Vs Openvpn Vs Vpn protocols are sets of programs and processes that determine how that tunnel is actually formed. each one is a different solution to the problem of secure, private, and somewhat anonymous internet communication. There are three major vpn protocols that you’re likely to see offered by most providers: pptp, l2tp ipsec and openvpn. there is also one called sstp that hasn’t been adopted as widely as the other three. Discover the different types of vpn protocols including ipsec, l2tp ipsec, pptp, and ssl vpn. learn how each vpn works, real time use cases, security comparisons, and which vpn is best for your needs. I wrote this article to help you understand the difference between vpn tunneling protocols, such as openvpn, ikev2, pptp, and others. In this complete vpn encryption guide, we take a detailed look at what encryption is, and how it is used in vpn connections. perhaps most importantly, we will explain the array of encryption terms used by vpn services. Well, the good news is, most vpn providers let you configure your app to use one of other protocols be it pptp, l2tp , sstp, ikev2, or openvpn. so, let’s find out what the pros and cons are for each vpn protocol and when to use them.

Vpn Protocol Comparison Pptp Vs Sstp Vs Openvpn Vs L2tp Vs Ikev2 Discover the different types of vpn protocols including ipsec, l2tp ipsec, pptp, and ssl vpn. learn how each vpn works, real time use cases, security comparisons, and which vpn is best for your needs. I wrote this article to help you understand the difference between vpn tunneling protocols, such as openvpn, ikev2, pptp, and others. In this complete vpn encryption guide, we take a detailed look at what encryption is, and how it is used in vpn connections. perhaps most importantly, we will explain the array of encryption terms used by vpn services. Well, the good news is, most vpn providers let you configure your app to use one of other protocols be it pptp, l2tp , sstp, ikev2, or openvpn. so, let’s find out what the pros and cons are for each vpn protocol and when to use them.

Vpn Protocol Comparison Pptp Vs Sstp Vs Openvpn Vs L2tp Vs Ikev2 In this complete vpn encryption guide, we take a detailed look at what encryption is, and how it is used in vpn connections. perhaps most importantly, we will explain the array of encryption terms used by vpn services. Well, the good news is, most vpn providers let you configure your app to use one of other protocols be it pptp, l2tp , sstp, ikev2, or openvpn. so, let’s find out what the pros and cons are for each vpn protocol and when to use them.