
The 9 Most Expensive Phishing Attacks In History Learn why holding down the ctrl key could compromise your network. uncover the latest phishing tactics and learn how to defend against them. Here’s what you need to look out for and what steps you can take to mitigate the risk of falling victim to these new 2sp cyber attacks, and why you shouldn’t hold down the ctrl key.
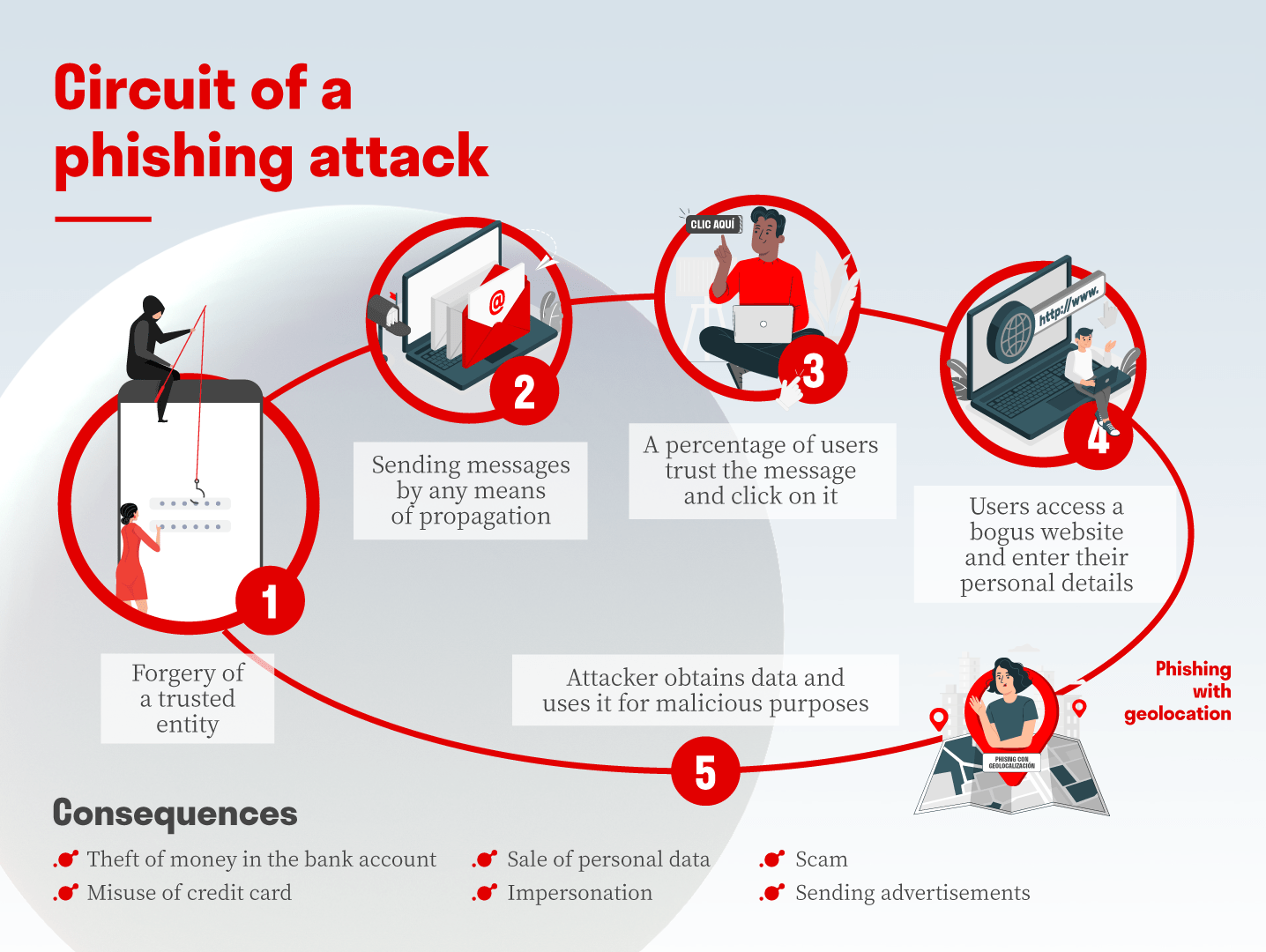
Phishing Attacks Hanley S Consulting Services A new form of phishing cyberattack has emerged, using a clever tactic involving the ctrl key to bypass automated security systems. These sophisticated attacks ask users to perform a seemingly innocent action—holding down the ctrl key—that cleverly evades automated security systems. this article unpacks the dangers of these attacks, their methodology, and how individuals and organizations can protect themselves. The security researchers have observed a dramatic increase in two step phishing attacks leveraging .vsdx files, targeting hundreds of organizations worldwide with a new layer of deception designed to evade detection and exploit user trust. Two step phishing attacks have, in the words of security researchers from perception point, “become a cornerstone of modern cybercrime,” leveraging trusted platforms “to deliver malicious content in layers to evade detection.”.

2 Step Phishing Attacks The Danger Of Holding Down The Ctrl Key The security researchers have observed a dramatic increase in two step phishing attacks leveraging .vsdx files, targeting hundreds of organizations worldwide with a new layer of deception designed to evade detection and exploit user trust. Two step phishing attacks have, in the words of security researchers from perception point, “become a cornerstone of modern cybercrime,” leveraging trusted platforms “to deliver malicious content in layers to evade detection.”. Do not and i mean do not hold down the control key. wondering what on earth i am talking about? well, let me break down this latest hack for you and explain why. attackers are increasingly using two step phishing attacks, with this one in particular using microsoft visio .vsdx format files to evade detection during credential stealing cyber. To make matters worse, victims are instructed to hold down the ctrl key while clicking on the embedded url, a subtle yet effective tactic designed to evade detection by email security scanners and automated tools. When this two step phishing campaign successfully exploits microsoft tools, the hacker not only gets the victim’s credentials but can also deliver additional malware for further attacks on your company’s assets. To activate the link in the visio file, users are prompted to hold down the ctrl key while clicking. this action bypasses automatic malware detection systems, allowing hackers to lead the victim to a fake microsoft 365 login page. the purpose is to steal credentials.

2 Step Phishing Attacks The Danger Of Holding Down The Ctrl Key Do not and i mean do not hold down the control key. wondering what on earth i am talking about? well, let me break down this latest hack for you and explain why. attackers are increasingly using two step phishing attacks, with this one in particular using microsoft visio .vsdx format files to evade detection during credential stealing cyber. To make matters worse, victims are instructed to hold down the ctrl key while clicking on the embedded url, a subtle yet effective tactic designed to evade detection by email security scanners and automated tools. When this two step phishing campaign successfully exploits microsoft tools, the hacker not only gets the victim’s credentials but can also deliver additional malware for further attacks on your company’s assets. To activate the link in the visio file, users are prompted to hold down the ctrl key while clicking. this action bypasses automatic malware detection systems, allowing hackers to lead the victim to a fake microsoft 365 login page. the purpose is to steal credentials.

New Warning Cyber Attacks Confirmed When Holding Down The Ctrl Key When this two step phishing campaign successfully exploits microsoft tools, the hacker not only gets the victim’s credentials but can also deliver additional malware for further attacks on your company’s assets. To activate the link in the visio file, users are prompted to hold down the ctrl key while clicking. this action bypasses automatic malware detection systems, allowing hackers to lead the victim to a fake microsoft 365 login page. the purpose is to steal credentials.