
A Puf Design For Secure Fpga Based Embedded Systems Pdf Field Physically unclonable functions (pufs) are circuits that compute a unique signature for a given ic based on the process variations inherent in the ic manufacturing process. this pa per presents the first puf design specifically targeted for field programmable gate arrays (fpgas). This document presents a new physically unclonable function (puf) design specifically targeted for field programmable gate arrays (fpgas). the proposed puf design leverages the underlying fpga architecture by using the inherent manufacturing variations between identical logic and routing circuits to generate a unique signature.

The Following Components Are Required For Proposed Fpga Based Embedded The concept of having an integrated circuit (ic) generate its own unique digital signature has broad application in areas such as embedded systems security, and. We compare various fpga based puf systems against one another to expose their unique advantages and disadvantages. this study provides system designers and security professionals with the crucial information they need to choose the best puf design for their particular applications. Physically unclonable functions (pufs) are circuits that compute a unique signature for a given ic based on the process variations inherent in the ic manufacturing process. this pa per presents. We propose a hardware software system design that ad dresses both sides of the instruction level security by incor porating physical unclonable function (puf) devices into the processor’s execution environment (see figure 1).

Pdf Successfully Designing Fpga Based Systems Pdfslide Net Physically unclonable functions (pufs) are circuits that compute a unique signature for a given ic based on the process variations inherent in the ic manufacturing process. this pa per presents. We propose a hardware software system design that ad dresses both sides of the instruction level security by incor porating physical unclonable function (puf) devices into the processor’s execution environment (see figure 1). Physically unclonable functions (pufs) are circuits that compute a unique signature for a given ic based on the process variations inherent in the ic manufacturing process. this pa per presents the first puf design specifically targeted for field programmable gate arrays (fpgas). We compare various fpga based puf systems against one another to expose their unique advantages and disadvantages. this study provides system designers and security professionals with. In this paper, we propose a novel low overhead hardware software co design solution that utilizes physical unclonable functions (pufs) to ensure the authenticity of program binaries for microprocessors microcontrollers mapped on the fpga. With this in mind, anderson described a puf design specifically tailored towards fpgas. in this paper we identify and analyse a flaw in said design which renders it impractical for security critical use. we describe two alternative solutions (relating to different trade offs) that eliminate this flaw. keywords fpga; puf i. introduction.
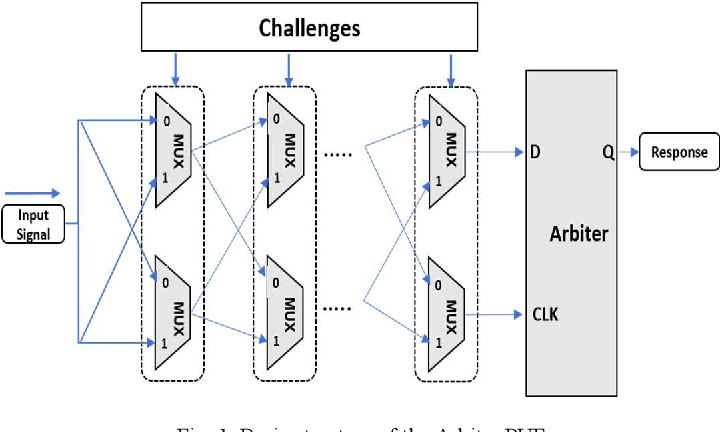
Figure 1 From Design Of A Delay Based Fpga Puf Resistant To Machine Physically unclonable functions (pufs) are circuits that compute a unique signature for a given ic based on the process variations inherent in the ic manufacturing process. this pa per presents the first puf design specifically targeted for field programmable gate arrays (fpgas). We compare various fpga based puf systems against one another to expose their unique advantages and disadvantages. this study provides system designers and security professionals with. In this paper, we propose a novel low overhead hardware software co design solution that utilizes physical unclonable functions (pufs) to ensure the authenticity of program binaries for microprocessors microcontrollers mapped on the fpga. With this in mind, anderson described a puf design specifically tailored towards fpgas. in this paper we identify and analyse a flaw in said design which renders it impractical for security critical use. we describe two alternative solutions (relating to different trade offs) that eliminate this flaw. keywords fpga; puf i. introduction.