
Differentiate Between Absolute Reference And Relative Reference With Rehydrate your cyber resilience with absolute security at black hat usa. restore compromised endpoints instantly!. Absolute gives it teams a live, tamper proof connection to every lenovo device, providing deep insights into software health, endpoint risks, and compliance gaps—helping organizations proactively manage security posture at scale.
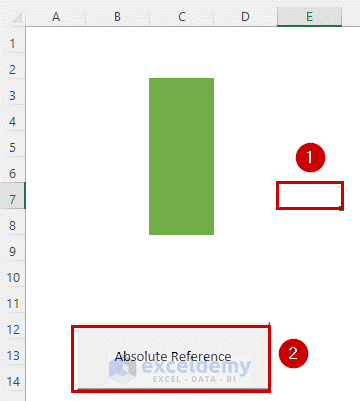
How To Use Relative Reference In Excel Macro With Easy Steps Add remove programs > absolute secure access > change > remove the warehouse component the configuration wizard will ask which warehouse to point the server to, use the fqdn of the new warehouse server. Seattle & las vegas — absolute security today announced that during consumer electronics show 2025 (ces 2025), it is offering consumers, students, and small business owners who purchase ai pcs a 50 percent discount on new one year subscriptions to absolute home & office, the industry’s leading security solution that protects pcs and data. Complemento absolute insights for endpoints identificar e responder às anomalias através de dashboards históricos personalizáveis obter insights sobre ativos e segurança em tempo real os profissionais de ti e segurança têm que gerenciar uma frota cada vez mais remota de dispositivos endpoint. 1993年に、教育分野のコンピューターを「追跡管理(track manage trace)」するプラットフォームのプロバイダーとして設立されたabsoluteは、真にインテリジェントな自動復活型セキュリティソリューションを提供する唯一のプロバイダーへと発展しました。.

How To Use Relative Reference In Excel Macro With Easy Steps Complemento absolute insights for endpoints identificar e responder às anomalias através de dashboards históricos personalizáveis obter insights sobre ativos e segurança em tempo real os profissionais de ti e segurança têm que gerenciar uma frota cada vez mais remota de dispositivos endpoint. 1993年に、教育分野のコンピューターを「追跡管理(track manage trace)」するプラットフォームのプロバイダーとして設立されたabsoluteは、真にインテリジェントな自動復活型セキュリティソリューションを提供する唯一のプロバイダーへと発展しました。. Absolute security cyber resilience survey and report reveals ciso challenges in the modern threat landscape. federal government leverage secure endpoint to enable a digital federal government, maintain security controls, protect sensitive public data and comply with a variety of federal data regulations. Leave nothing to chance with resilience — the absolute platform’s most comprehensive and secure product. allow compromised devices and critical apps to self heal if they're altered, disabled, or uninstalled. quickly find and lock devices that go dark. Absolute security is partnered with more than 28 of the world’s leading endpoint device manufacturers, embedded in the firmware of 600 million devices, trusted by thousands of global enterprise customers, and licensed across 16 million pc users. Absolute control gives you full visibility and command over every device in your endpoint population. keep sensitive data safe by creating boundaries with geofencing, and remotely delete data or freeze individual compromised devices — even if they're off network.
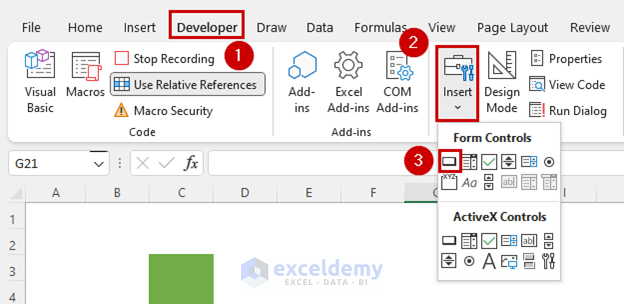
How To Use Relative Reference In Excel Macro With Easy Steps Absolute security cyber resilience survey and report reveals ciso challenges in the modern threat landscape. federal government leverage secure endpoint to enable a digital federal government, maintain security controls, protect sensitive public data and comply with a variety of federal data regulations. Leave nothing to chance with resilience — the absolute platform’s most comprehensive and secure product. allow compromised devices and critical apps to self heal if they're altered, disabled, or uninstalled. quickly find and lock devices that go dark. Absolute security is partnered with more than 28 of the world’s leading endpoint device manufacturers, embedded in the firmware of 600 million devices, trusted by thousands of global enterprise customers, and licensed across 16 million pc users. Absolute control gives you full visibility and command over every device in your endpoint population. keep sensitive data safe by creating boundaries with geofencing, and remotely delete data or freeze individual compromised devices — even if they're off network.