
Authentication Is There A Better Way Of Jwt Web Token Combined With You can use both asp identity or json web token. but as you have both spas and web api based on your scenario jwt would be the best optionl; so that you can use that everywhere, no matter in intranet or in web which would ensure more security. By decoupling the session lifetime from the jwt used to authenticate requests and instead tracking it elsewhere, you can have a hybrid approach to authentication that combines the best of both jwt authentication and session token authentication.
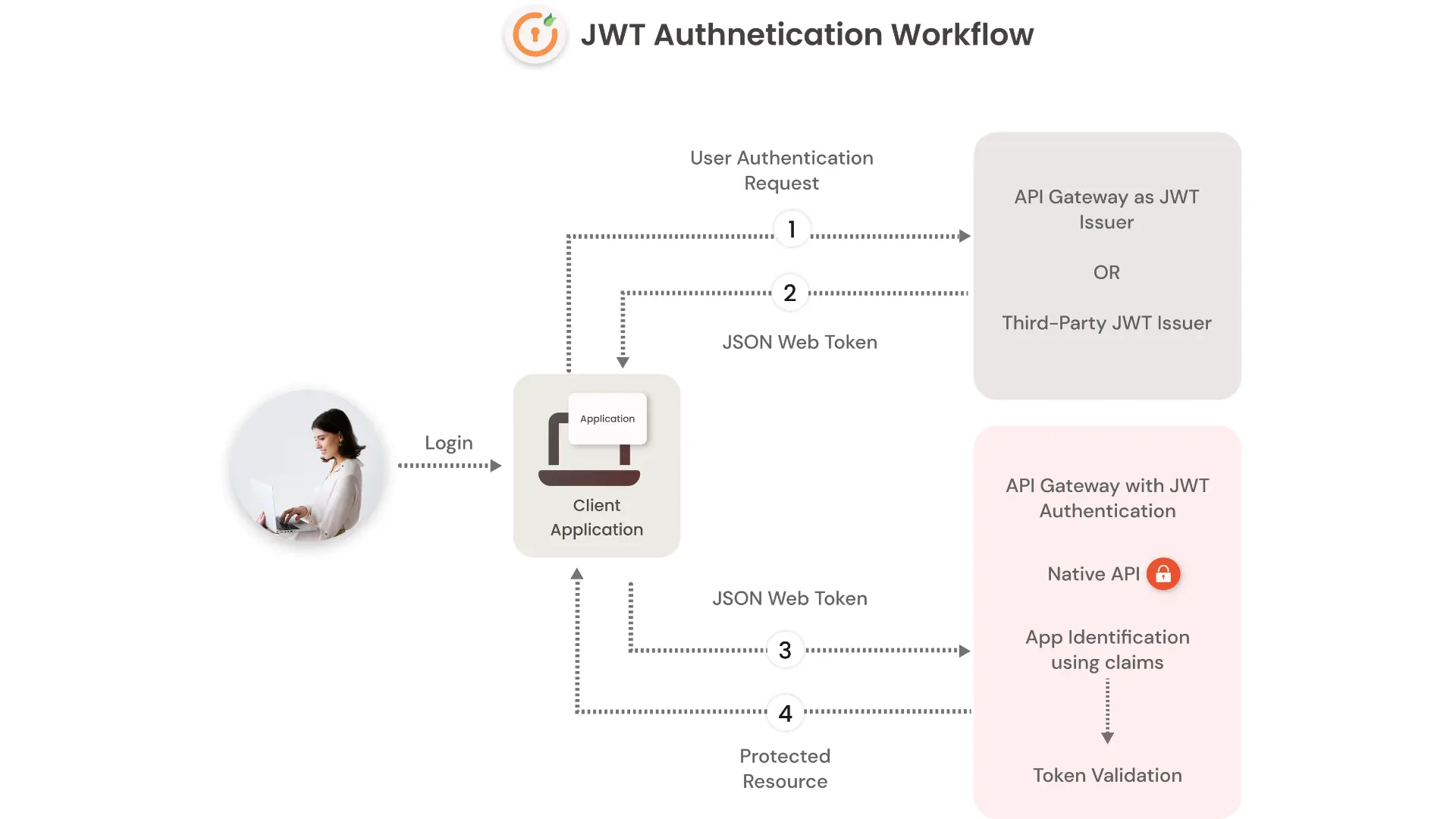
What Is Jwt Json Web Token How Does Jwt Authenticatio Vrogue Co To mitigate the downsides of jwts while leveraging their advantages, we propose a hybrid approach that combines jwts with traditional server sessions. initial authentication: upon successful. This article explores the fusion of jwt (json web token) authentication and session authentication, presenting a comprehensive approach that combines the strengths of both methods. Authentication is essential for secure user access, data protection, and resource management in modern applications. the two prevalent approaches for managing user sessions and verifying. Discover how json web tokens (jwt) revolutionize web authentication. this guide covers everything from basic concepts to advanced security measures, helping you implement secure, scalable authentication in modern applications.
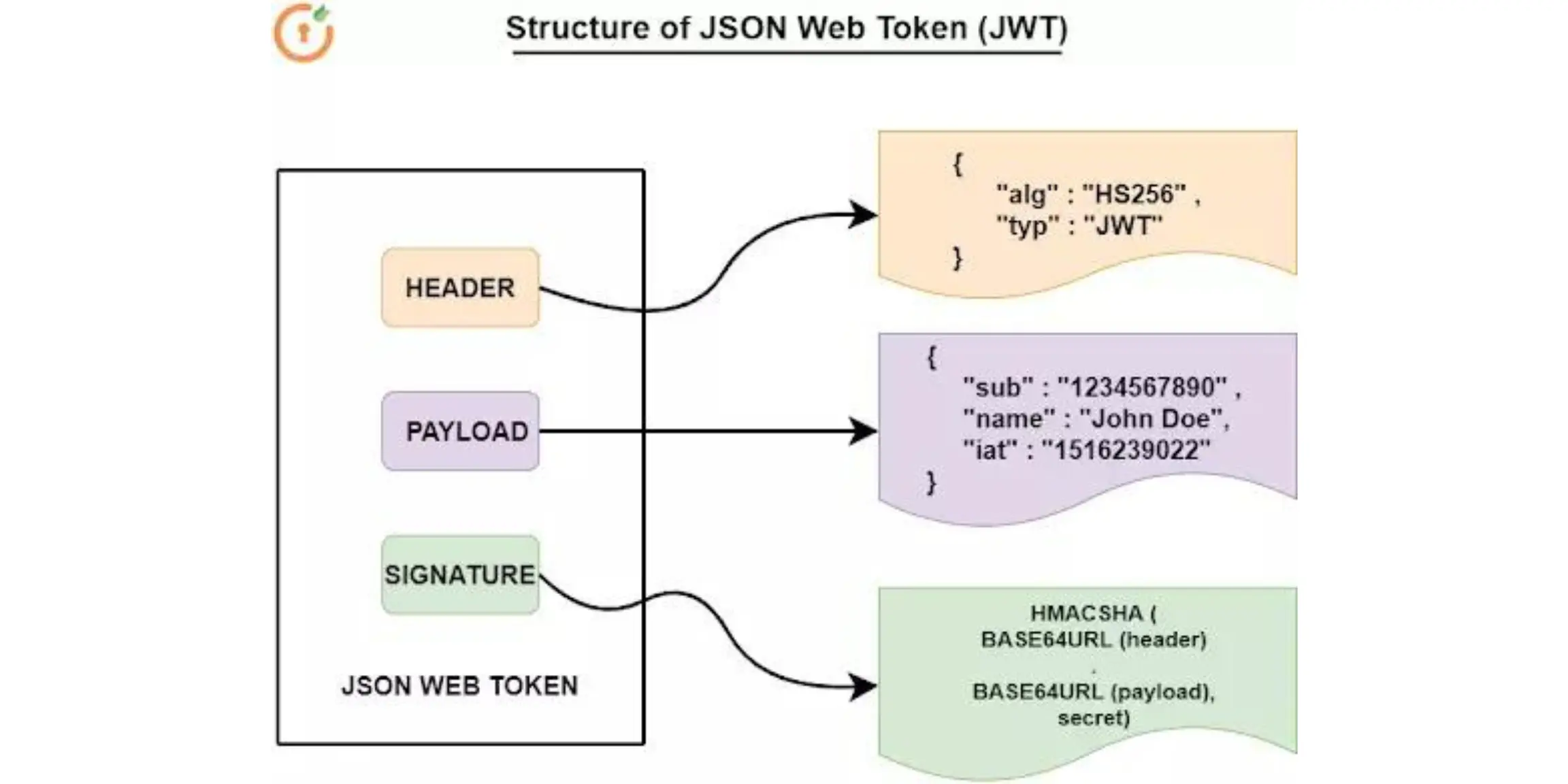
How Jwt Token Authentication Works Printable Templates Protal Authentication is essential for secure user access, data protection, and resource management in modern applications. the two prevalent approaches for managing user sessions and verifying. Discover how json web tokens (jwt) revolutionize web authentication. this guide covers everything from basic concepts to advanced security measures, helping you implement secure, scalable authentication in modern applications. Two popular methods are json web tokens (jwt) and session based authentication. with technical examples and security insights, let’s break down how jwts work, why they’re different from. Jwt provides an easy way to to do this. with knowledge of some of the security concerns to consider when using jwt, you can implement a more secure authentication as you see with third party authentication services. Token based authentication is widely used to secure applications, especially in modern web services. popular options include json web tokens (jwt), oauth, api keys, and platform agnostic security tokens (paseto). this guide explores how each token type works, its structure, pros and cons, and a recommended implementation approach. 1. Json web tokens have revolutionized how we handle authentication and authorization in modern applications. yet, i’ve seen countless developers fall into the same traps i did. this jwt best practices guide will save you from those headaches and help you implement jwts securely from day one.

Authentication With Next Js Jwt And Token Based Authentication Two popular methods are json web tokens (jwt) and session based authentication. with technical examples and security insights, let’s break down how jwts work, why they’re different from. Jwt provides an easy way to to do this. with knowledge of some of the security concerns to consider when using jwt, you can implement a more secure authentication as you see with third party authentication services. Token based authentication is widely used to secure applications, especially in modern web services. popular options include json web tokens (jwt), oauth, api keys, and platform agnostic security tokens (paseto). this guide explores how each token type works, its structure, pros and cons, and a recommended implementation approach. 1. Json web tokens have revolutionized how we handle authentication and authorization in modern applications. yet, i’ve seen countless developers fall into the same traps i did. this jwt best practices guide will save you from those headaches and help you implement jwts securely from day one.