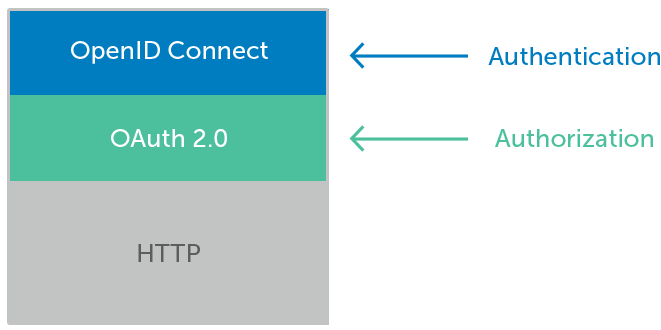
Openid Connect Okta Australia An openid connect (oidc) app integration provides an identity layer on top of the oauth 2.0 protocol to verify end users' identities and obtain profile information. Find information about the oauth 2.0 and openid connect endpoints that okta exposes on its authorization servers.
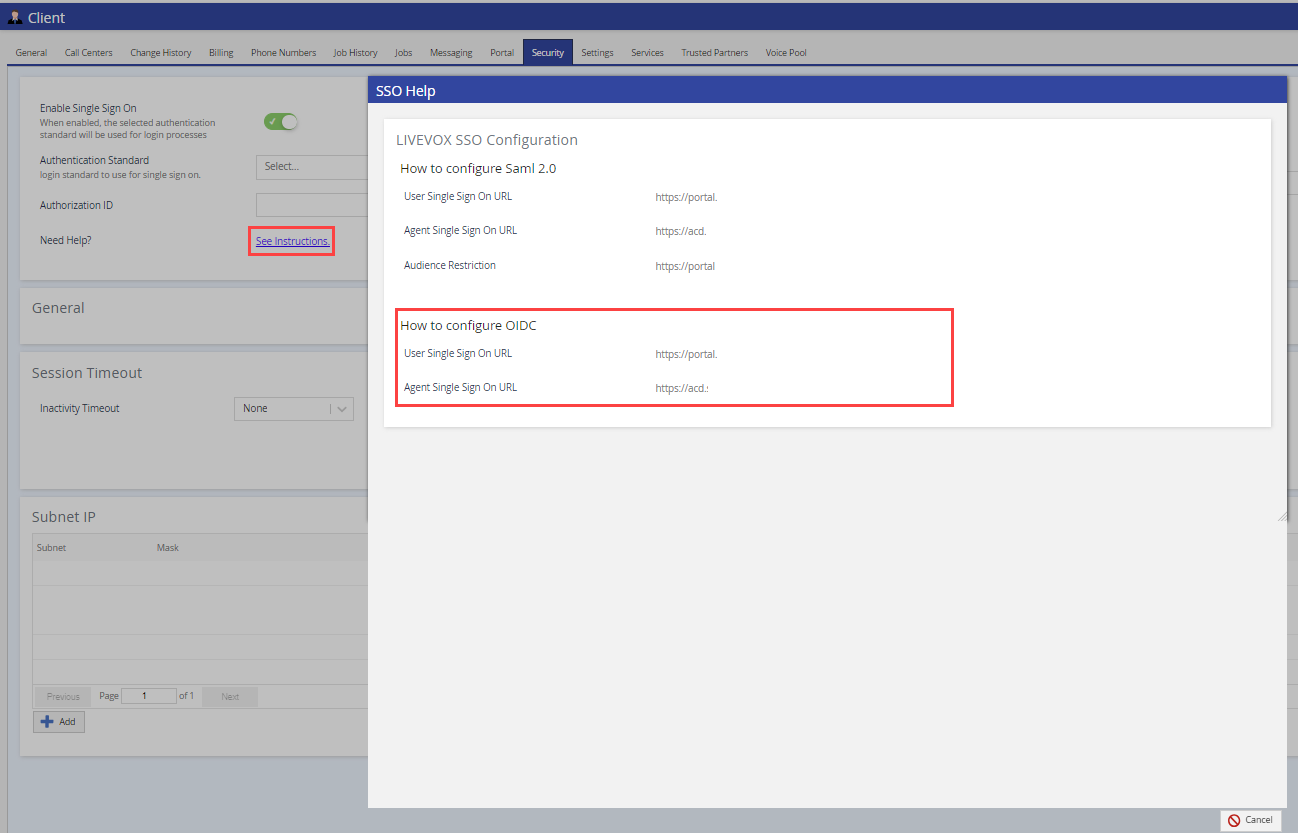
Configuring Openid Connect Oidc In Okta To enable secure access to authenticate with oidc, you must set up the integration of an oidc identity provider (idp) in secure access. on the organization's instance of okta, configure an okta id oidc app. then to complete the integration, add the oidc idp metadata in secure access. Where oauth 2.0 provides authorization via an access token containing scopes, openid connect provides authentication by introducing a new token, the id token which contains a new set of scopes and claims specifically for identity. In this article, we will cover the step by step process of setting up openid connect (oidc) single sign on using okta. you can learn more about how to set up oidc sso in businessmap here. 1. head to your okta administrator dashboard, select applications, and click on the applications tab. 2. select “ create app integration.” 3. To set up an sso connection that lets users sign in to your blackbaud solutions using okta as your idp, use the oidc protocol to enable third party applications to verify end users.
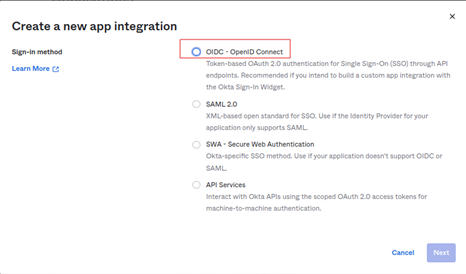
Configuring Openid Connect Oidc In Okta In this article, we will cover the step by step process of setting up openid connect (oidc) single sign on using okta. you can learn more about how to set up oidc sso in businessmap here. 1. head to your okta administrator dashboard, select applications, and click on the applications tab. 2. select “ create app integration.” 3. To set up an sso connection that lets users sign in to your blackbaud solutions using okta as your idp, use the oidc protocol to enable third party applications to verify end users. This article describes how to make an openid connect (oidc) app visible in the okta dashboard and the different login flows available. for an openid connect oauth application to appear as an app in the okta dashboard, the application's general settings will need to be configured as follows (see below for additional options):. Okta supports two sso standards for your integration: openid connect (oidc) (preferred) security assertion markup language (saml) okta recommends using oidc for new sso integrations. note: not all okta sso features are supported in the oin. see oin limitations. deployment models after you've decided on a protocol, select a deployment model. Openid connect (oidc) is an identity and authentication layer built on top of the oauth2 authorization framework. this guide explains how to set up oidc with okta as identity platform for dhis 2. In this post, i will share how to build oidc sso using okta, keycloak and google as op (openid provider). the tutorials attached include the following contents. 1. okta (cloud) 1. set up okta. 1 1. create an application. 1 2. add person. 2. configure pega platform. 3. mapping claims. 3 1. jwt (id token) 3 2. userinfo. 2. keycloak (on premise) 1.
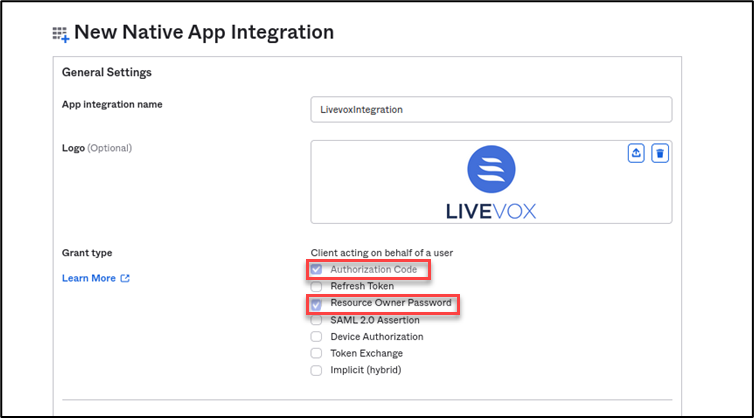
Configuring Openid Connect Oidc In Okta This article describes how to make an openid connect (oidc) app visible in the okta dashboard and the different login flows available. for an openid connect oauth application to appear as an app in the okta dashboard, the application's general settings will need to be configured as follows (see below for additional options):. Okta supports two sso standards for your integration: openid connect (oidc) (preferred) security assertion markup language (saml) okta recommends using oidc for new sso integrations. note: not all okta sso features are supported in the oin. see oin limitations. deployment models after you've decided on a protocol, select a deployment model. Openid connect (oidc) is an identity and authentication layer built on top of the oauth2 authorization framework. this guide explains how to set up oidc with okta as identity platform for dhis 2. In this post, i will share how to build oidc sso using okta, keycloak and google as op (openid provider). the tutorials attached include the following contents. 1. okta (cloud) 1. set up okta. 1 1. create an application. 1 2. add person. 2. configure pega platform. 3. mapping claims. 3 1. jwt (id token) 3 2. userinfo. 2. keycloak (on premise) 1.