
Copilot For Microsoft 365 Data Security Access Control 101 Best When adopting microsoft copilot for microsoft 365, it’s crucial to address the risks associated with poor access control. copilot, with its ai powered capabilities, promises to enhance productivity within m365 applications like word, powerpoint, teams, and outlook. Learn how microsoft 365 copilot uses data and how it stores and protects that data.

Copilot For Microsoft 365 Data Security Access Control 101 Best First things first – copilot doesn’t grant access to any more than what your users can currently access today. this means that if anna from accounts can’t access hr data today, copilot won’t grant her access to that data. Learn how to protect your data and ensure access control best practices and tips for copilot for microsoft 365. The integration of generative ai into enterprise ecosystems has significant implications for data security, governance, and compliance. in this blog, we explore microsoft copilot’s architecture, use cases, and associated risks, and outline best practices for it professionals and security leaders to ensure a secure and responsible rollout. At microsoft ignite 2024, erica toelle and jeremy chapman introduced a fresh approach to this challenge, focused on just enough access (jea) with microsoft 365 copilot. here’s a practical look at how these new tools help maintain control and security without slowing down innovation.
Introducing Microsoft Security Copilot Empowering Defenders At The The integration of generative ai into enterprise ecosystems has significant implications for data security, governance, and compliance. in this blog, we explore microsoft copilot’s architecture, use cases, and associated risks, and outline best practices for it professionals and security leaders to ensure a secure and responsible rollout. At microsoft ignite 2024, erica toelle and jeremy chapman introduced a fresh approach to this challenge, focused on just enough access (jea) with microsoft 365 copilot. here’s a practical look at how these new tools help maintain control and security without slowing down innovation. Follow these three best practices to ensure you’re fully equipped to reap the benefits of copilot for microsoft 365 in a secure and sustainable way. elevate your data management practices and implement and enforce governance controls to fuel sustainable ai success. Copilot uses zero trust architecture, tenant isolation, and encryption to safeguard data. it also features defenses against prompt injection using machine learning and content filters. but organizations still bear responsibility for misconfigured access and risks like social engineering attacks. When adopting microsoft copilot for microsoft 365, it’s crucial to address the risks associated with poor access control. copilot, with its ai powered capabilities, promises to enhance productivity within m365 applications like word, powerpoint, teams, and outlook. Learn how to set up guardrails in microsoft 365 copilot to prevent sensitive data exposure before loose permissions lead to costly security breaches.
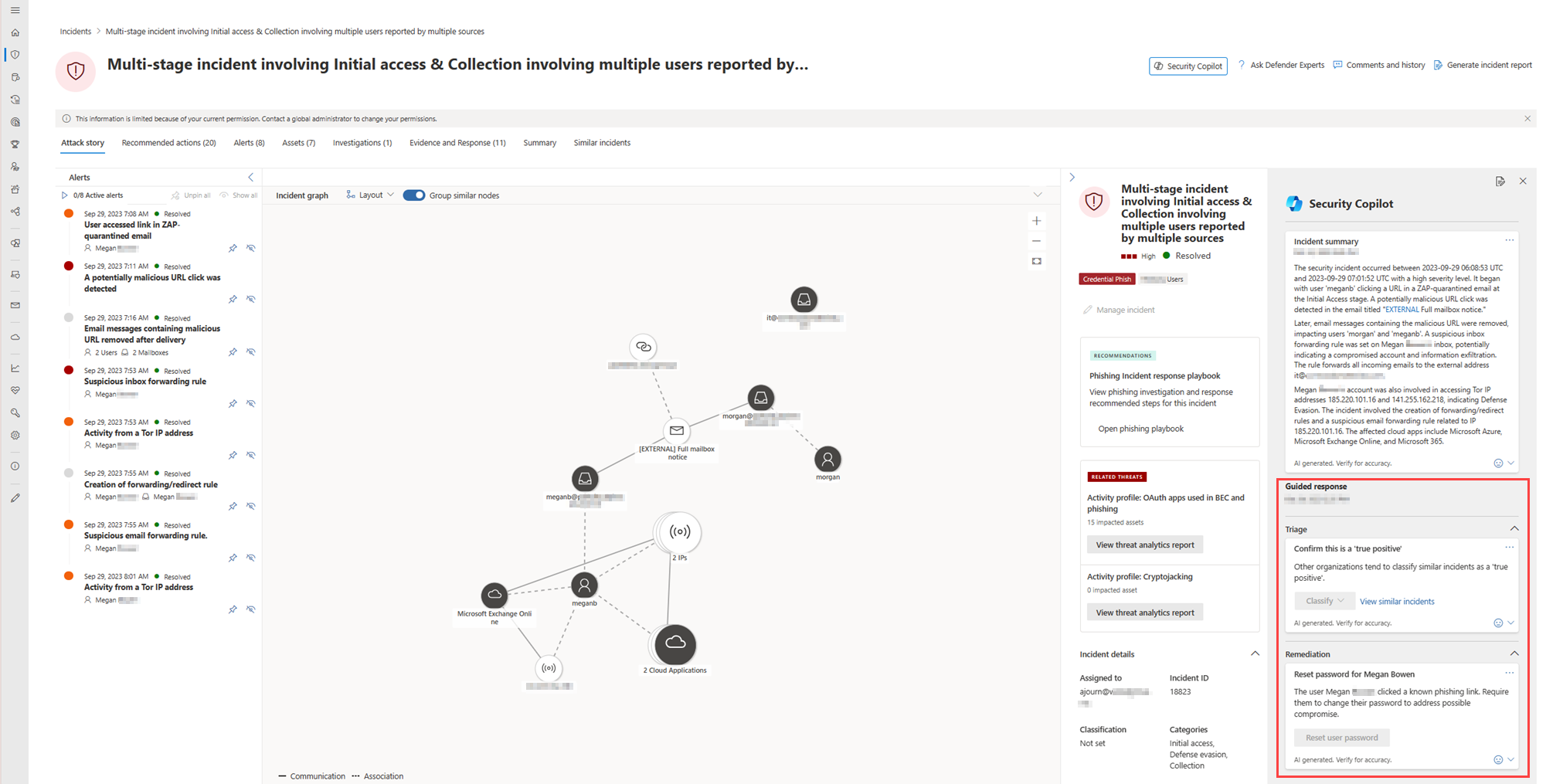
Microsoft Security Copilot In Microsoft Defender Xdr Microsoft Learn Follow these three best practices to ensure you’re fully equipped to reap the benefits of copilot for microsoft 365 in a secure and sustainable way. elevate your data management practices and implement and enforce governance controls to fuel sustainable ai success. Copilot uses zero trust architecture, tenant isolation, and encryption to safeguard data. it also features defenses against prompt injection using machine learning and content filters. but organizations still bear responsibility for misconfigured access and risks like social engineering attacks. When adopting microsoft copilot for microsoft 365, it’s crucial to address the risks associated with poor access control. copilot, with its ai powered capabilities, promises to enhance productivity within m365 applications like word, powerpoint, teams, and outlook. Learn how to set up guardrails in microsoft 365 copilot to prevent sensitive data exposure before loose permissions lead to costly security breaches.