
Cross Site Scripting Xss Exploits Total Uptime Throughout the world, images of the cross adorn the walls and steeples of churches. for some christians, the cross is part of their daily attire worn around their necks. sometimes the cross even adorns the body of a christian in permanent ink. in egypt, among other countries, for example, christians wear a tattoo of the cross on their wrists. and for some christians, each year during the. Cross attention mask: similarly to the previous two, it should mask input that the model "shouldn't have access to". so for a translation scenario, it would typically have access to the entire input and the output generated so far. so, it should be a combination of the causal and padding mask. 👏 well written question, by the way.

Cross Site Scripting Xss Payload Generator Nettitude Labs The history of crucifixion was brought to life when the heel bones of a young man were found in a jerusalem tomb, pierced by an iron nail. In addition to its symbolism for the holy spirit, the dove was a popular christian symbol before the cross rose to prominence in the fourth century. the dove continued to be used for various church implements throughout the byzantine and medieval period, including the form of oil lamps and this 13th century altar piece for holding the eucharistic bread. walters art museum, baltimore. Currently, we use cross validation to model the optimal smoothness of our spline models using penalized likelihoods. moreover, we use bootstrap around the entire procedure to understand the sensitivity in parameter estimates. nb: for each bootstrap iteration, we use cross validation to find the optimal smoothness for each bootstrap resample. The true location of golgotha, where jesus was crucified, remains debated, but evidence may support the church of the holy sepulchre.

Understanding Cross Site Scripting Xss Attacks Currently, we use cross validation to model the optimal smoothness of our spline models using penalized likelihoods. moreover, we use bootstrap around the entire procedure to understand the sensitivity in parameter estimates. nb: for each bootstrap iteration, we use cross validation to find the optimal smoothness for each bootstrap resample. The true location of golgotha, where jesus was crucified, remains debated, but evidence may support the church of the holy sepulchre. Gospel accounts of jesus’s execution do not specify how exactly jesus was secured to the cross. yet in christian tradition, jesus had his palms and feet pierced with nails. even though roman execution methods did include crucifixion with nails, some scholars believe this method only developed after jesus’s lifetime. Roman crucifixion methods as analyzed from the remains found in jerusalem of a young man crucified in the first century a.d. Several papers books i have read say that cross entropy is used when looking for the best split in a classification tree, e.g. the elements of statistical learning (hastie, tibshirani, friedman) wi. I understand cross validate and how it works, but now i am confused about what cross val score actually does. can anyone give me some example?.
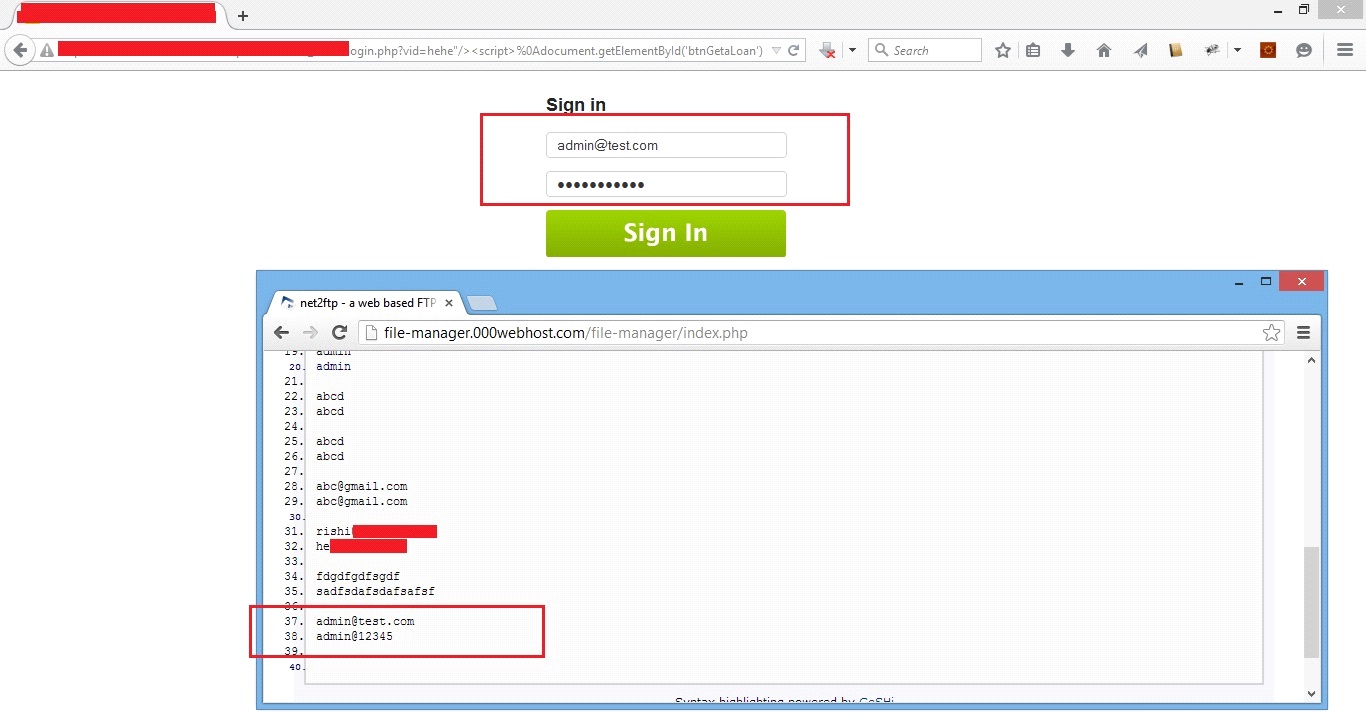
Cross Site Scripting Xss Exploitation Zensar Gospel accounts of jesus’s execution do not specify how exactly jesus was secured to the cross. yet in christian tradition, jesus had his palms and feet pierced with nails. even though roman execution methods did include crucifixion with nails, some scholars believe this method only developed after jesus’s lifetime. Roman crucifixion methods as analyzed from the remains found in jerusalem of a young man crucified in the first century a.d. Several papers books i have read say that cross entropy is used when looking for the best split in a classification tree, e.g. the elements of statistical learning (hastie, tibshirani, friedman) wi. I understand cross validate and how it works, but now i am confused about what cross val score actually does. can anyone give me some example?.
What Is Cross Site Scripting Xss Types Risks Prevention Several papers books i have read say that cross entropy is used when looking for the best split in a classification tree, e.g. the elements of statistical learning (hastie, tibshirani, friedman) wi. I understand cross validate and how it works, but now i am confused about what cross val score actually does. can anyone give me some example?.