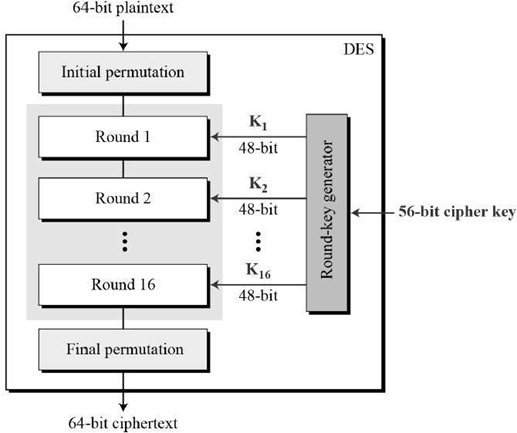
Data Encryption Standard Des In Cryptography • AES (Advanced Encryption Standard): AES is a symmetric encryption algorithm widely used in government and industry It offers key lengths of 128, 192 and 256 bits, providing strong security The National Institute of Standards and Technology (NIST) is proposing that the Data Encryption Standard (DES), a popular encryption algorithm, lose its certification for use in software products

Des Data Encryption Standard Data Encryption Standard In Cryptography On March 17, 1975, the National Bureau of Standards (NBS) published its proposed Data Encryption Standard (DES) in the Federal Register The algorithm used a 56-bit encryption key, which (it was FEAL (Fast Data Encipherment Algorithm) DES (Data Encryption Standard) Triple DES; LOKI; Symmetric encryption is also divided into two groups: block andstream ciphers Block ciphers work on blocks of History has shown that it is always necessary for security to evolve to meet the demands of new technology Moore's Law may work wonders for computing horsepower, but it creates nightmares for LEUVEN, Belgium -- Can you spare 149 trillion years? That's how long it would take the most sophisticated hacker to crack Rijndael, the encryption formula created by Belgian engineers Vincent
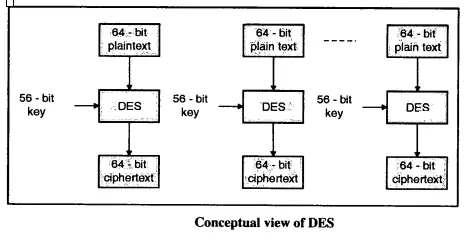
What Is Data Encryption Standard Des In Cryptography Guide To Des History has shown that it is always necessary for security to evolve to meet the demands of new technology Moore's Law may work wonders for computing horsepower, but it creates nightmares for LEUVEN, Belgium -- Can you spare 149 trillion years? That's how long it would take the most sophisticated hacker to crack Rijndael, the encryption formula created by Belgian engineers Vincent Ultra-Compact Data Encryption Standard (DES/3DES) Core The DES1 ASIC/FPGA core is an implementation of the DES and triple DES encryption and decryption in compliance with the NIST Data Encryption The Commerce Department approves the Advanced Encryption Standard, a new, stronger data-encryption standard intended to replace an aging standard first adopted in 1977 According to Jörg Schwenk who teaches of Electrical Engineering and Information Technology at RUB, all data encryption algorithms recommended in the XML Encryption standard are affected by this In asymmetric encryption cryptography, one public and one private key are used to encrypt and decrypt data The public key can be disseminated openly, while the private key is known only to the owner

What Is Data Encryption Standard Des In Cryptography Guide To Des Ultra-Compact Data Encryption Standard (DES/3DES) Core The DES1 ASIC/FPGA core is an implementation of the DES and triple DES encryption and decryption in compliance with the NIST Data Encryption The Commerce Department approves the Advanced Encryption Standard, a new, stronger data-encryption standard intended to replace an aging standard first adopted in 1977 According to Jörg Schwenk who teaches of Electrical Engineering and Information Technology at RUB, all data encryption algorithms recommended in the XML Encryption standard are affected by this In asymmetric encryption cryptography, one public and one private key are used to encrypt and decrypt data The public key can be disseminated openly, while the private key is known only to the owner End-to-end encryption: Some healthcare organizations are adopting end-to-end encryption (E2EE) for transmitting sensitive data, which ensures that only the intended recipients can decrypt and read
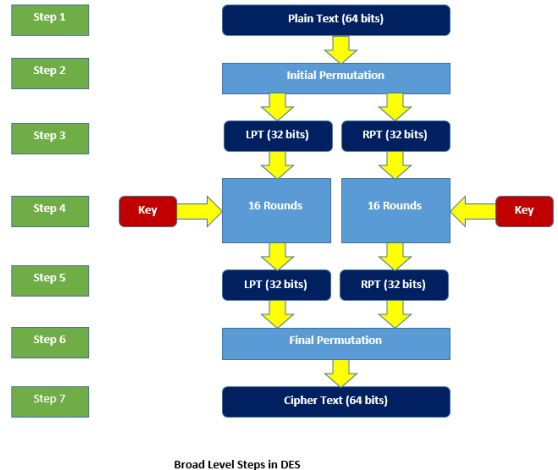
Cryptography Data Encryption Standard Des According to Jörg Schwenk who teaches of Electrical Engineering and Information Technology at RUB, all data encryption algorithms recommended in the XML Encryption standard are affected by this In asymmetric encryption cryptography, one public and one private key are used to encrypt and decrypt data The public key can be disseminated openly, while the private key is known only to the owner End-to-end encryption: Some healthcare organizations are adopting end-to-end encryption (E2EE) for transmitting sensitive data, which ensures that only the intended recipients can decrypt and read

Des Data Encryption Standard Bench Partner End-to-end encryption: Some healthcare organizations are adopting end-to-end encryption (E2EE) for transmitting sensitive data, which ensures that only the intended recipients can decrypt and read