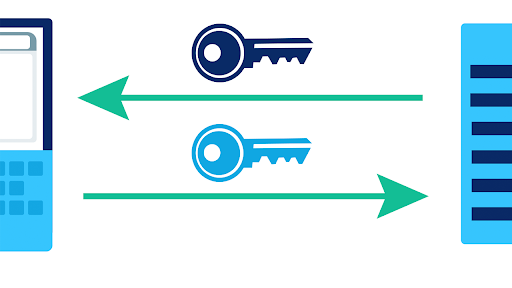
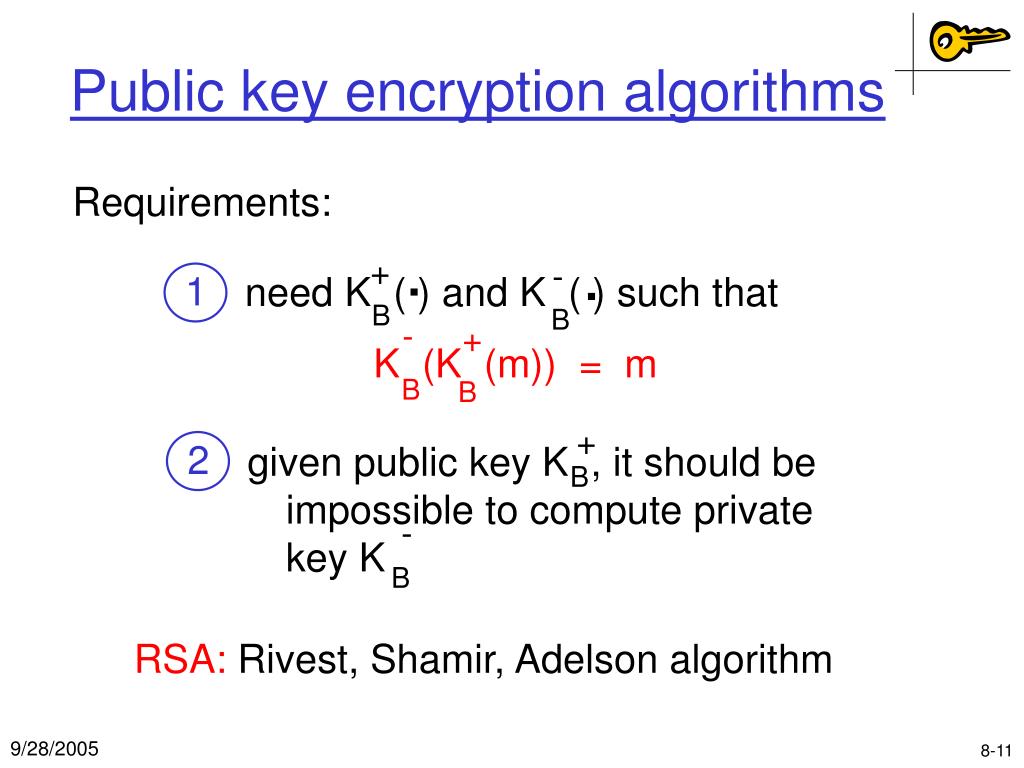
Welcome to the fascinating world of technology, where innovation knows no bounds. Join us on an exhilarating journey as we explore cutting-edge advancements, share insightful analyses, and unravel the mysteries of the digital age in our Encryption And Public Keys Internet 101 Computer Science Khan Academy section.
Conclusion
Having examined the subject matter thoroughly, it can be concluded that this particular post supplies worthwhile data in connection with Encryption And Public Keys Internet 101 Computer Science Khan Academy. In the complete article, the commentator depicts noteworthy proficiency in the domain.
Markedly, the part about contributing variables stands out as exceptionally insightful. The text comprehensively covers how these components connect to form a complete picture of Encryption And Public Keys Internet 101 Computer Science Khan Academy.
Besides, the document shines in disentangling complex concepts in an simple manner. This accessibility makes the subject matter useful across different knowledge levels.
The author further augments the presentation by including fitting illustrations and real-world applications that situate the theoretical constructs.
A further characteristic that makes this post stand out is the thorough investigation of different viewpoints related to Encryption And Public Keys Internet 101 Computer Science Khan Academy. By exploring these alternate approaches, the piece offers a well-rounded picture of the subject matter.
The exhaustiveness with which the creator treats the topic is extremely laudable and establishes a benchmark for analogous content in this discipline.
In conclusion, this article not only informs the consumer about Encryption And Public Keys Internet 101 Computer Science Khan Academy, but also encourages further exploration into this interesting field. If you happen to be uninitiated or a veteran, you will discover beneficial knowledge in this thorough post.
Thank you sincerely for taking the time to this content. Should you require additional details, please do not hesitate to reach out using the feedback area. I am keen on your questions.
For further exploration, here is some similar write-ups that might be valuable and supplementary to this material. Wishing you enjoyable reading!