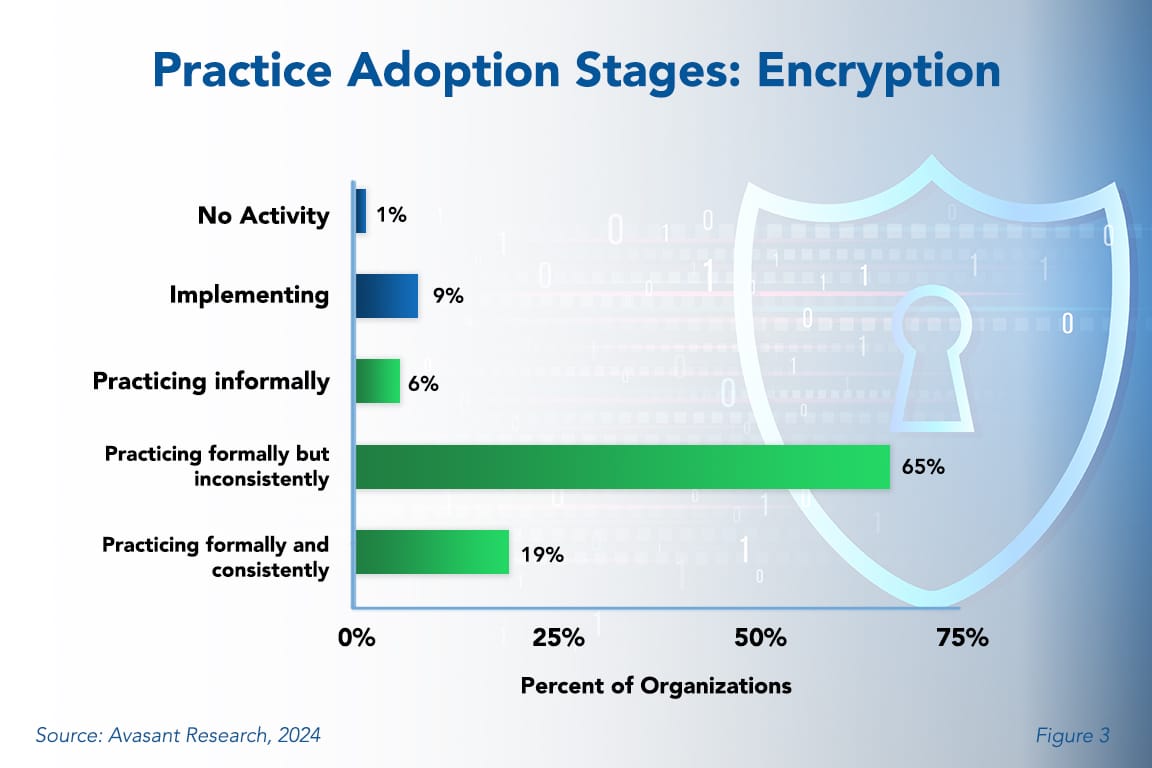
Encryption Best Practices 2024 Avasant In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. this process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Encryption is an essential online privacy tool used to safeguard sensitive, confidential, or personal information across the internet. encryption scrambles plain text into a type of secret code that hackers, cybercriminals, and other online snoops can't read—even if they intercept it before it reaches its intended recipients.
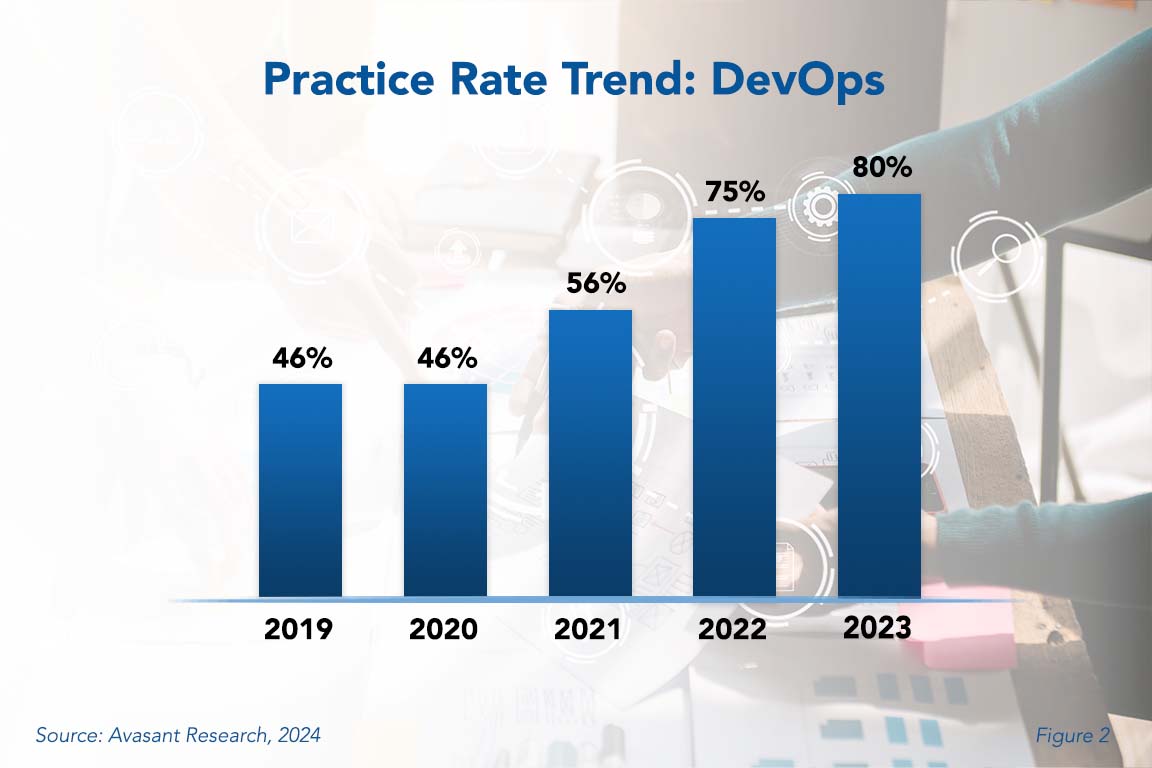
Devops Best Practices 2024 Avasant Learn how encryption works and how to use it to protect data from being accessed by unauthorized users. explore benefits, types, implementation and more. Encryption is a form of data security in which information is converted to ciphertext. only authorized people who have the key can decipher the code and access the original plaintext information. in even simpler terms, encryption is a way to render data unreadable to an unauthorized party. Data encryption is the process of converting readable information (plaintext) into an unreadable format (ciphertext) to protect it from unauthorized access. it is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded using a unique decryption key produced at the time of the encryption or. Encryption is the process of transforming readable plain text into unreadable ciphertext to mask sensitive information from unauthorized users. organizations regularly use encryption in data security to protect sensitive data from unauthorized access and data breaches.

Agile Development Best Practices 2024 Avasant Data encryption is the process of converting readable information (plaintext) into an unreadable format (ciphertext) to protect it from unauthorized access. it is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded using a unique decryption key produced at the time of the encryption or. Encryption is the process of transforming readable plain text into unreadable ciphertext to mask sensitive information from unauthorized users. organizations regularly use encryption in data security to protect sensitive data from unauthorized access and data breaches. Encryption is the process of converting or scrambling data and information into an unreadable, encoded version that can only be read with authorized access. encryption is a widely used security tool that can prevent the interception of sensitive data, either while stored in files or while in transit across networks. Encryption is a way of scrambling data so that only authorized parties can understand the information. in technical terms, it is the process of converting human readable plaintext to incomprehensible text, also known as ciphertext. Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only be unlocked with a unique digital key. Encryption protects data by converting it into an unreadable format that can only be decoded with the right key. it ensures that sensitive data remains secure, whether stored on a device or.
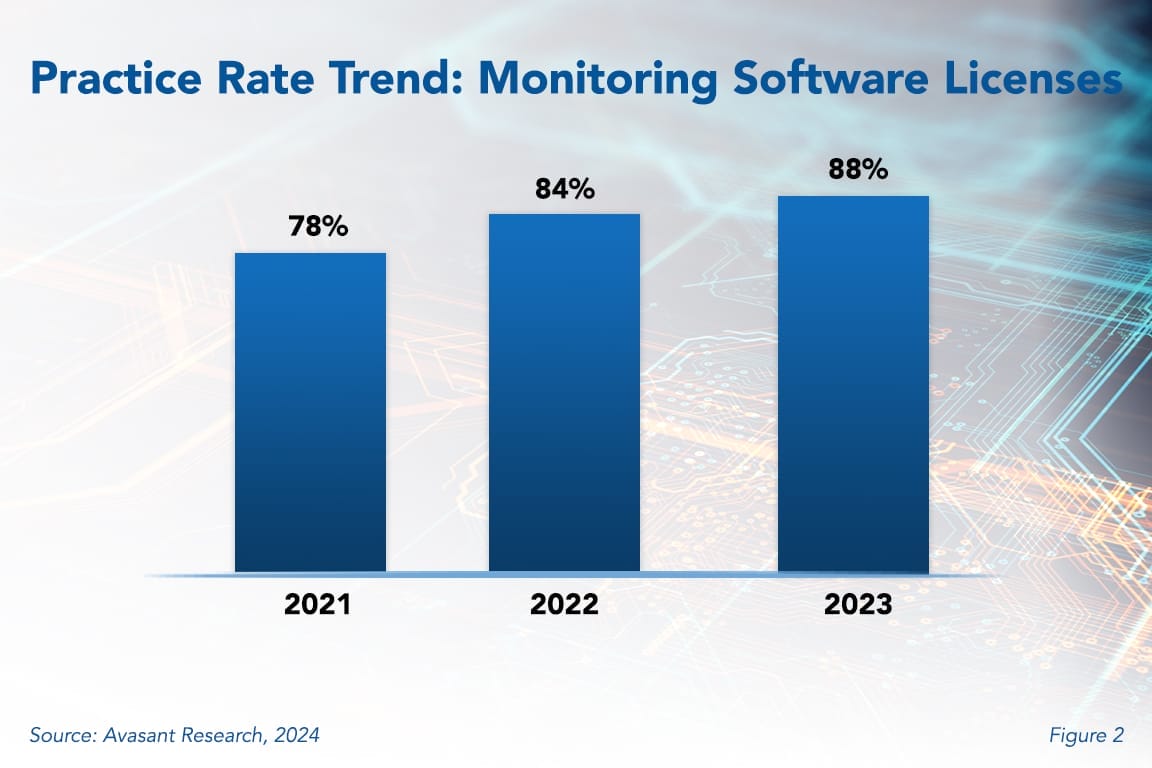
Monitoring Software Licenses Best Practices 2024 Avasant Encryption is the process of converting or scrambling data and information into an unreadable, encoded version that can only be read with authorized access. encryption is a widely used security tool that can prevent the interception of sensitive data, either while stored in files or while in transit across networks. Encryption is a way of scrambling data so that only authorized parties can understand the information. in technical terms, it is the process of converting human readable plaintext to incomprehensible text, also known as ciphertext. Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only be unlocked with a unique digital key. Encryption protects data by converting it into an unreadable format that can only be decoded with the right key. it ensures that sensitive data remains secure, whether stored on a device or.
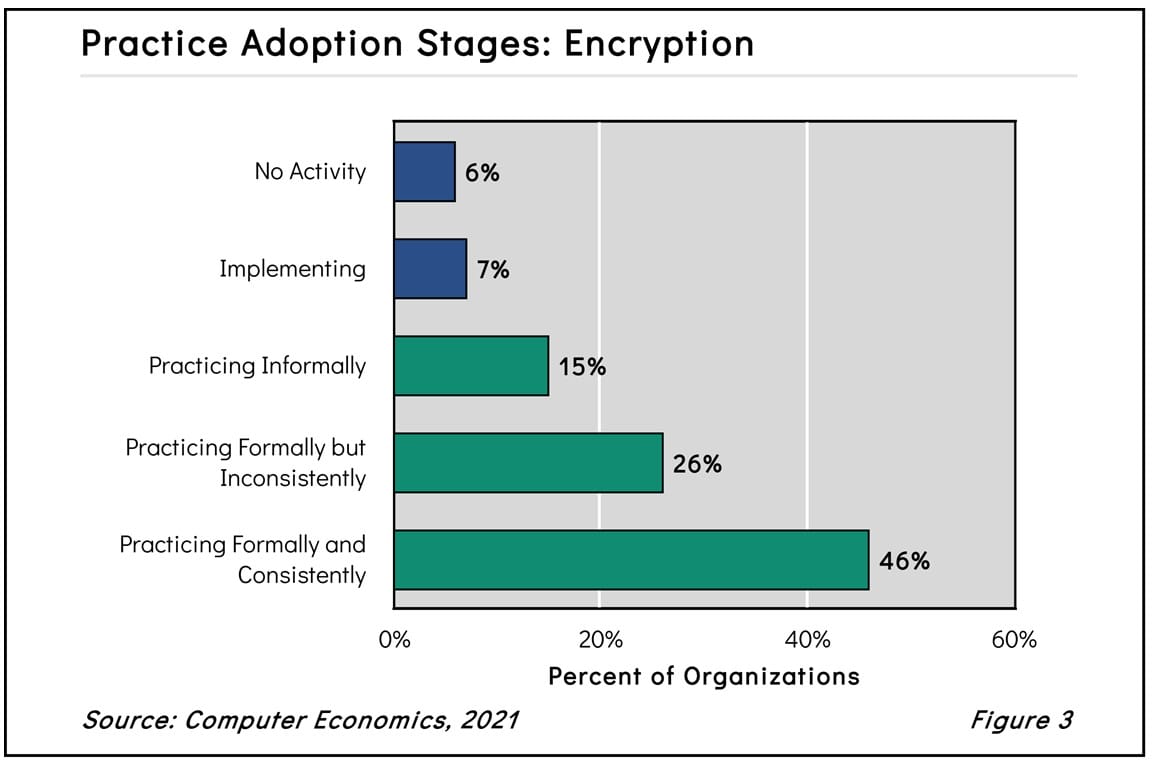
Encryption Adoption And Best Practices 2021 Avasant Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only be unlocked with a unique digital key. Encryption protects data by converting it into an unreadable format that can only be decoded with the right key. it ensures that sensitive data remains secure, whether stored on a device or.

Avasant On Linkedin Itil Best Practices 2024