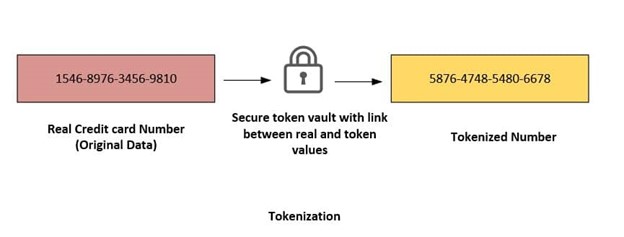
Tokenization Vs Encryption Similarities And Differences Tokenization and encryption are the most popular techniques for robust protection against data breaches. both methods aim to secure data but operate differently, each with strengths and weaknesses. While tokenization and encryption are both crucial when managing and protecting sensitive data, the two approaches have certain advantages and disadvantages and must be used for different purposes.

Tokenization Vs Encryption Similarities And Differences Encryption uses shared keys to hide the content of communications as they are transmitted across networks; by contrast, tokenization replaces sensitive data with randomly generated strings. While both tokenization and encryption enhance data security, their approaches differ. tokenization focuses on replacing data with unrelated tokens, minimizing the exposure of sensitive information, and simplifying compliance with data protection regulations. Tokenization and encryption are not synonymous, nor can they be used interchangeably. there are strengths and weaknesses to each technology, and based on those, one or the other should be used to secure data depending on the situation. Encryption provides secure access to data while allowing reversible transformation. tokenization replaces sensitive data with. unique tokens for storage and processing purposes, retaining referential integrity. masking. on the other hand, modifies data to ensure privacy while preserving its structure. however, all three tec.
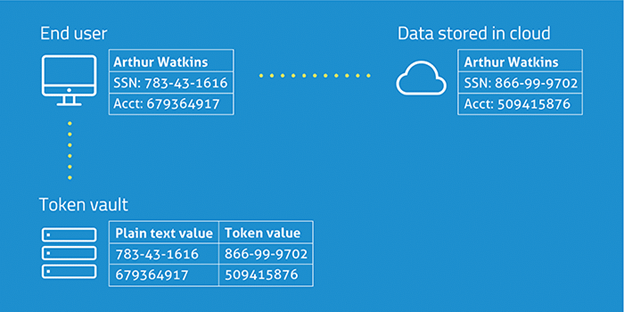
Tokenization Vs Encryption Similarities And Differences Tokenization and encryption are not synonymous, nor can they be used interchangeably. there are strengths and weaknesses to each technology, and based on those, one or the other should be used to secure data depending on the situation. Encryption provides secure access to data while allowing reversible transformation. tokenization replaces sensitive data with. unique tokens for storage and processing purposes, retaining referential integrity. masking. on the other hand, modifies data to ensure privacy while preserving its structure. however, all three tec. Encryption and tokenization are both data security techniques but work differently. encryption scrambles data to make it unreadable without a key. tokenization replaces data with random tokens or references. encryption provides strong protection but requires managing keys. Data retrieval: tokenization retrieves data by matching tokens, while encryption requires the correct encryption key for decryption. applicability: encryption is suitable for securing various types of data, whereas tokenization is primarily used for smaller data sets, such as credit card numbers. Tokenization and encryption are two sides of the same coin in data security. while they share similarities, the key difference lies in how they protect sensitive data and when each is best applied. Encryption and tokenization are both powerful data security methods that help organizations protect sensitive information and comply with regulatory requirements.