
Exploits Explained 5 Unusual Authentication Bypass Techniques Synack The meaning of exploit is deed, act; especially : a notable, memorable, or heroic act. how to use exploit in a sentence. synonym discussion of exploit. Exploit definition: a striking or notable deed; feat; spirited or heroic act see examples of exploit used in a sentence.
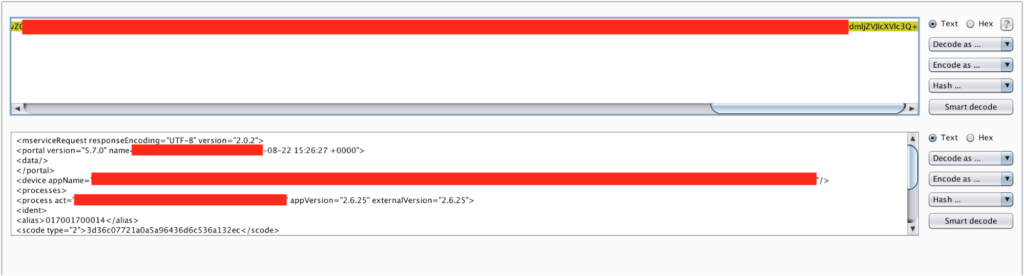
Exploits Explained 5 Unusual Authentication Bypass Techniques Synack Exploits target vulnerabilities, which are essentially flaws or weaknesses in a system's defenses. common targets for exploits include operating systems, web browsers, and various applications, where hidden vulnerabilities can compromise the integrity and security of computer systems. exploits can cause unintended or unanticipated behavior in systems, potentially leading to severe security. Exploit definition: 1. to use something in a way that helps you: 2. to use someone or something unfairly for your own…. learn more. Discover what an exploit is in cybersecurity, how it works, types, and effective strategies to prevent and mitigate exploit attacks. An exploit is a piece of software or code created to take advantage of a vulnerability. it is not malicious in essence, it is rather a method to prey on a software or hardware security flaw.

Exploits Explained 5 Unusual Authentication Bypass Techniques Synack Discover what an exploit is in cybersecurity, how it works, types, and effective strategies to prevent and mitigate exploit attacks. An exploit is a piece of software or code created to take advantage of a vulnerability. it is not malicious in essence, it is rather a method to prey on a software or hardware security flaw. Wireless exploits: these exploits target vulnerabilities in wireless networks, such as wi fi or bluetooth. cryptographic exploits: these exploits focus on weaknesses or vulnerabilities in cryptographic algorithms, protocols, or implementations. different types of exploits exploits are commonly classified into two types: known or unknown exploits. Learn what a cybersecurity exploit is, how attackers use them to breach systems, and the key strategies to detect and mitigate vulnerability exploitation. Exploit is a program, piece of code, or set of instructions used to take advantage of a weakness in a computer system, software, or hardware. Vulnerability intelligence that predicts avenues of attack with speed and accuracy.
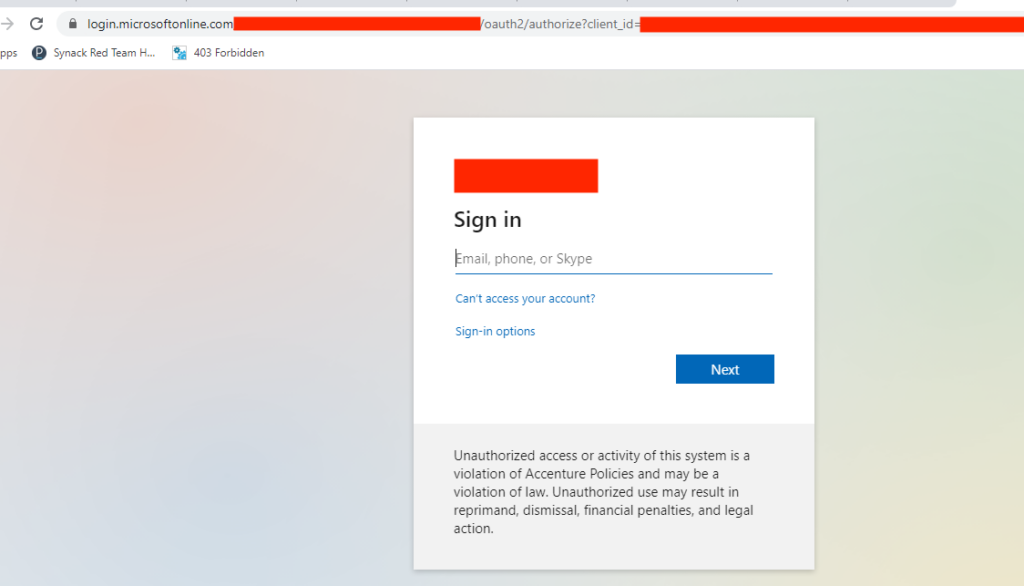
Exploits Explained 5 Unusual Authentication Bypass Techniques Synack Wireless exploits: these exploits target vulnerabilities in wireless networks, such as wi fi or bluetooth. cryptographic exploits: these exploits focus on weaknesses or vulnerabilities in cryptographic algorithms, protocols, or implementations. different types of exploits exploits are commonly classified into two types: known or unknown exploits. Learn what a cybersecurity exploit is, how attackers use them to breach systems, and the key strategies to detect and mitigate vulnerability exploitation. Exploit is a program, piece of code, or set of instructions used to take advantage of a weakness in a computer system, software, or hardware. Vulnerability intelligence that predicts avenues of attack with speed and accuracy.
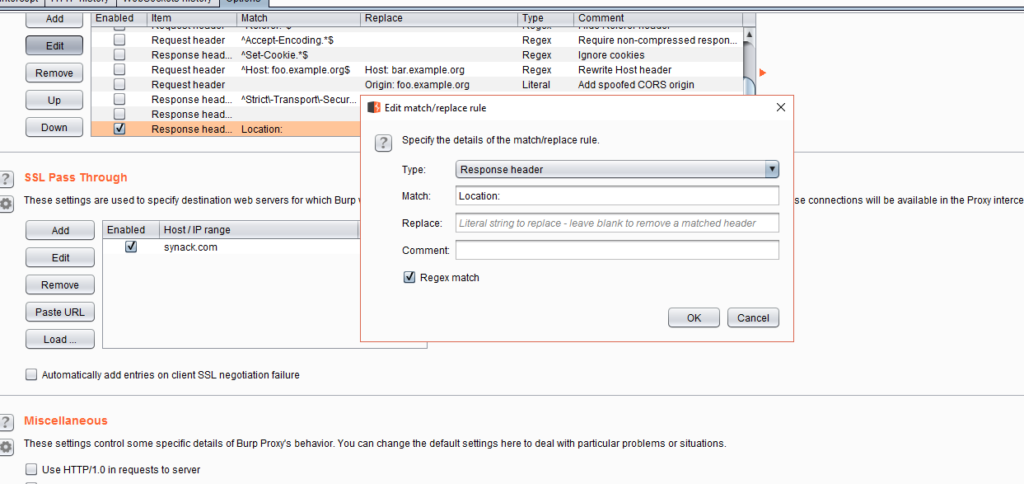
Exploits Explained 5 Unusual Authentication Bypass Techniques Synack Exploit is a program, piece of code, or set of instructions used to take advantage of a weakness in a computer system, software, or hardware. Vulnerability intelligence that predicts avenues of attack with speed and accuracy.