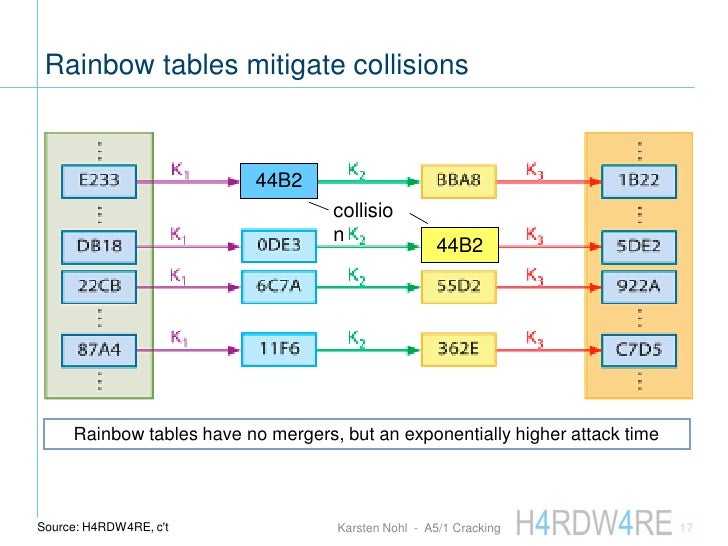
Rainbow Tables Cracking Lloaddwa Hacking in cyber security refers to the misuse of devices like computers, smartphones, tablets, and networks to cause damage to or corrupt systems, gather information on users, steal data and documents, or disrupt data related activity. The premier ethical hacking course platform for aspiring cybersecurity professionals, offering the latest techniques and insights. become an ethical hacker & security expert. we provide the best training available, coupled with the coaching and support you need.

Rainbow Tables Explained How They Work And Why They Re Mostly Hacking involves using technical skills to break into computer systems and access sensitive data. even though hackers have been around for decades, with our increasing reliance on data and technology, they’ve been playing a far more significant role in recent years. What hacking is and the different motivations behind it—ranging from financial gain and espionage to activism and reputation. the tools and tactics hackers use, including malware, phishing, social engineering, and attacks targeting android devices, macs, and business networks. Security hackers are people involved with circumvention of computer security. there are several types, including: hackers who work to keep data safe from other hackers by finding system vulnerabilities that can be mitigated. An effort to attack a computer system or a private network inside a computer is known as hacking. simply, it is unauthorized access to or control of computer network security systems with the intention of committing a crime.

Rainbow Tables A Path To Password Gold For Cybercriminals Hashed Out Security hackers are people involved with circumvention of computer security. there are several types, including: hackers who work to keep data safe from other hackers by finding system vulnerabilities that can be mitigated. An effort to attack a computer system or a private network inside a computer is known as hacking. simply, it is unauthorized access to or control of computer network security systems with the intention of committing a crime. Hacking is the act of identifying and then exploiting weaknesses in a computer system or network, usually to gain unauthorized access to personal or organizational data. hacking is not always a malicious activity, but the term has mostly negative connotations due to its association with cybercrime. how does hacking work? so, how do hackers hack?. Hacking (also called cyber hacking) is the use of unconventional or illicit means to gain unauthorized access to a digital device, computer system or computer network. Hacking is the act of exploiting system vulnerabilities and compromising the security of digital devices and networks to gain unauthorized access to data. Starthacking is an effort to give more people the tools and resources they need to start building software. whether you are completely new to programming or have already attended a few hackathons, starthacking can help you learn the skills you need for your next project.
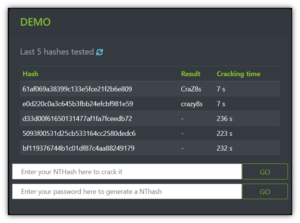
Rainbow Tables A Path To Password Gold For Cybercriminals Hashed Out Hacking is the act of identifying and then exploiting weaknesses in a computer system or network, usually to gain unauthorized access to personal or organizational data. hacking is not always a malicious activity, but the term has mostly negative connotations due to its association with cybercrime. how does hacking work? so, how do hackers hack?. Hacking (also called cyber hacking) is the use of unconventional or illicit means to gain unauthorized access to a digital device, computer system or computer network. Hacking is the act of exploiting system vulnerabilities and compromising the security of digital devices and networks to gain unauthorized access to data. Starthacking is an effort to give more people the tools and resources they need to start building software. whether you are completely new to programming or have already attended a few hackathons, starthacking can help you learn the skills you need for your next project.
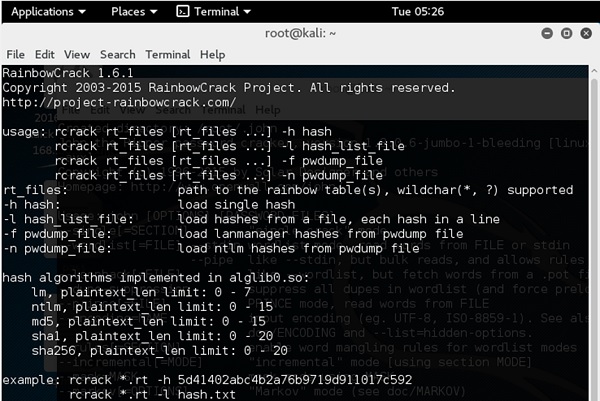
Ethical Hacking Password Hacking Wannahack Hacking is the act of exploiting system vulnerabilities and compromising the security of digital devices and networks to gain unauthorized access to data. Starthacking is an effort to give more people the tools and resources they need to start building software. whether you are completely new to programming or have already attended a few hackathons, starthacking can help you learn the skills you need for your next project.