
Kali Linux How To Use Metasploit Hoolivs Read this expert tutorial on how to use metasploit in kali linux. learn how to download, install, and use metasploit for ethical hacking within kali linux. In this post, we are going to dive into the most popular penetration testing framework metasploit. we will look at 'what is the metasploit framework,' 'the installation process,' and how to use it in ethical hacking. let's get started.

Kali Linux How To Use Metasploit Hoolivs We will demonstrate how to use nmap to perform a basic scan using the localhost ip address. step 1: to view your localhost ip address, run the following command in the terminal. your ip address is displayed as inet xx.x.x.xx in eth0, in our case 10.0.2.15, as shown below. In this article, we’ll look at how this framework within kali linux can be used to attack a windows 10 machine. we will do this through a malicious executable file, using shellter. this article assumes the installation of kali linux has been done and is reachable through a bridged connection from a windows machine on virtualbox. When conducting penetration testing with metasploit on kali linux, it’s crucial to follow structured steps for effective results. this includes setting up a secure test environment, selecting appropriate exploits, and executing attacks carefully to identify vulnerabilities. Metasploit is a powerful tool used for penetration testing, ethical hacking, and vulnerability assessment. it is widely used by cybersecurity professionals and ethical hackers to identify and exploit vulnerabilities in target systems.
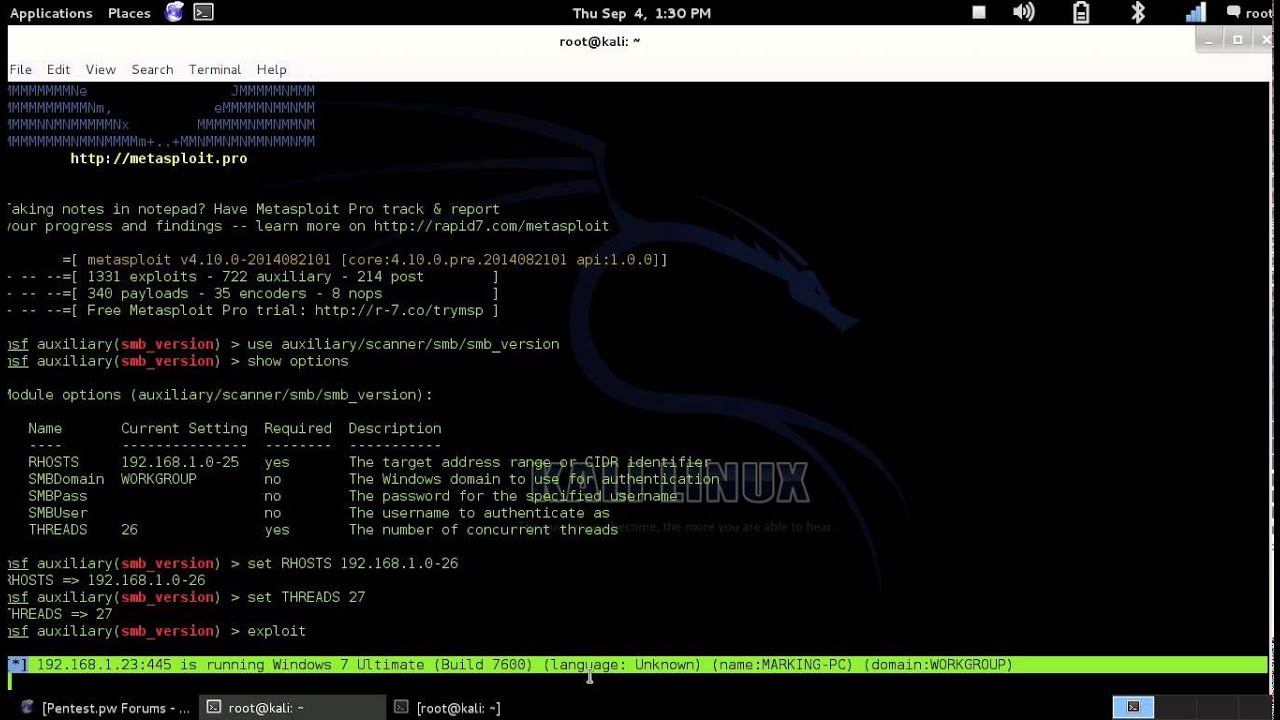
Kali Linux How To Install Metasploit Muslitg When conducting penetration testing with metasploit on kali linux, it’s crucial to follow structured steps for effective results. this includes setting up a secure test environment, selecting appropriate exploits, and executing attacks carefully to identify vulnerabilities. Metasploit is a powerful tool used for penetration testing, ethical hacking, and vulnerability assessment. it is widely used by cybersecurity professionals and ethical hackers to identify and exploit vulnerabilities in target systems. After these have been installed and set up, we will look at using metasploit to gain access to the metasploitable 2 system. we will go step by step, so that everything is clear. my goal is to make this as easy to follow as possible. i will cover every step involved in each of these procedures. Kali linux comes pre installed with metasploit. you can update it using the following commands: curl raw.githubusercontent rapid7 metasploit omnibus master config templates metasploit framework wrappers msfupdate.erb > msfinstall. chmod 755 msfinstall. . msfinstall. msfconsole. download the installer from the rapid7 website. One of the most powerful tools in the ethical hacker's arsenal is metasploit, and when combined with kali linux, it becomes a formidable force. in this guide, we'll walk you through the basics of using metasploit on kali linux, crafted especially for beginners. Today i'm going to show you how we can hack metasploitable virtual machine in 5 different ways to learn penetration testing with nmap and metasploit framework. let's get into it!.

Hack Windows 7 With Metasploit Using Kali Linux Linux Digest After these have been installed and set up, we will look at using metasploit to gain access to the metasploitable 2 system. we will go step by step, so that everything is clear. my goal is to make this as easy to follow as possible. i will cover every step involved in each of these procedures. Kali linux comes pre installed with metasploit. you can update it using the following commands: curl raw.githubusercontent rapid7 metasploit omnibus master config templates metasploit framework wrappers msfupdate.erb > msfinstall. chmod 755 msfinstall. . msfinstall. msfconsole. download the installer from the rapid7 website. One of the most powerful tools in the ethical hacker's arsenal is metasploit, and when combined with kali linux, it becomes a formidable force. in this guide, we'll walk you through the basics of using metasploit on kali linux, crafted especially for beginners. Today i'm going to show you how we can hack metasploitable virtual machine in 5 different ways to learn penetration testing with nmap and metasploit framework. let's get into it!.

How To Use Metasploit In Kali Linux A Step By Step Tutorialёяш Descubra One of the most powerful tools in the ethical hacker's arsenal is metasploit, and when combined with kali linux, it becomes a formidable force. in this guide, we'll walk you through the basics of using metasploit on kali linux, crafted especially for beginners. Today i'm going to show you how we can hack metasploitable virtual machine in 5 different ways to learn penetration testing with nmap and metasploit framework. let's get into it!.