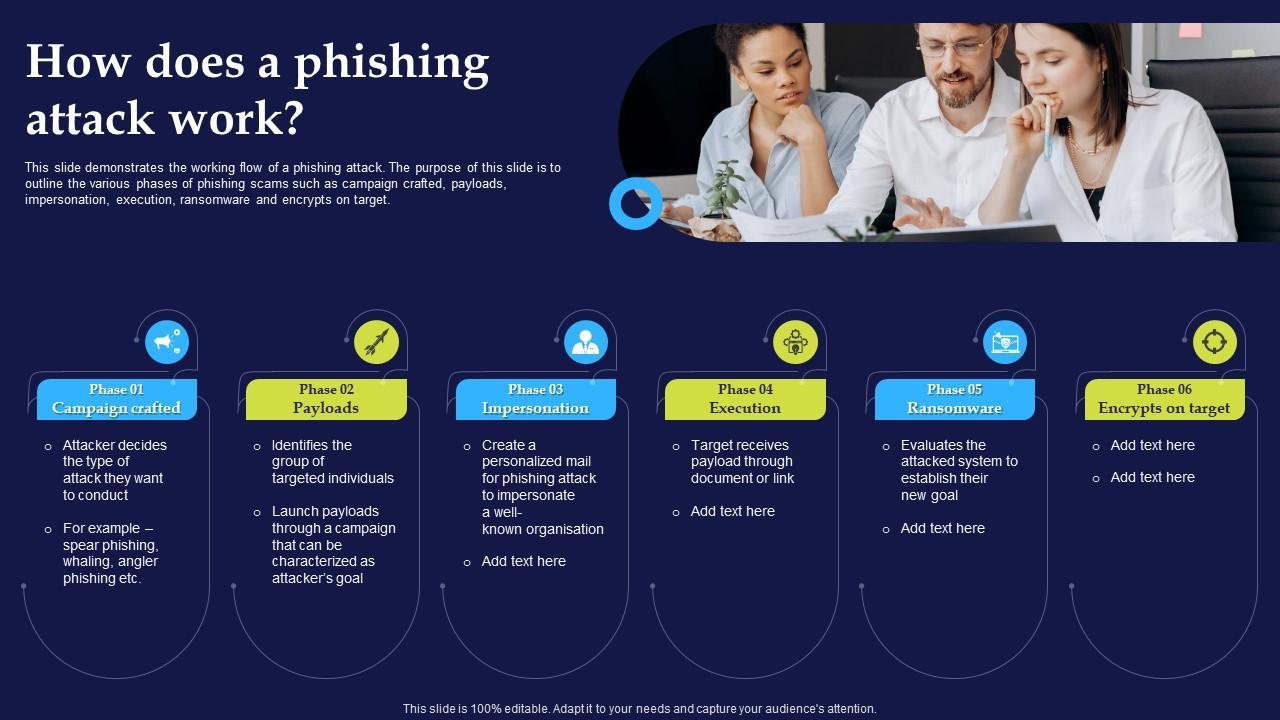
How Does A Phishing Attack Work Phishing Attacks And Strategies Ppt Slide This slide demonstrates the working flow of a phishing attack. the purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. The document provides information on how phishing works, techniques used to detect and prevent it, and tips for users to avoid falling victim to phishing scams.

Phishing Attacks Ppt This slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi factor authentication, and so on. Types of phishing • clone phishing: • phisher creates a clone email • does by getting contents and addresses of recipients and sender • spear phishing: • targeting a specific group of users • all users of that group have something in common • targeting all faculty members of iiti • phone phishing: • call up someone and say you. Phishing email messages, websites, and phone calls are designed to steal money or sensitive information. cybercriminals can do this by installing malicious software on your computer, tricking you into giving them sensitive information, or outright stealing personal information off of your computer. Phishing attacks come in different forms like deceptive, spear, and whaling phishing. users can protect themselves by being educated on how to identify phishing scams and using security technologies like email filters and firewalls.

Phishing Attacks Ppt Phishing email messages, websites, and phone calls are designed to steal money or sensitive information. cybercriminals can do this by installing malicious software on your computer, tricking you into giving them sensitive information, or outright stealing personal information off of your computer. Phishing attacks come in different forms like deceptive, spear, and whaling phishing. users can protect themselves by being educated on how to identify phishing scams and using security technologies like email filters and firewalls. Showcase a multi layered approach for effectively countering phishing attacks with this slide. gain insights into strategies, such as implementing anti spoofing controls, blocking incoming phishing emails, training users, two factor authentication, using proxy servers, and introducing a security logging system. Whaling: a form of spear phishing targeting high profile individuals like c level executives. smishing: phishing attempts via sms or text messages. vishing: voice phishing, where attackers use phone calls to deceive victims. clone phishing: replicating a legitimate email with malicious content. Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. the practices are recognizing hyperlinks attached in an email, backup system copies, secure robust https connections, installing a firewall and using anti spam tools. This slide deck walks you through how to identify scams and phishes, and gives you concrete steps you can take to prevent phishing emails from succeeding.