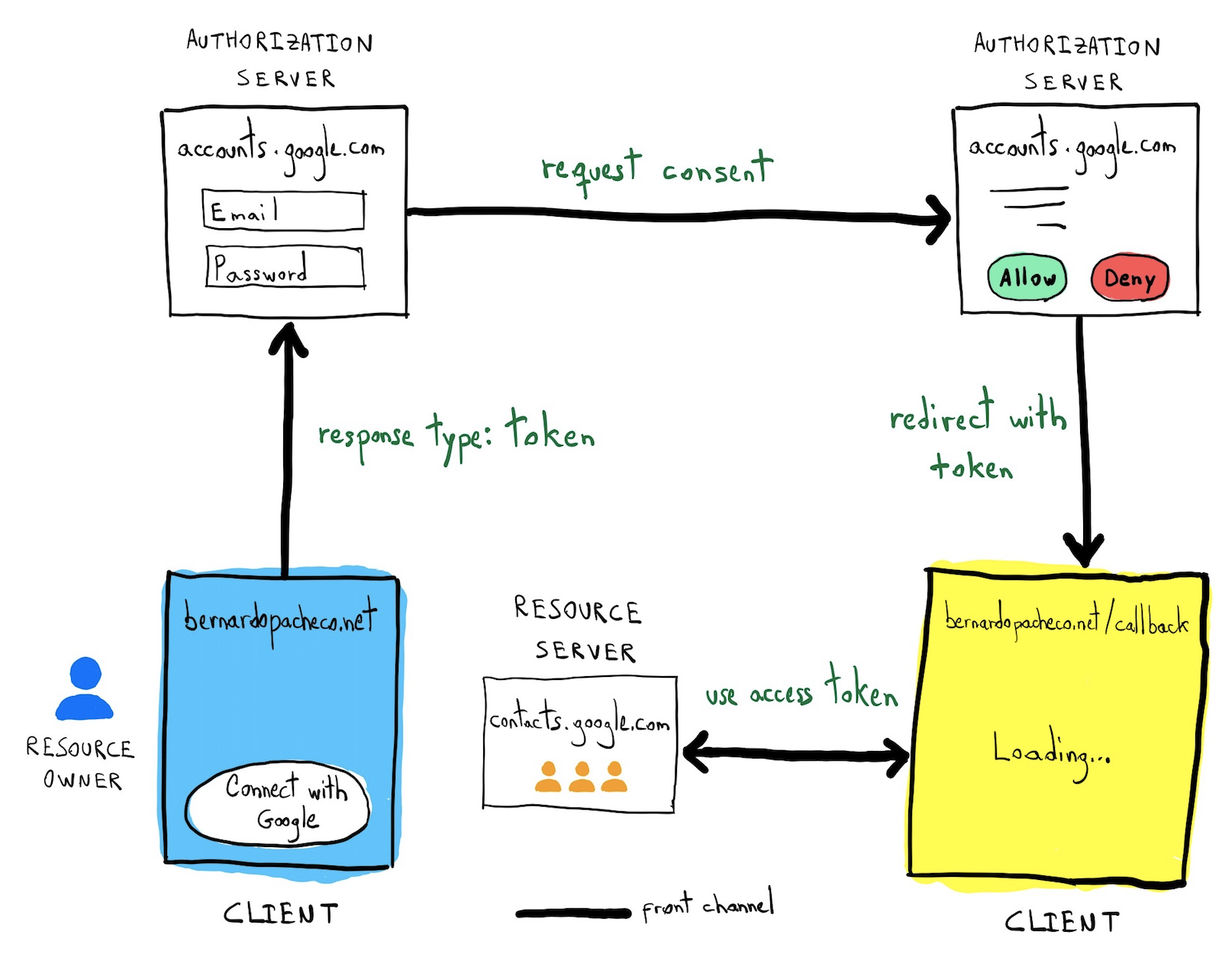
How Oauth 2 0 And Openid Connect Work Bernardo Pacheco It replaced oauth 1.0 in 2012 and is now the de facto industry standard for online authorization. oauth 2.0 provides consented access and restricts actions of what the client app can perform on resources on behalf of the user, without ever sharing the user's credentials. Oauth can be used in conjunction with xacml, where oauth is used for ownership consent and access delegation whereas xacml is used to define the authorization policies (e.g., managers can view documents in their region).
Oauth2 Openid Connect Oauth is a technological standard that allows you to authorize one app or service to sign in to another without divulging private information, such as passwords. Oauth is a technical standard for authorizing users. it is a protocol for passing authorization from one service to another without sharing the actual user credentials, such as a username and password. Oauth (open authorization) is an open standard protocol for authorization of an application for using user information, in general, it allows a third party application access to user related info like name, dob, email or other required data from an application like facebook, google etc. without giving the third party app the user password. Oauth 2.0 is the industry standard protocol for authorization. oauth 2.0 focuses on client developer simplicity while providing specific authorization flows for web applications, desktop applications, mobile phones, and living room devices.

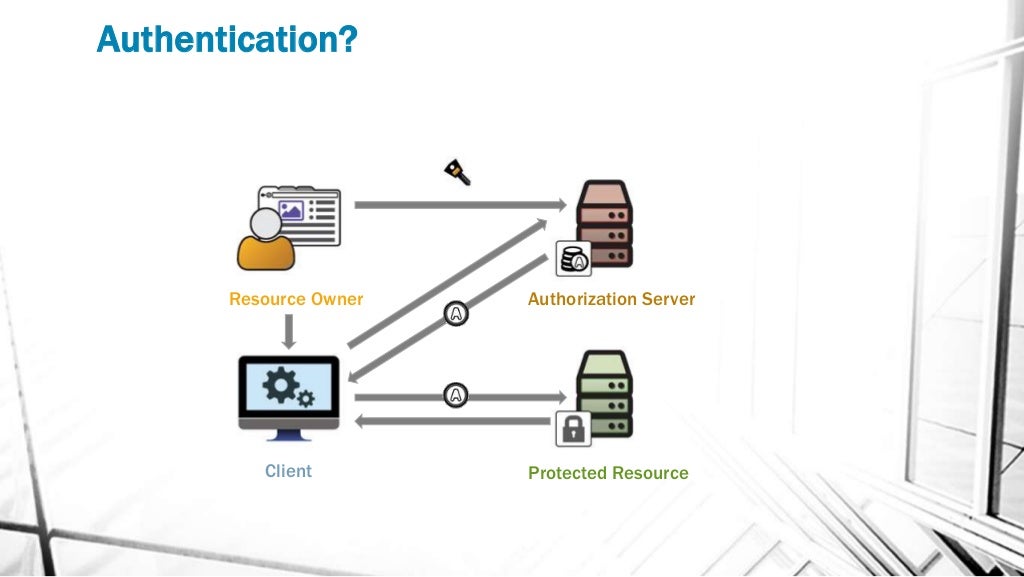
Understanding Oauth2 And Openid Connect Database System Downloading Oauth (open authorization) is an open standard protocol for authorization of an application for using user information, in general, it allows a third party application access to user related info like name, dob, email or other required data from an application like facebook, google etc. without giving the third party app the user password. Oauth 2.0 is the industry standard protocol for authorization. oauth 2.0 focuses on client developer simplicity while providing specific authorization flows for web applications, desktop applications, mobile phones, and living room devices. The open authorization (oauth) 2.0 is the industry protocol for authorization. it allows a user to grant limited access to its protected resources. designed to work specifically with hypertext transfer protocol (http), oauth separates the role of the client from the resource owner. Oauth (open authorization) is an open standard authorization framework for token based authorization on the internet. oauth, which is pronounced "oh auth," enables an end user's account information to be used by third party services, such as facebook and google, without exposing the user's account credentials to the third party. This guide sheds light on the intricacies of oauth 2.0, highlighting the main roles involved, its operational flows, the use of tokens, and best practices for implementation to ensure safe delegated access. Curious about oauth? understand what is oauth authentication and how does it work in real world scenarios. explore how it helps it teams enforce granular access controls and improve user experience.

Oauth 2 Vs Openid Connect Api University The open authorization (oauth) 2.0 is the industry protocol for authorization. it allows a user to grant limited access to its protected resources. designed to work specifically with hypertext transfer protocol (http), oauth separates the role of the client from the resource owner. Oauth (open authorization) is an open standard authorization framework for token based authorization on the internet. oauth, which is pronounced "oh auth," enables an end user's account information to be used by third party services, such as facebook and google, without exposing the user's account credentials to the third party. This guide sheds light on the intricacies of oauth 2.0, highlighting the main roles involved, its operational flows, the use of tokens, and best practices for implementation to ensure safe delegated access. Curious about oauth? understand what is oauth authentication and how does it work in real world scenarios. explore how it helps it teams enforce granular access controls and improve user experience.