
Reverse Shell1 Pdf Port Computer Networking Security Hacker A reverse shell is a powerful tool in ethical hacking that allows attack ers to gain remote access to a target machine. by understanding how reverse shells work, ethical hackers can identify vulnerabilities in systems and network s, simulating real world attack s and helping organisations strengthen their defences. Reverse shells are commonly used in scenarios where the victim’s machine is behind a firewall or nat (network address translation). the attacker sets up a listener on their machine, often on a.

Reverse Shells From Payloads Packt Secpro In the first part, i will show you some encoding techniques to bypass application firewall filtering. next, we will create a list of multiple reverse shells and encode them all together into a “master” copy pastable. This ethical hacking guide explains what is a reverse shell attack, how to create a reverse shell with examples using netcat, php, python and bash and how to prevent and mitigate it in cyber security. A reverse shell is essentially a backdoor that bypasses the usual security measures put in place by system administrators. it allows the attacker to execute commands, upload or download files, and access sensitive data on the compromised system. How does a reverse shell attack work? preparation for a reverse shell attack begins with the attacker setting up a listening server, configuring it to run a command line interpreter (more commonly referred to as a ‘shell’) that can be used to run commands on the victim’s machine.
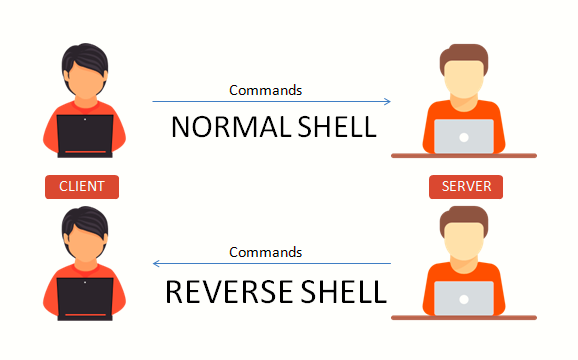
Reverse Shell Between Two Linux Machines Yeah Hub A reverse shell is essentially a backdoor that bypasses the usual security measures put in place by system administrators. it allows the attacker to execute commands, upload or download files, and access sensitive data on the compromised system. How does a reverse shell attack work? preparation for a reverse shell attack begins with the attacker setting up a listening server, configuring it to run a command line interpreter (more commonly referred to as a ‘shell’) that can be used to run commands on the victim’s machine. By leveraging this unique method, reverse shells allow attackers to bypass firewalls, intrusion detection systems, and other security measures that typically monitor for incoming connections. in essence, reverse shells turns the tables on conventional security systems. Reverse shells are an indispensable tool in cyber security and it forensics. they allow an attacker to execute commands on a compromised machine from outside the target network without the need for a direct connection to the target system. How does a reverse shell work? a reverse shell operates by creating a connection between the target system and the attacker’s machine. typically, the target machine initiates this connection by sending a request to the attacker’s machine. This article explains how reverse shells work, the tools used to execute them, and the risks associated with these attacks. a reverse shell is a type of remote access method where a compromised system initiates a connection to an attacker’s machine, allowing the attacker to execute commands remotely.

Reverse Shells Cocomelonc By leveraging this unique method, reverse shells allow attackers to bypass firewalls, intrusion detection systems, and other security measures that typically monitor for incoming connections. in essence, reverse shells turns the tables on conventional security systems. Reverse shells are an indispensable tool in cyber security and it forensics. they allow an attacker to execute commands on a compromised machine from outside the target network without the need for a direct connection to the target system. How does a reverse shell work? a reverse shell operates by creating a connection between the target system and the attacker’s machine. typically, the target machine initiates this connection by sending a request to the attacker’s machine. This article explains how reverse shells work, the tools used to execute them, and the risks associated with these attacks. a reverse shell is a type of remote access method where a compromised system initiates a connection to an attacker’s machine, allowing the attacker to execute commands remotely.

Reverse Shells Cocomelonc How does a reverse shell work? a reverse shell operates by creating a connection between the target system and the attacker’s machine. typically, the target machine initiates this connection by sending a request to the attacker’s machine. This article explains how reverse shells work, the tools used to execute them, and the risks associated with these attacks. a reverse shell is a type of remote access method where a compromised system initiates a connection to an attacker’s machine, allowing the attacker to execute commands remotely.

Reverse Shells Cocomelonc