Deep Analysis Of Vidar Information Stealer Eln0ty Named after the god of vengeance from scandinavian mythology, vidar is used to steal information from infected machines, take screenshots, steal cryptocurrency, and more. Vidar is an information stealer trojan. it is either a fork of vidar or the result of its evolution. follow live malware statistics of this trojan and get new reports, samples, iocs, etc.

Vidar Malware Spreads By Tricking Users Into Downloading Fake Versions Our new blog post shows how we successfully use wazuh to detect vidar infostealer on an infected windows endpoint. By doing this, malware authors can avoid hardcoding c2 addresses in their malware, making detection and takedown efforts more challenging. i observed that the stealer uses two well known sites — steam and telegram. When the request is finely crafted, vidar is simply using shellexecutea to pop a command shell and execute the task, this erases all trace of the interaction of the payload on the machine and delete all downloaded dlls. Analyse suspicious files, domains, ips and urls to detect malware and other breaches, automatically share them with the security community.
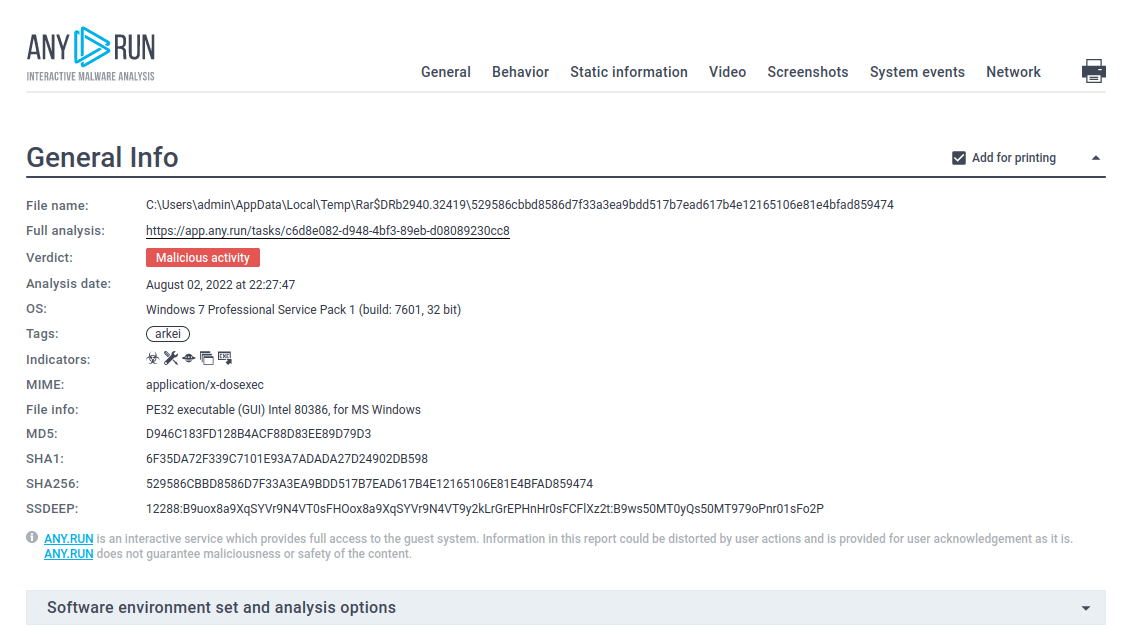
Vidar Trojan Analysis Malware Overview By Any Run When the request is finely crafted, vidar is simply using shellexecutea to pop a command shell and execute the task, this erases all trace of the interaction of the payload on the machine and delete all downloaded dlls. Analyse suspicious files, domains, ips and urls to detect malware and other breaches, automatically share them with the security community. It uses adaptive threat analysis technology to detect evasive malware and extract relevant indicators of compromise (iocs). our threat agnostic scanning supports a wide variety of files and urls to identify iocs swiftly and efficiently. Submit malware for free analysis with falcon sandbox and hybrid analysis technology. hybrid analysis develops and licenses analysis tools to fight malware. Explore vidar, a windows based info stealing malware. learn about its data theft capabilities, distribution methods, and mitigation strategies. Vidar uses tricks to avoid instant detection by both in system antivirus software and analysis sites like virustotal.
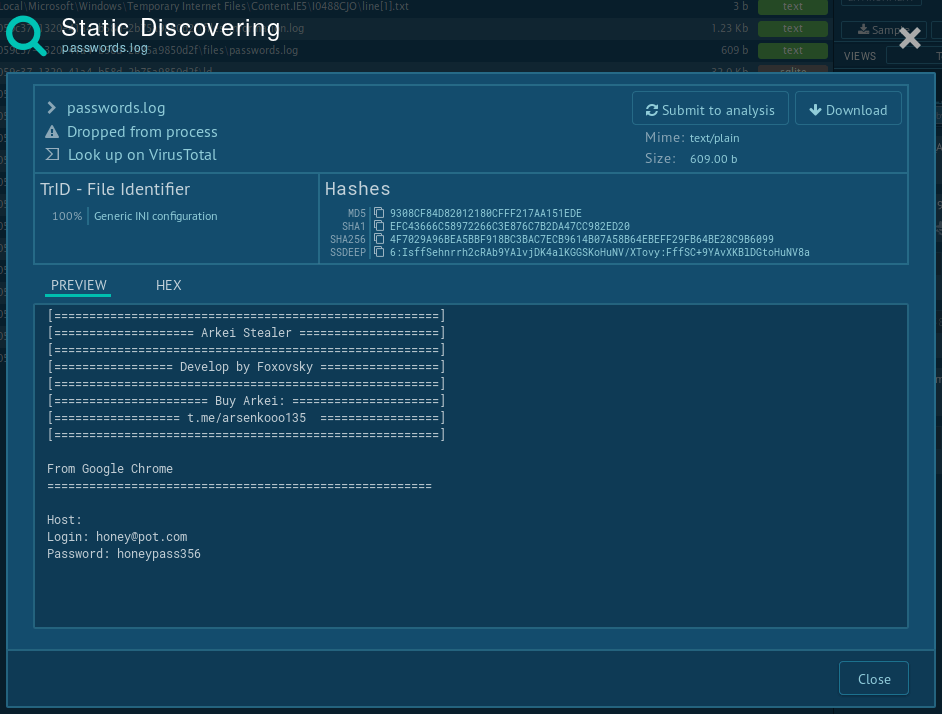
Vidar Trojan Analysis Malware Overview By Any Run It uses adaptive threat analysis technology to detect evasive malware and extract relevant indicators of compromise (iocs). our threat agnostic scanning supports a wide variety of files and urls to identify iocs swiftly and efficiently. Submit malware for free analysis with falcon sandbox and hybrid analysis technology. hybrid analysis develops and licenses analysis tools to fight malware. Explore vidar, a windows based info stealing malware. learn about its data theft capabilities, distribution methods, and mitigation strategies. Vidar uses tricks to avoid instant detection by both in system antivirus software and analysis sites like virustotal.