What Are The Best Ways To Prevent Cyber Attacks That Bypass Multi Perhaps penetration testing is the most effective way to prevent authentication bypass vulnerabilities. in penetration testing, it security professionals simulate an attack against a given system or network, probing it for various flaws and holes. Learn what an authentication bypass vulnerability is, how it works, and proven ways to prevent unauthorized access and protect your systems.

How To Prevent Authentication Bypass Attacks Authentication bypass is a vulnerable point where criminals gain access to the application and get users’ sensitive information. authentication bypass vulnerability allows hackers to perform malicious activities by bypassing the authentication mechanism of the devices. In this article, we shall discuss common techniques that hackers adopt and how you can put measures in place to protect yourself from such attacks in simple terms. Implementing multi factor authentication (mfa) is a simple and effective process that organizations can use to reduce their risk of security breach. in fact, research from microsoft has found that taking this one simple step can stop 99.9% of attacks on your account. Recognizing these common causes is crucial for effective prevention. many authentication bypasses stem from flawed session management: token verification: always validate token authenticity and integrity. cookie checks: ensure cookies are securely validated server side. session ids: use strong, unpredictable session identifiers.
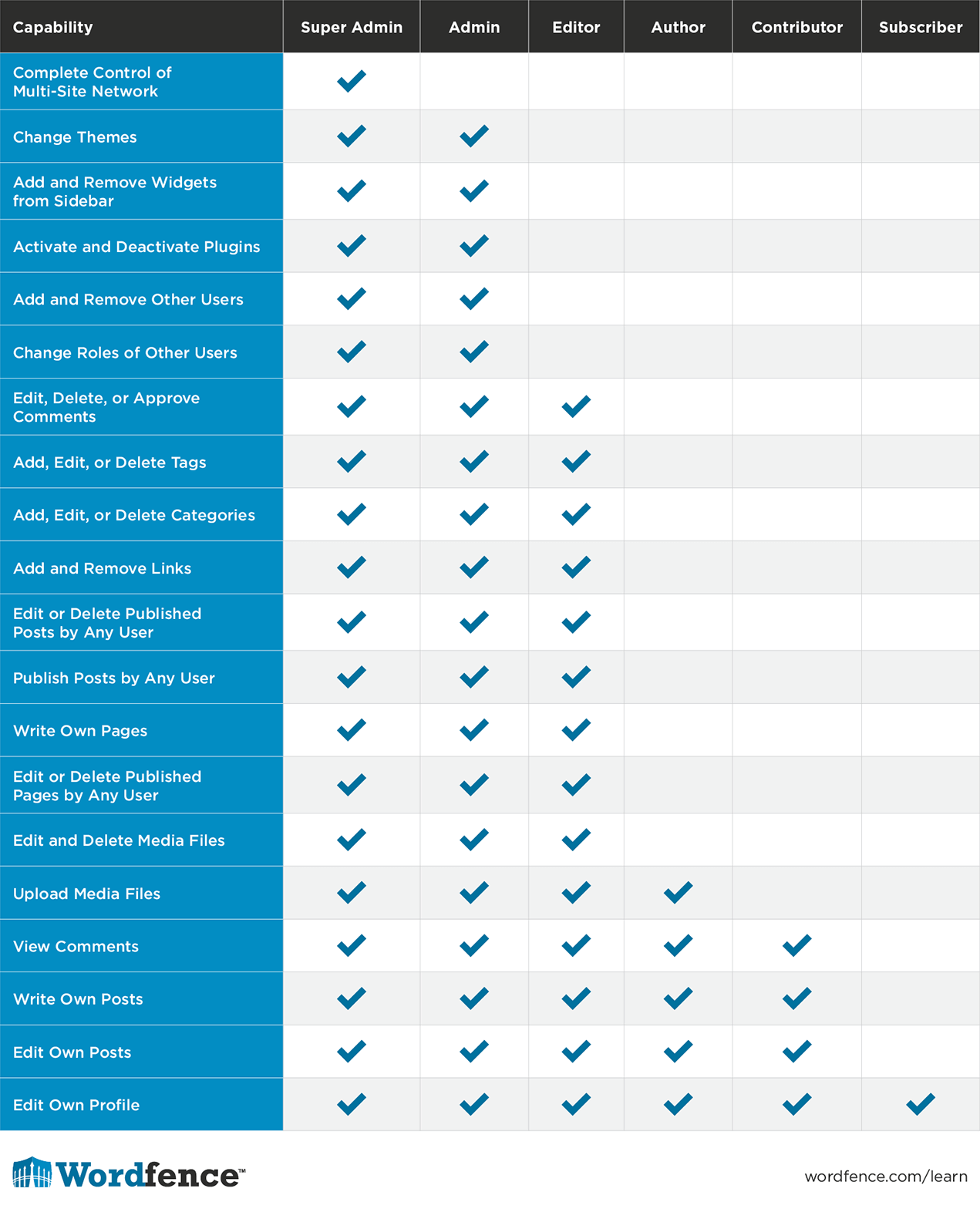
How To Prevent Authentication Bypass Attacks Implementing multi factor authentication (mfa) is a simple and effective process that organizations can use to reduce their risk of security breach. in fact, research from microsoft has found that taking this one simple step can stop 99.9% of attacks on your account. Recognizing these common causes is crucial for effective prevention. many authentication bypasses stem from flawed session management: token verification: always validate token authenticity and integrity. cookie checks: ensure cookies are securely validated server side. session ids: use strong, unpredictable session identifiers. Below are six common ways cybercriminals can bypass mfa. hackers can also use these methods to bypass two factor authentication. 1. social engineering. social engineering involves tricking a victim into revealing privileged information that can be leveraged in a cyber attack. How to prevent authentication bypass attacks there are two common options that organizations typically leverage to prevent these kinds of vulnerabilities and attacks:. In this article, we will delve into two methods of web app authentication bypass and outline the preventive techniques that developers can use to stop attackers in their tracks. penetration. Implementing robust security measures is crucial to prevent authentication bypass vulnerabilities. here are some key strategies: implement multi factor authentication (mfa): mfa adds an extra layer of security, making it significantly harder for attackers to bypass authentication.
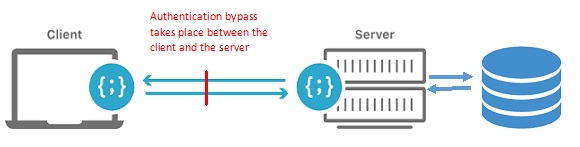
Best Vapt Company Authentication Bypass Attack Pune Mumbai Below are six common ways cybercriminals can bypass mfa. hackers can also use these methods to bypass two factor authentication. 1. social engineering. social engineering involves tricking a victim into revealing privileged information that can be leveraged in a cyber attack. How to prevent authentication bypass attacks there are two common options that organizations typically leverage to prevent these kinds of vulnerabilities and attacks:. In this article, we will delve into two methods of web app authentication bypass and outline the preventive techniques that developers can use to stop attackers in their tracks. penetration. Implementing robust security measures is crucial to prevent authentication bypass vulnerabilities. here are some key strategies: implement multi factor authentication (mfa): mfa adds an extra layer of security, making it significantly harder for attackers to bypass authentication.
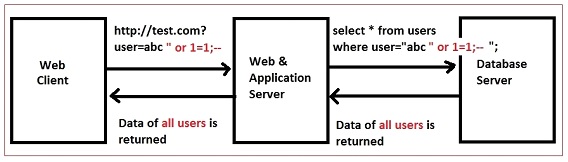
Best Vapt Company Authentication Bypass Attack Pune Mumbai In this article, we will delve into two methods of web app authentication bypass and outline the preventive techniques that developers can use to stop attackers in their tracks. penetration. Implementing robust security measures is crucial to prevent authentication bypass vulnerabilities. here are some key strategies: implement multi factor authentication (mfa): mfa adds an extra layer of security, making it significantly harder for attackers to bypass authentication.
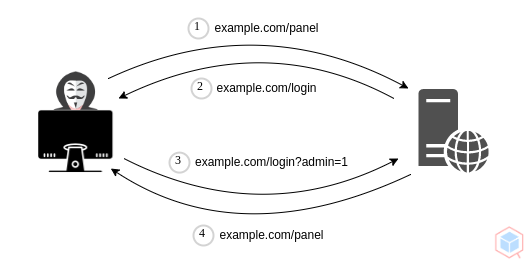
Github Qeeqbox Authentication Bypass A Threat Actor May Gain Access



Comments are closed.