
How To Store Refresh Tokens Securely In The Database 7 day refresh token for one time usage: generate random secret (don't need to sign it encrypt it), store it in redis with a 7 day ttl (or mysql with a valid until timestamp). I'm building a website with patreon integration and i have identified the need to store patreon user's oauth2 token in the database. i'm wondering what's the best way to do that, security wise.
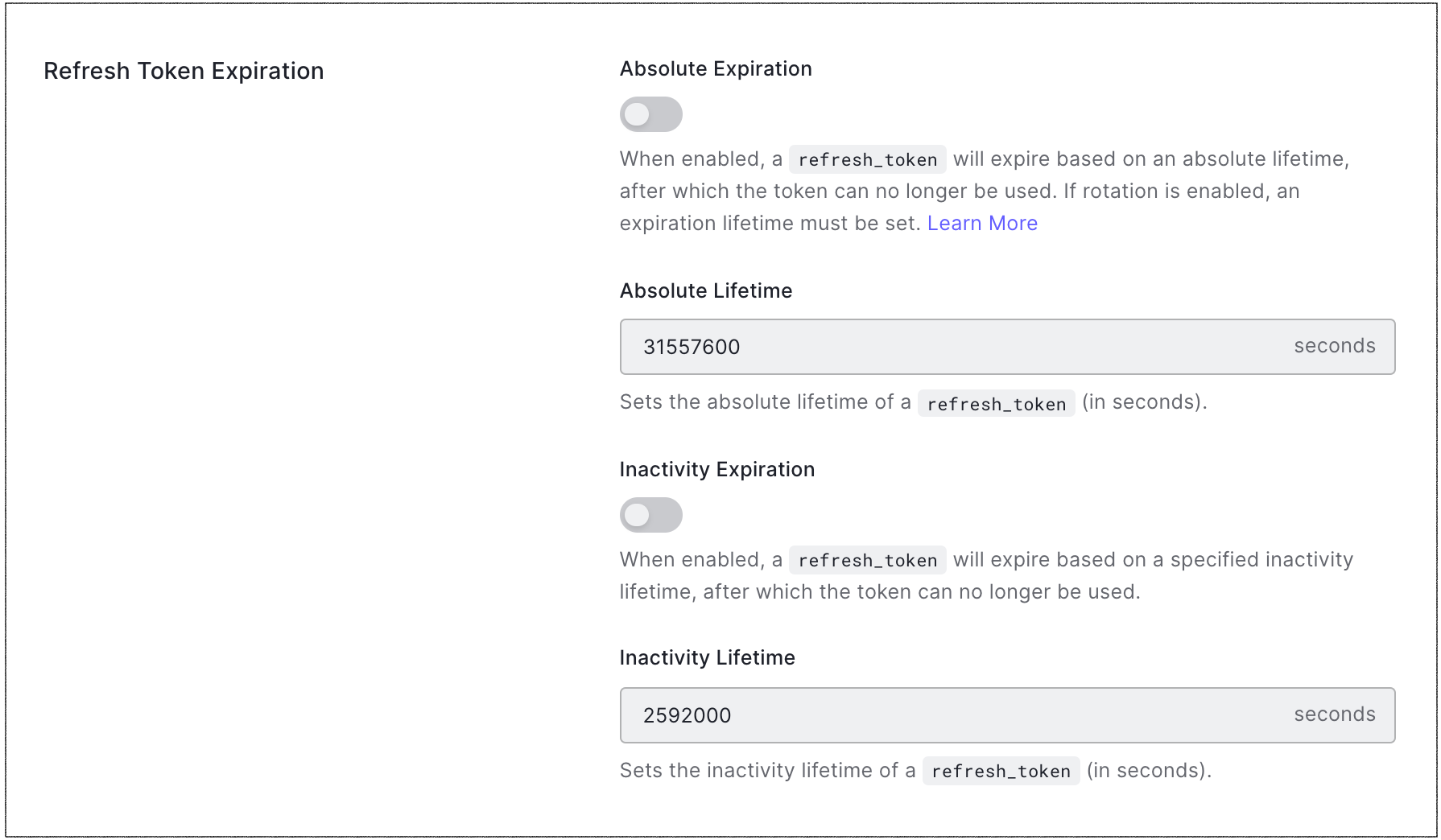
Configure Refresh Token Expiration Here’s how you can store refresh tokens in a database: database table: create a table in your database with columns for user id and refresh token. this table will store the associations between users and their refresh tokens. In oauth 2.0, you control access to your application's protected resources by using access tokens. access tokens are the credentials representing the authorization given to an application. they contain the granted permissions in the form of scopes with a specific duration. Refresh tokens, with longer lifespans, allow clients to request new access tokens without requiring the user to log in again. ensure the following dependencies in your pom.xml. update the jwtutil class to handle access and refresh tokens separately. import io.jsonwebtoken.*; .setsubject(username) . .setissuedat(new date()) . It’s a long lived token stored securely (often in http only cookies) that allows the client to request a new access token when the current one expires. [key].
Configure Refresh Token Expiration Refresh tokens, with longer lifespans, allow clients to request new access tokens without requiring the user to log in again. ensure the following dependencies in your pom.xml. update the jwtutil class to handle access and refresh tokens separately. import io.jsonwebtoken.*; .setsubject(username) . .setissuedat(new date()) . It’s a long lived token stored securely (often in http only cookies) that allows the client to request a new access token when the current one expires. [key]. Storing tokens in browser local storage provides persistence across page refreshes and browser tabs; however, if malicious users managed to run javascript in the spa using a cross site scripting (xss) attack, they could retrieve the tokens stored in local storage. We can encrypt refresh tokens before storing them in the database. in this case, we need to somehow securely store and manage the secret keys that we will use for encryption decryption. to do this,. Access tokens and refresh tokens are common solutions to ensure security, scalability, and user friendly experiences. in this blog, we’ll explain how to use these tokens in a webforms application with step by step guidance. a short lived token (e.g., 5 minute) used to authenticate api requests. In this article, we will discuss how to store jwt refresh tokens in a database using identity and ef core in an asp core application. adding a refresh token entity. next, we will create a new entity for our refresh tokens. in the models folder, create a new class called refreshtoken.cs and add the following code:.
Github Sranvare007 Refresh Tokens Auth Storing tokens in browser local storage provides persistence across page refreshes and browser tabs; however, if malicious users managed to run javascript in the spa using a cross site scripting (xss) attack, they could retrieve the tokens stored in local storage. We can encrypt refresh tokens before storing them in the database. in this case, we need to somehow securely store and manage the secret keys that we will use for encryption decryption. to do this,. Access tokens and refresh tokens are common solutions to ensure security, scalability, and user friendly experiences. in this blog, we’ll explain how to use these tokens in a webforms application with step by step guidance. a short lived token (e.g., 5 minute) used to authenticate api requests. In this article, we will discuss how to store jwt refresh tokens in a database using identity and ef core in an asp core application. adding a refresh token entity. next, we will create a new entity for our refresh tokens. in the models folder, create a new class called refreshtoken.cs and add the following code:.
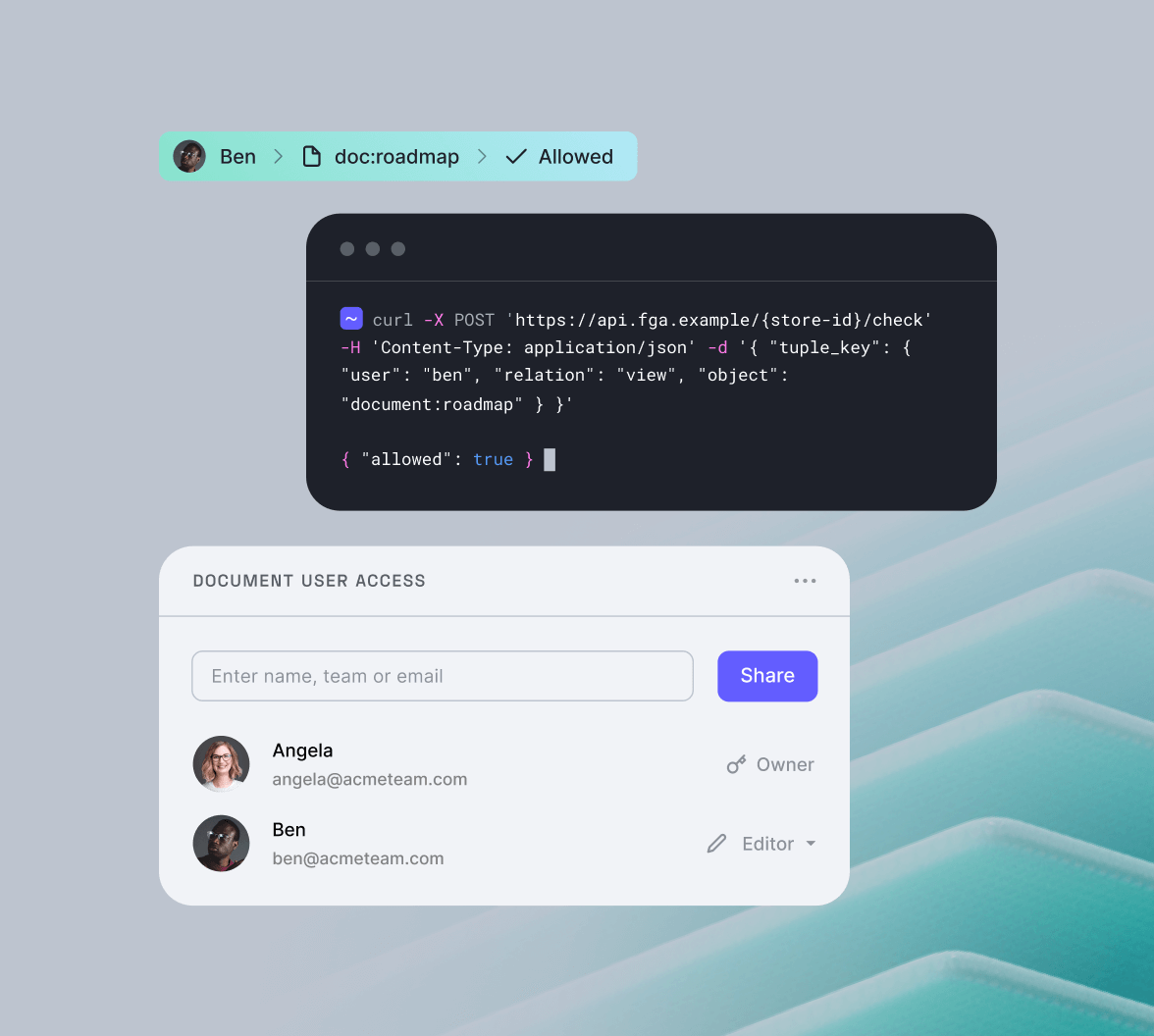
Understanding Refresh Tokens Access tokens and refresh tokens are common solutions to ensure security, scalability, and user friendly experiences. in this blog, we’ll explain how to use these tokens in a webforms application with step by step guidance. a short lived token (e.g., 5 minute) used to authenticate api requests. In this article, we will discuss how to store jwt refresh tokens in a database using identity and ef core in an asp core application. adding a refresh token entity. next, we will create a new entity for our refresh tokens. in the models folder, create a new class called refreshtoken.cs and add the following code:.