
A New Way Of Design And Implementation Of Hybrid Encryption Pdf A hybrid cryptosystem is a public key system that combines the convenience of a public key cryptosystem with the efficiency of a symmetric key cryptosystem. learn how hybrid cryptosystems work, their security properties, and their applications in cloud computing and protocols. Hybrid encryption combines symmetric and asymmetric encryption, leveraging the speed and security of both methods. learn how it works, why it is effective, and how it differs from traditional encryption methods.

Hybrid Encryption Hybrid encryption is an approach to encoding and decoding data that blends the speed and convenience of a public asymmetric encryption scheme with the effectiveness of a private symmetric encryption scheme. the final form of encryption is hybrid encryption. Hybrid encryption is a cryptographic method that combines the strengths of both symmetric and asymmetric encryption to provide efficient and secure communication. this approach leverages the speed of symmetric encryption and the security of asymmetric encryption. here’s a detailed explanation of how hybrid encryption works and its benefits:. Learn how to use hybrid encryption to combine symmetric and public key cryptography for efficient and convenient data encryption. see key types, properties, use cases, and examples of hybrid encryption in tink. A hybrid cryptosystem is a cryptographic system that combines symmetric and asymmetric encryption to secure data transmission. learn how it works, its benefits, challenges, and examples of its applications in secure email, data encryption, and vpns.
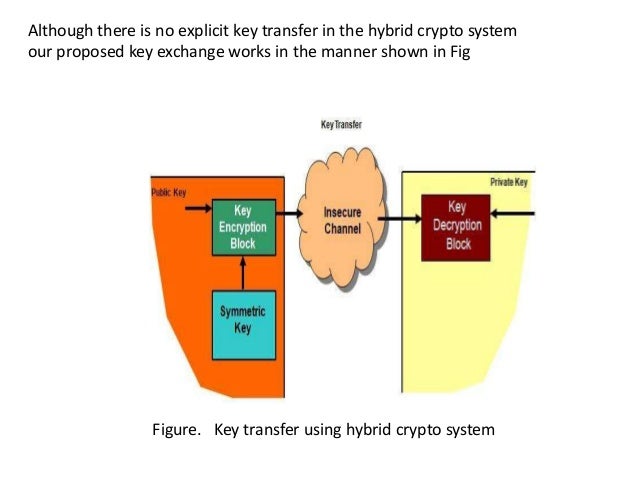
Hybrid Encryption Learn how to use hybrid encryption to combine symmetric and public key cryptography for efficient and convenient data encryption. see key types, properties, use cases, and examples of hybrid encryption in tink. A hybrid cryptosystem is a cryptographic system that combines symmetric and asymmetric encryption to secure data transmission. learn how it works, its benefits, challenges, and examples of its applications in secure email, data encryption, and vpns. Hybrid encryption combines public key and symmetric algorithms to compensate for weaknesses in single post quantum solutions. learn the advantages, disadvantages, and challenges of this approach from cryptographers and experts. Hybrid encryption main idea use public key encryption to establish a (shared, secret) key k use k to encrypt the message with a symmetric key encryption scheme benefits lower ciphertext expansion amortized efficiency of symmetric key encryption. In the current scenario, various forms of information are spread everywhere, especially through the internet. a lot of valuable information is contained in the. By combining the strengths of different encryption techniques, hybrid encryption not only safeguards your data but also optimizes performance. join us as we explore this innovative approach to data protection and discover why it’s rapidly becoming the gold standard in cybersecurity.

Hybrid Encryption Hybrid encryption combines public key and symmetric algorithms to compensate for weaknesses in single post quantum solutions. learn the advantages, disadvantages, and challenges of this approach from cryptographers and experts. Hybrid encryption main idea use public key encryption to establish a (shared, secret) key k use k to encrypt the message with a symmetric key encryption scheme benefits lower ciphertext expansion amortized efficiency of symmetric key encryption. In the current scenario, various forms of information are spread everywhere, especially through the internet. a lot of valuable information is contained in the. By combining the strengths of different encryption techniques, hybrid encryption not only safeguards your data but also optimizes performance. join us as we explore this innovative approach to data protection and discover why it’s rapidly becoming the gold standard in cybersecurity.

Hybrid Encryption In the current scenario, various forms of information are spread everywhere, especially through the internet. a lot of valuable information is contained in the. By combining the strengths of different encryption techniques, hybrid encryption not only safeguards your data but also optimizes performance. join us as we explore this innovative approach to data protection and discover why it’s rapidly becoming the gold standard in cybersecurity.