Asp Net Core Cookie Jwt Authentication Combined I'm trying to implement an authentication scheme in my app. the controller, more specifically the method, responsible for checking user's credentials and generating jwt which it has to put into the httponly cookie afterward looks as follows. [httppost] [route("authenticate")] public async task

Javascript Cannot Create Httponly Cookie Containing Jwt In Asp Net In this guide, i’ll show you how to implement jwt authentication using httponly cookies in a 9 web api — a secure, scalable approach that avoids the pitfalls of localstorage and keeps your tokens safe from xss attacks. In this article, we will show you how to use httponly cookie in core apps to secure our jwt or json web tokens, when implementing the authentication and refresh token actions. Jwt request that requires authentication response is 401. a cookie request that requires authentication response is a redirect to the login page. you have set the default to jwt. normally in a mixed environment you would use jwt for api requests and cookie for razor page requests. then you would use different policies. Http only cookie option is used to secure cookie and used to protect the cookie from retrieve from malicious xss script. to secure cookies from unwanted use then the security policy is used for modern browsers.
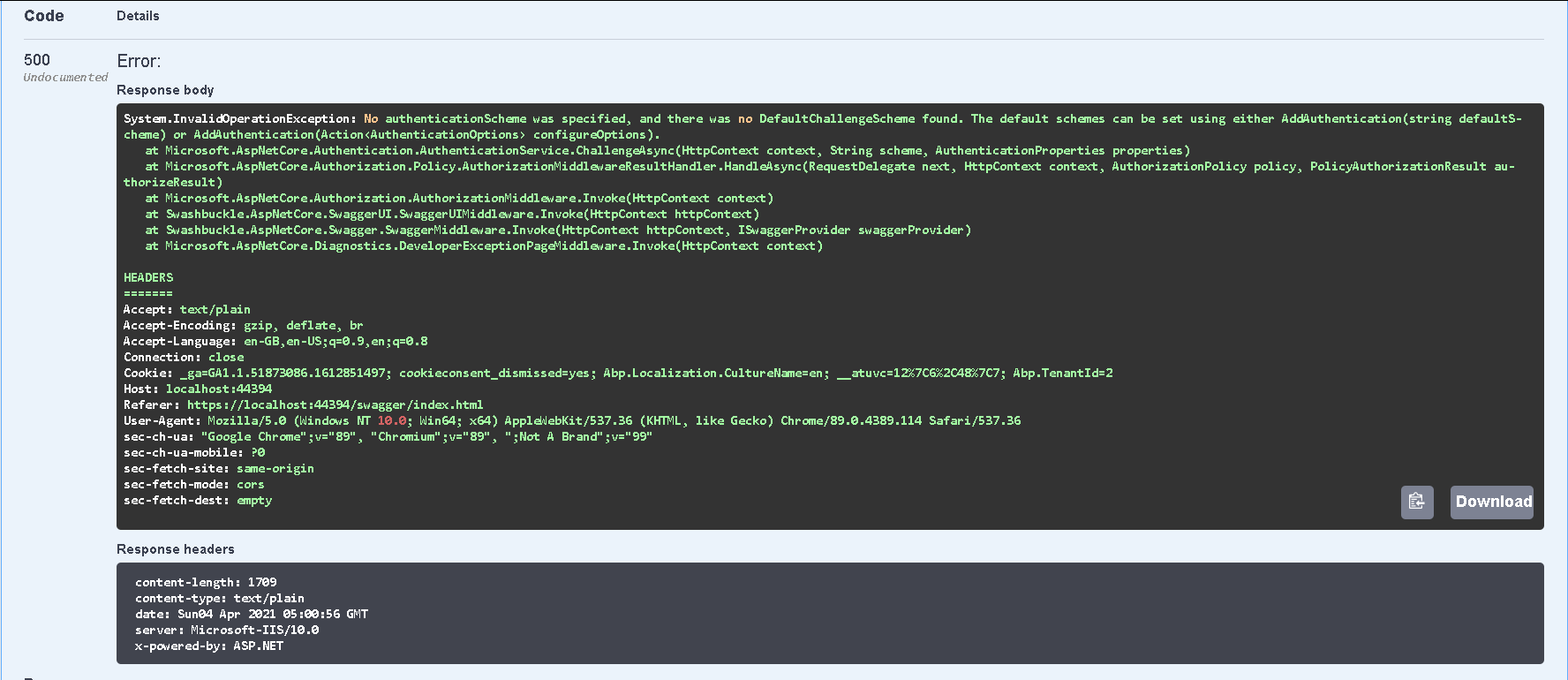
How To Implement Jwt Token Authentication In Asp Net Core 5 Using Jwt Jwt request that requires authentication response is 401. a cookie request that requires authentication response is a redirect to the login page. you have set the default to jwt. normally in a mixed environment you would use jwt for api requests and cookie for razor page requests. then you would use different policies. Http only cookie option is used to secure cookie and used to protect the cookie from retrieve from malicious xss script. to secure cookies from unwanted use then the security policy is used for modern browsers. In this post i will show one way to mix jwt token authentication with cookie authentication using asp core and send out the jwt in a response cookie. Summary create in box support for authn with jwt stored in http only cookies motivation and goals then we develop spa application with asp core (for ex. with react at frontend) we very often think about how we implement authenticatio. This post discusses how to combine cookie authentication with jwt bearer authentication in an asp core application without manipulating the token in any way – like it is suggested in several articles on the web. As i mentioned above, after cookie with httponly flag you couldn't access the token on client side. xmlhttprequest will access those cookies for us. whenever there is a request the xmlhttprequest sends all the cookies to the server side. note: if your authentication server is separated from your website.