
Jwt Security 101 How To Defend Against Common Attacks On Json Web To mitigate jwt based attacks, it’s important to use strong signing keys and algorithms, as well as using proper storage and transmission methods, such as https. also, it’s crucial to. In this section, we'll look at how design issues and flawed handling of json web tokens (jwts) can leave websites vulnerable to a variety of high severity attacks. as jwts are most commonly used in authentication, session management, and access control mechanisms, these vulnerabilities can potentially compromise the entire website and its users.
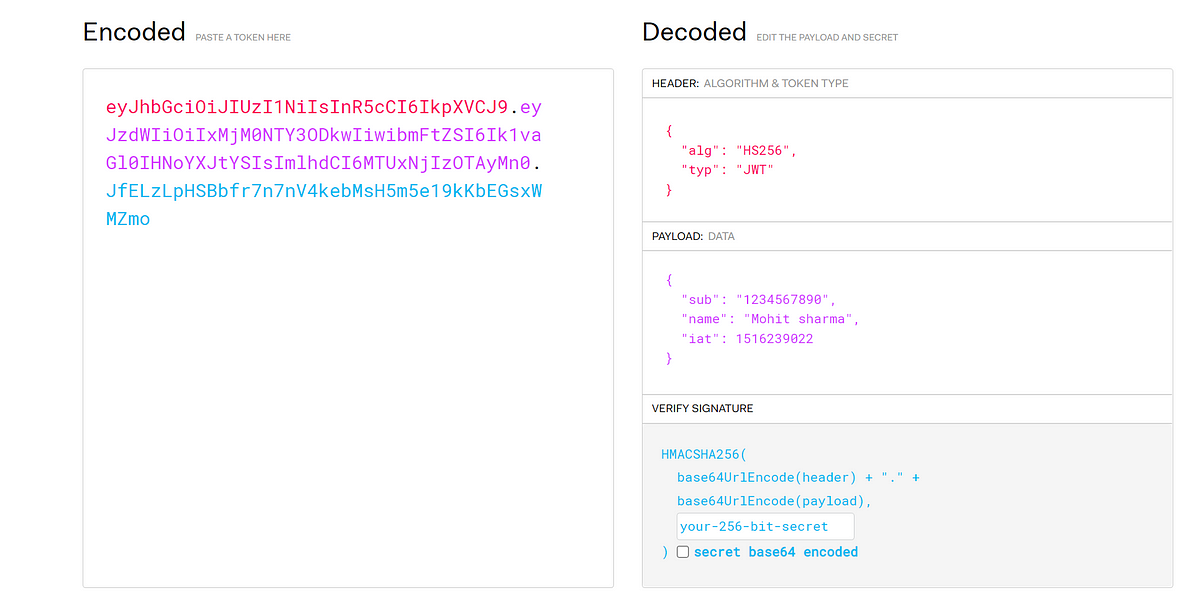
Jwt Security 101 How To Defend Against Common Attacks On Json Web Master jwt security with this in depth guide to web hacking and appsec. learn how to exploit and defend against real world jwt vulnerabilities like algorithm confusion, weak secrets, and kid injection — with hands on labs from pentesterlab. Deep dive into common jwt security vulnerabilities and learn how to prevent replay attacks, key leaks, signature forgery and other security issues. provides practical security recommendations and best practices. Discover how json web tokens (jwt) revolutionize web authentication. this guide covers everything from basic concepts to advanced security measures, helping you implement secure, scalable authentication in modern applications. Security professionals need to understand common jwt vulnerabilities and testing methodologies to identify potential weaknesses before malicious actors can exploit them. this article outlines practical approaches to jwt penetration testing, including tools, techniques, and remediation strategies for common security issues.
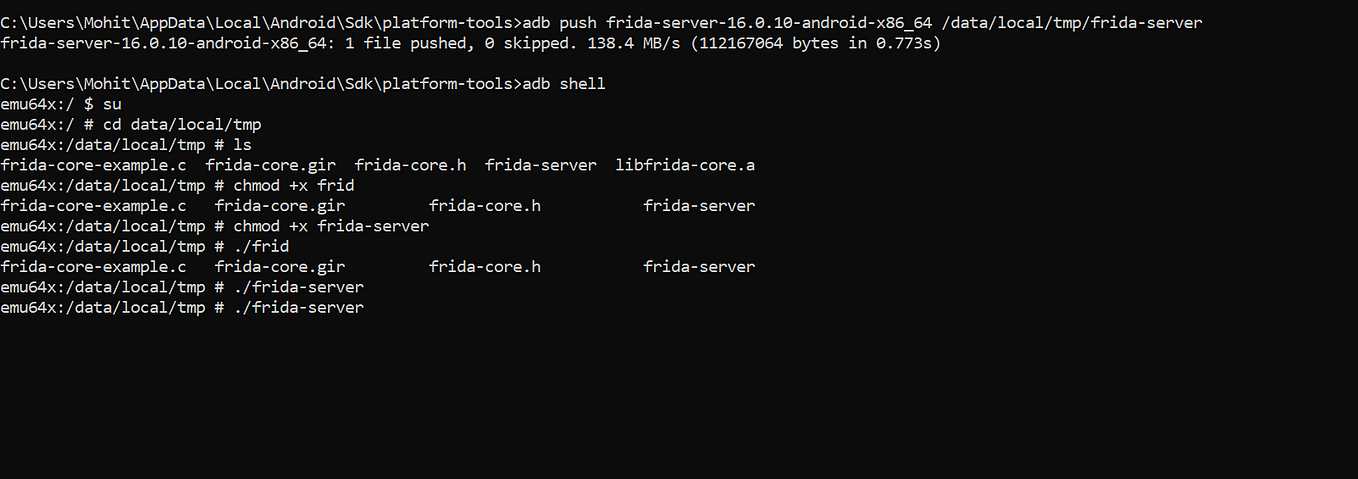
Jwt Security 101 How To Defend Against Common Attacks On Json Web Discover how json web tokens (jwt) revolutionize web authentication. this guide covers everything from basic concepts to advanced security measures, helping you implement secure, scalable authentication in modern applications. Security professionals need to understand common jwt vulnerabilities and testing methodologies to identify potential weaknesses before malicious actors can exploit them. this article outlines practical approaches to jwt penetration testing, including tools, techniques, and remediation strategies for common security issues. Learn how to enhance the security of your web applications with robust strategies for managing json web tokens (jwts). from using strong algorithms and handling token storage securely to implementing effective validation techniques, this guide covers all you need to know to safeguard your applications against vulnerabilities. Jwt storage cookie xss protections (httponly & secure flags) are not available for browser local session storage. best practice memory only jwt token handling. protection of the crypto keys (server side). protection against csrf it’s not jwt tokens, it’s about how you use them. memory only jwt & usability. jwt token verification. I've seen too many developers fall into the same traps—using weak secrets, trusting unsigned tokens, or storing jwts in localstorage like they're harmless cookies. this article breaks down the most dangerous jwt mistakes i've encountered and shows you exactly how to fix them before they bite you. Learn how to safeguard your applications from jwt vulnerabilities that can lead to token forgery and data manipulation. discover secure implementation practices with real world example code to ensure robust api security. tagged with javascript, websecurity, jwt, apisecurity.

Jwt Security 101 How To Defend Against Common Attacks On Json Web Learn how to enhance the security of your web applications with robust strategies for managing json web tokens (jwts). from using strong algorithms and handling token storage securely to implementing effective validation techniques, this guide covers all you need to know to safeguard your applications against vulnerabilities. Jwt storage cookie xss protections (httponly & secure flags) are not available for browser local session storage. best practice memory only jwt token handling. protection of the crypto keys (server side). protection against csrf it’s not jwt tokens, it’s about how you use them. memory only jwt & usability. jwt token verification. I've seen too many developers fall into the same traps—using weak secrets, trusting unsigned tokens, or storing jwts in localstorage like they're harmless cookies. this article breaks down the most dangerous jwt mistakes i've encountered and shows you exactly how to fix them before they bite you. Learn how to safeguard your applications from jwt vulnerabilities that can lead to token forgery and data manipulation. discover secure implementation practices with real world example code to ensure robust api security. tagged with javascript, websecurity, jwt, apisecurity.
Jwt Security 101 How To Defend Against Common Attacks On Json Web I've seen too many developers fall into the same traps—using weak secrets, trusting unsigned tokens, or storing jwts in localstorage like they're harmless cookies. this article breaks down the most dangerous jwt mistakes i've encountered and shows you exactly how to fix them before they bite you. Learn how to safeguard your applications from jwt vulnerabilities that can lead to token forgery and data manipulation. discover secure implementation practices with real world example code to ensure robust api security. tagged with javascript, websecurity, jwt, apisecurity.

Jwt Security 101 How To Defend Against Common Attacks On Json Web