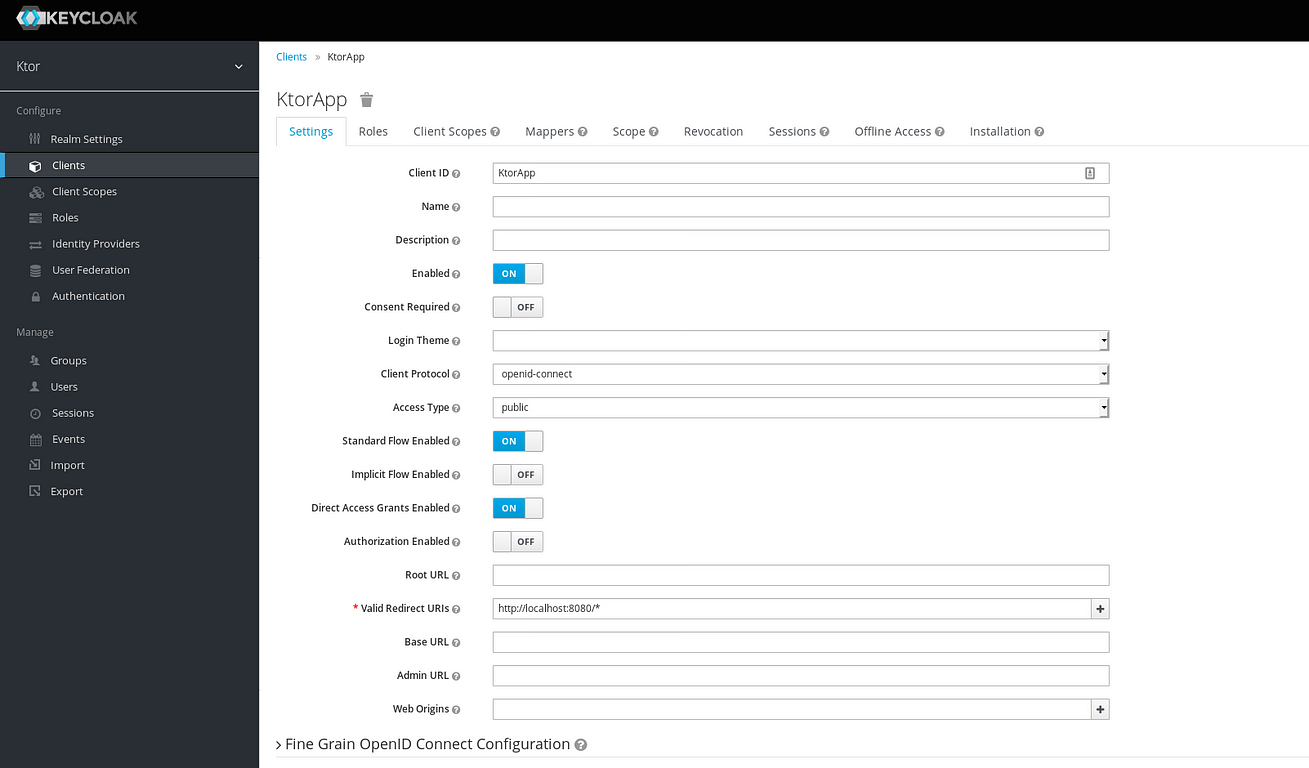
Ktor And Keycloak Authentication With Openid Slickteam According to the version 18 release note. keycloak does not support logout with redirect uri anymore. you need to include post logout redirect uri and id token hint as parameters. please check the answer of this question for more information. keycloak: using react user can login but when i try logout i get a message "invalid parameter: redirect. We are not interested in using keycloak's own client library, we want to use standard oauth2 openid connect client libraries, as the client applications using the keycloak server will be written in a wide range of languages (php, ruby, node, java, c#, angular). therefore the examples that use the keycloak client aren't of use for us.
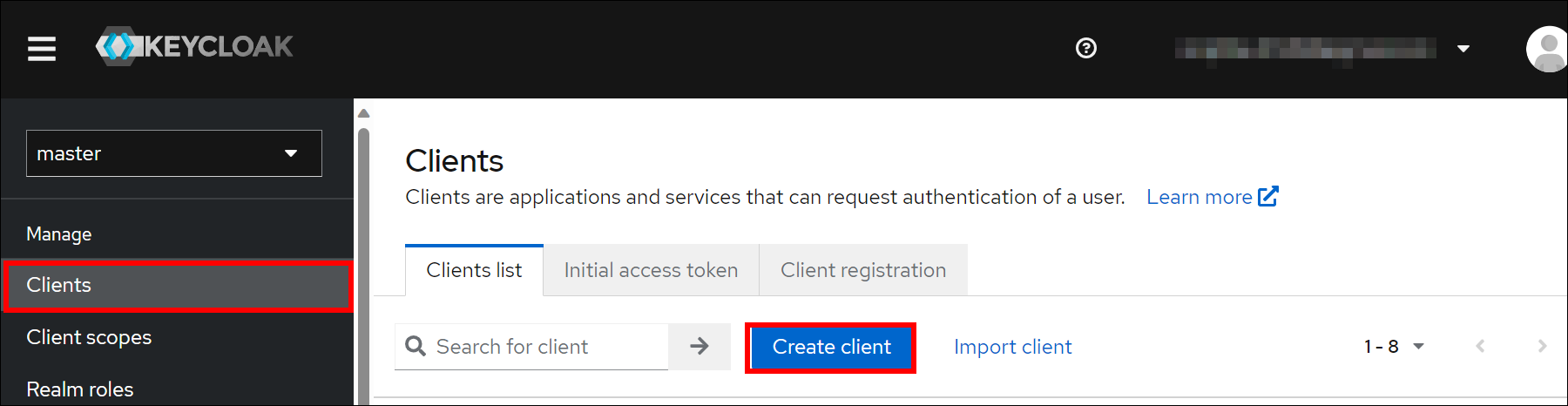
Integrating Bold Reports With Keycloak Via Openid Connect I inspected the certificate from keycloak's ui where you can manually get the public key, and it was a 10 year expiration. but that's not a given that it isn't scheduled to change before that. i'm expecting there to be a short outage, unexplained, some years down the road. : for now i'm just caching the key for 15m at a time. In addition, keycloak is too much about the gui which makes it difficult for me, especially during development. because i also want to provide my team with a local instance of keycloak during development. but what is the concept to import the initial data into realms, apps and also users into keycloak?. You'll need to complete a few actions and gain 15 reputation points before being able to upvote. upvoting indicates when questions and answers are useful. what's reputation and how do i get it? instead, you can save this post to reference later. Look like you know keycloak. is it possible to get a token based on another token? i mean client makes a request to resource server with a jwt token it got from kc. rs1 needs to make a request to rs2. can it get a new token, by using the old token with a different scope from keycloak?.
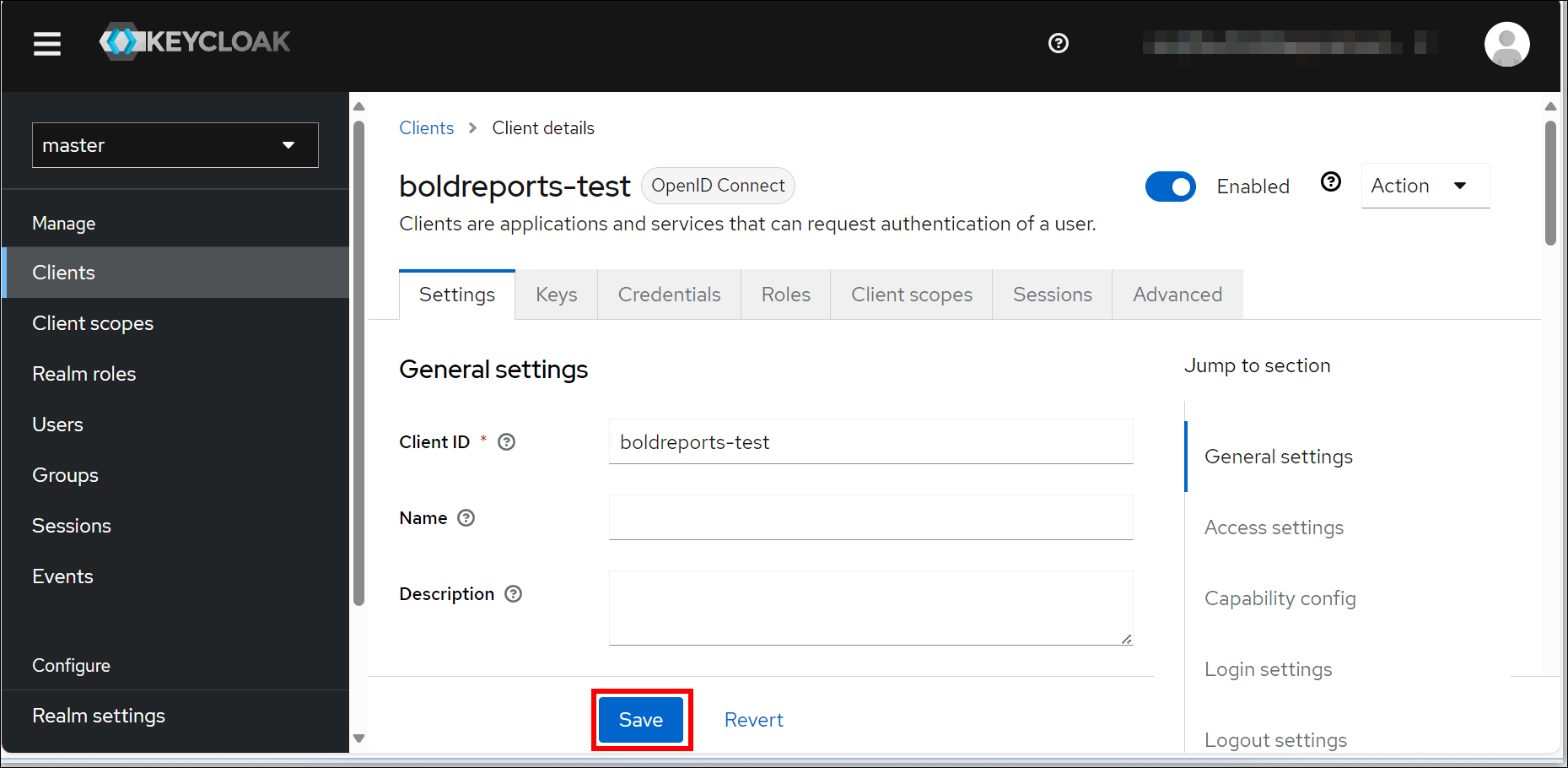
Integrating Bold Reports With Keycloak Via Openid Connect You'll need to complete a few actions and gain 15 reputation points before being able to upvote. upvoting indicates when questions and answers are useful. what's reputation and how do i get it? instead, you can save this post to reference later. Look like you know keycloak. is it possible to get a token based on another token? i mean client makes a request to resource server with a jwt token it got from kc. rs1 needs to make a request to rs2. can it get a new token, by using the old token with a different scope from keycloak?. In keycloak admin console, you can configure mappers under your client. add a builtin mapper of type "user realm role", then open its configuration e.g. change token claim name if you want. client roles can be configured similarly, but they are returned by default in the token under the name resource access.$ {client id}.roles the the client side you can parse the token to find the roles. e.g. Step 2: application requests keycloak to generate the otp for the user associated with the username. the otp returned by keycloak is sent to user via email or sms. step 3: user enters the otp and the application sends the otp to keycloak to validate against that user. step 4: keycloak validates the otp and responds back with access token. Keycloak documentation is a good starting point, check "adding x.509 client certificate authentication to a browser flow" and "adding x.509 client certificate authentication to a direct grant flow" if you need the whole dn for user key, you can use this regex on the config x509 : set "a regular expression to extract user identity" : (.*). I am trying to setup keycloak as a idp (identity provider) and nextcloud as a service. i want to setup keycloak as to present a sso (single sign on) page. i am running a linux server with a intel.
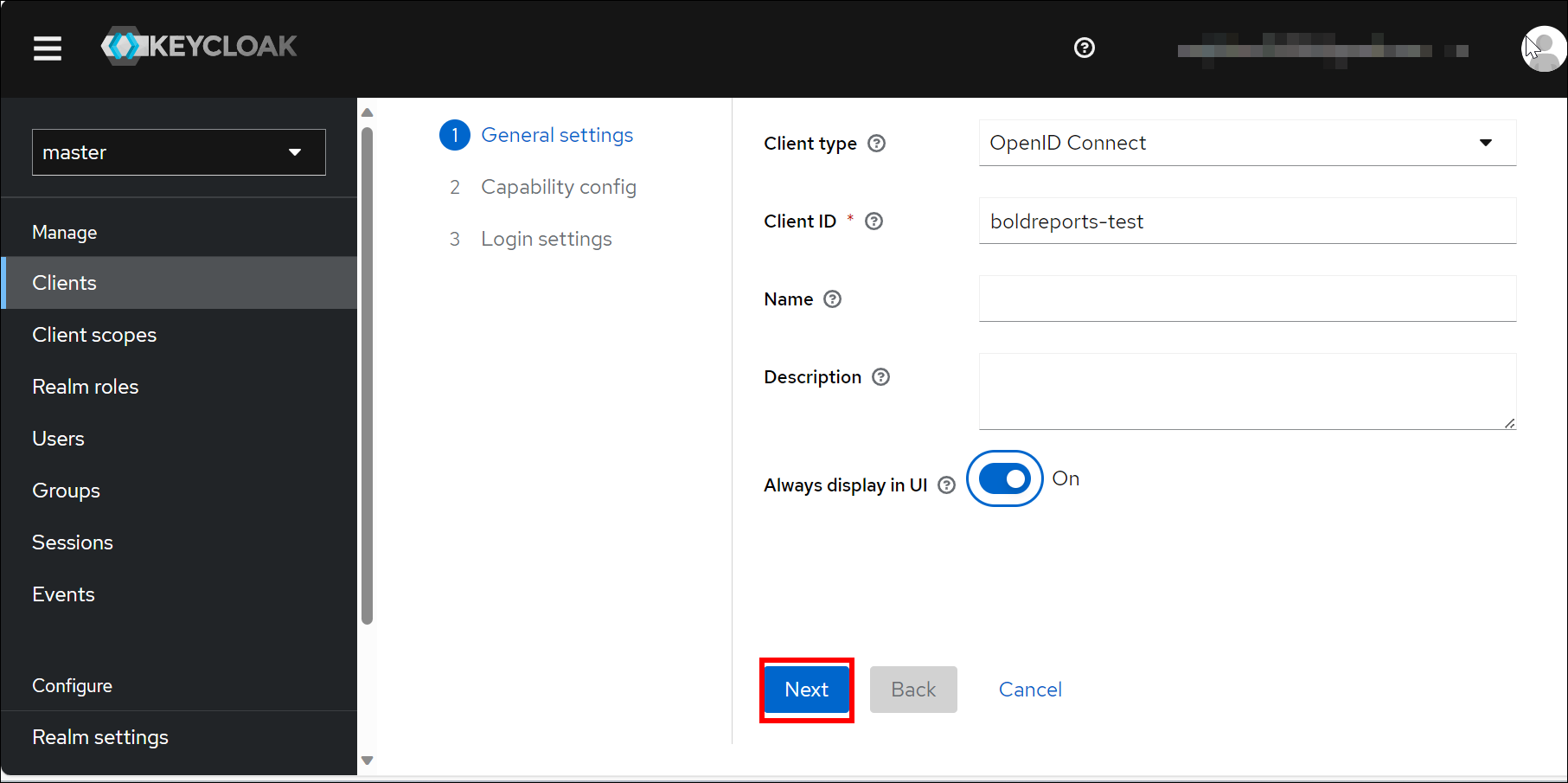
Integrating Bold Reports With Keycloak Via Openid Connect In keycloak admin console, you can configure mappers under your client. add a builtin mapper of type "user realm role", then open its configuration e.g. change token claim name if you want. client roles can be configured similarly, but they are returned by default in the token under the name resource access.$ {client id}.roles the the client side you can parse the token to find the roles. e.g. Step 2: application requests keycloak to generate the otp for the user associated with the username. the otp returned by keycloak is sent to user via email or sms. step 3: user enters the otp and the application sends the otp to keycloak to validate against that user. step 4: keycloak validates the otp and responds back with access token. Keycloak documentation is a good starting point, check "adding x.509 client certificate authentication to a browser flow" and "adding x.509 client certificate authentication to a direct grant flow" if you need the whole dn for user key, you can use this regex on the config x509 : set "a regular expression to extract user identity" : (.*). I am trying to setup keycloak as a idp (identity provider) and nextcloud as a service. i want to setup keycloak as to present a sso (single sign on) page. i am running a linux server with a intel.