
Access Token Management This article explains essential information about access tokens, including formats, ownership, lifetimes and how apis can validate and use the claims inside an access token. An access token is a compact digital artifact, typically in the form of a json web token (jwt), that grants permissions to a user (the resource owner) to access certain resources.

Custom Access Token Auth0 Community We will compare access tokens and id tokens, showing how and where you should use them in your application. we will highlight why access tokens should be treated as opaque by client applications and outline best practices around access token usage, helping you avoid common pitfalls. Token based authentication is a two step authentication strategy to enhance the security mechanism for users to access a network. the users once register their credentials, receive a unique encrypted token that is valid for a specified session time. When a user logs in to a web application, the server issues a session token that is used to identify the user's session. the session token is typically stored in a cookie on the user's computer and is used to authenticate the user on subsequent requests. H = {'authorization': token} check to make sure this is the correct format for the authorization header and not token {token} or bearer {token} or something like that. also, be aware that websites can block non browser based access fairly effectively so you might be getting a captcha because they don't want scripts to hit their site.
Can We Create A Personal Access Token Using Access Token Or Basic Auth When a user logs in to a web application, the server issues a session token that is used to identify the user's session. the session token is typically stored in a cookie on the user's computer and is used to authenticate the user on subsequent requests. H = {'authorization': token} check to make sure this is the correct format for the authorization header and not token {token} or bearer {token} or something like that. also, be aware that websites can block non browser based access fairly effectively so you might be getting a captcha because they don't want scripts to hit their site. Learn about id and access tokens, their role in authentication and authorization, and how to use them correctly in the openid connect and oauth contexts. Token based authentication is a protocol which allows users to verify their identity, and in return receive a unique access token. Get and save an access token at user login, and use the saved access token to have the user log in. use information including an access token that are automatically saved by the kii cloud sdk, and have the user log in. An access token is generated by the logon service when a user logs on to the system and the credentials provided by the user are authenticated against the authentication database.
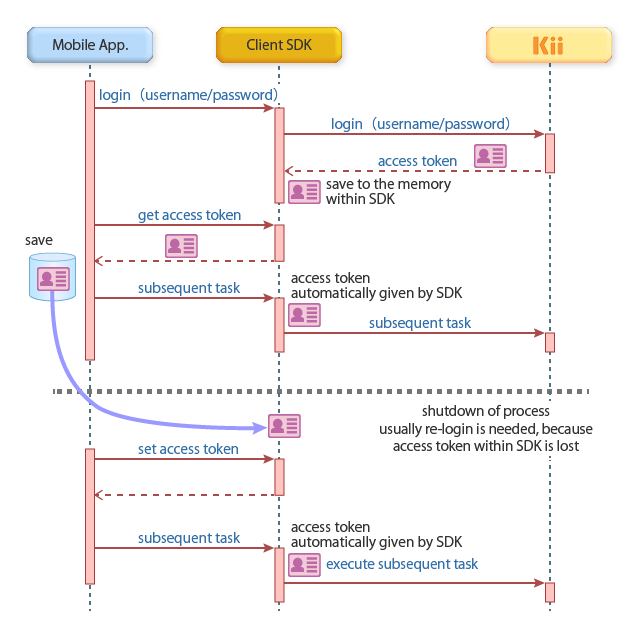
Login By Manually Specifying An Access Token Learn about id and access tokens, their role in authentication and authorization, and how to use them correctly in the openid connect and oauth contexts. Token based authentication is a protocol which allows users to verify their identity, and in return receive a unique access token. Get and save an access token at user login, and use the saved access token to have the user log in. use information including an access token that are automatically saved by the kii cloud sdk, and have the user log in. An access token is generated by the logon service when a user logs on to the system and the credentials provided by the user are authenticated against the authentication database.
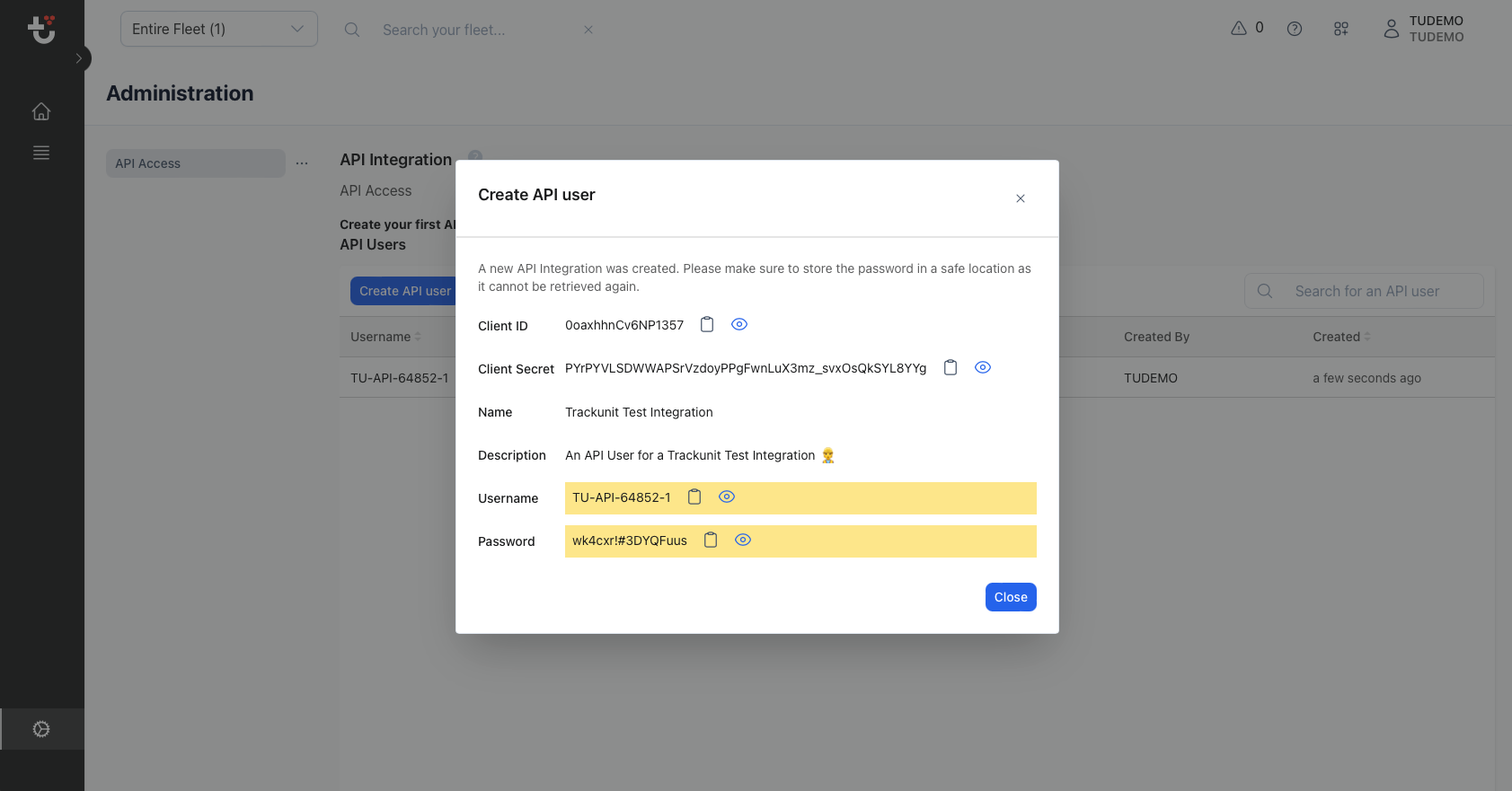
Access Token Get and save an access token at user login, and use the saved access token to have the user log in. use information including an access token that are automatically saved by the kii cloud sdk, and have the user log in. An access token is generated by the logon service when a user logs on to the system and the credentials provided by the user are authenticated against the authentication database.