
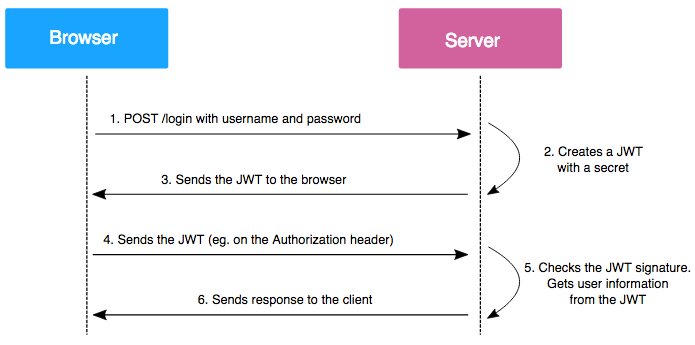
Node Js How To Avoid Manually Copying Jwt Token In Authorization How to add token in authorization header without manually copying it in postman. using axios library. url = your url, data = { headers: { 'authorization': 'bearer ' access token. ); crud examples. this is my demo code. get the access token and get query with access token. try { const resp = await axios.post(. Jwt authentication follows a simple yet effective process. when a user logs in, the server verifies their credentials and, upon successful authentication, issues a jwt. this token is stored on.
Nswag Jwt Token Authorization Openapi Documentation In Asp In this blog post, we will explore best practices for using jwts in your node.js api implementations, avoiding common pitfalls, and ensuring your application remains secure. Learn how to use json web tokens (jwt) securely in your node.js applications. i'll cover the basics of jwt and share best practices to avoid common security mistakes. One effective way to achieve this is by implementing json web token (jwt) authentication and authorization. in this tutorial, we will delve into the technical aspects of securing node.js applications using jwt, covering the core concepts, implementation guide, code examples, best practices, testing and debugging, and conclusion. Json web tokens (jwt) offer a robust solution for token based authentication, enabling secure transmission of user information between parties. this article provides a step by step approach to implementing jwt authentication in node.js applications, enhancing the security of your apis. what is jwt?.
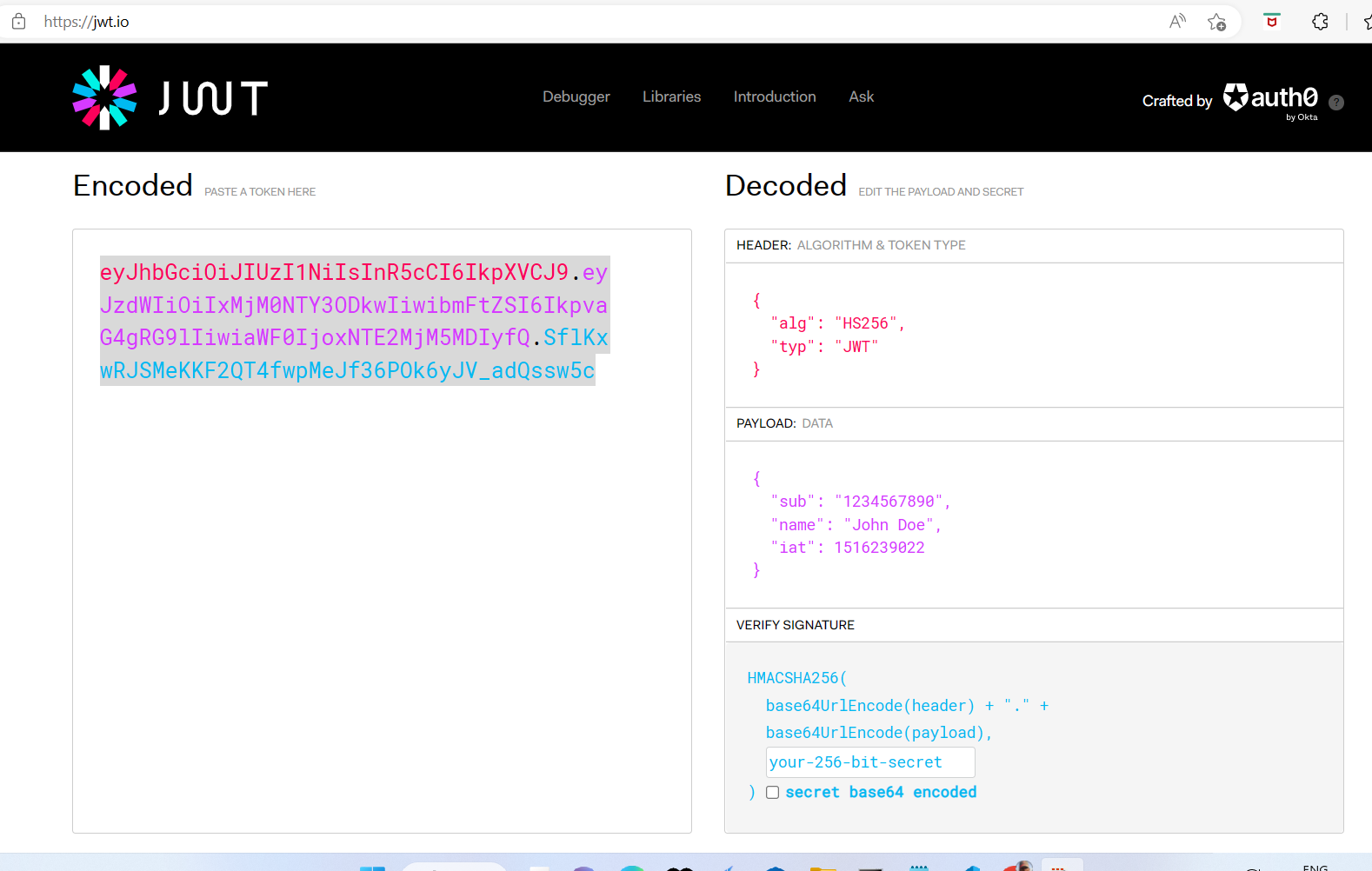
How To Decode A Jwt Token In Node Js With And Without Using External One effective way to achieve this is by implementing json web token (jwt) authentication and authorization. in this tutorial, we will delve into the technical aspects of securing node.js applications using jwt, covering the core concepts, implementation guide, code examples, best practices, testing and debugging, and conclusion. Json web tokens (jwt) offer a robust solution for token based authentication, enabling secure transmission of user information between parties. this article provides a step by step approach to implementing jwt authentication in node.js applications, enhancing the security of your apis. what is jwt?. In this article, we'll dive into what insiders know about jwt authentication in node.js that outsiders might miss. you'll learn how to implement it, the pitfalls to avoid, and why it's such a big deal. Discover the top common mistakes to avoid when implementing jwt in node.js to ensure a secure and efficient authentication process. in the realm of modern web development, the incorporation of robust authentication methods is essential. Step by step guide to implementing secure user auth in a modern node.js backend. covers jwts, hashed passwords, route protection, and middleware using express typescript mongodb. Implement the secure and httponly flags in cookies storing jwts to prevent xss attacks. keep tokens short lived to limit the window for potential abuse, and monitor for unusual activity patterns indicating token misuse. set explicit expiration times for jwts using the exp claim.

How To Decode A Jwt Token In Node Js With And Without Using External In this article, we'll dive into what insiders know about jwt authentication in node.js that outsiders might miss. you'll learn how to implement it, the pitfalls to avoid, and why it's such a big deal. Discover the top common mistakes to avoid when implementing jwt in node.js to ensure a secure and efficient authentication process. in the realm of modern web development, the incorporation of robust authentication methods is essential. Step by step guide to implementing secure user auth in a modern node.js backend. covers jwts, hashed passwords, route protection, and middleware using express typescript mongodb. Implement the secure and httponly flags in cookies storing jwts to prevent xss attacks. keep tokens short lived to limit the window for potential abuse, and monitor for unusual activity patterns indicating token misuse. set explicit expiration times for jwts using the exp claim. In this part, we’ll walk through how to implement jwt in a nodejs application. you’ll learn how to: set up jwt based authentication. secure your api routes using jwt. generate and verify. Jwts provide an effective and straightforward way to handle user authentication without relying on session storage. 🔒 use https: protects the token from being intercepted in transit. 🔒 set expiry time: tokens should expire after a reasonable duration (e.g., 1 hour). 🔒 use strong secret keys: avoid weak or hardcoded secrets.

How Can I Decode A Token In Node Js Jwt Verify Fails Stack Overflow Step by step guide to implementing secure user auth in a modern node.js backend. covers jwts, hashed passwords, route protection, and middleware using express typescript mongodb. Implement the secure and httponly flags in cookies storing jwts to prevent xss attacks. keep tokens short lived to limit the window for potential abuse, and monitor for unusual activity patterns indicating token misuse. set explicit expiration times for jwts using the exp claim. In this part, we’ll walk through how to implement jwt in a nodejs application. you’ll learn how to: set up jwt based authentication. secure your api routes using jwt. generate and verify. Jwts provide an effective and straightforward way to handle user authentication without relying on session storage. 🔒 use https: protects the token from being intercepted in transit. 🔒 set expiry time: tokens should expire after a reasonable duration (e.g., 1 hour). 🔒 use strong secret keys: avoid weak or hardcoded secrets.