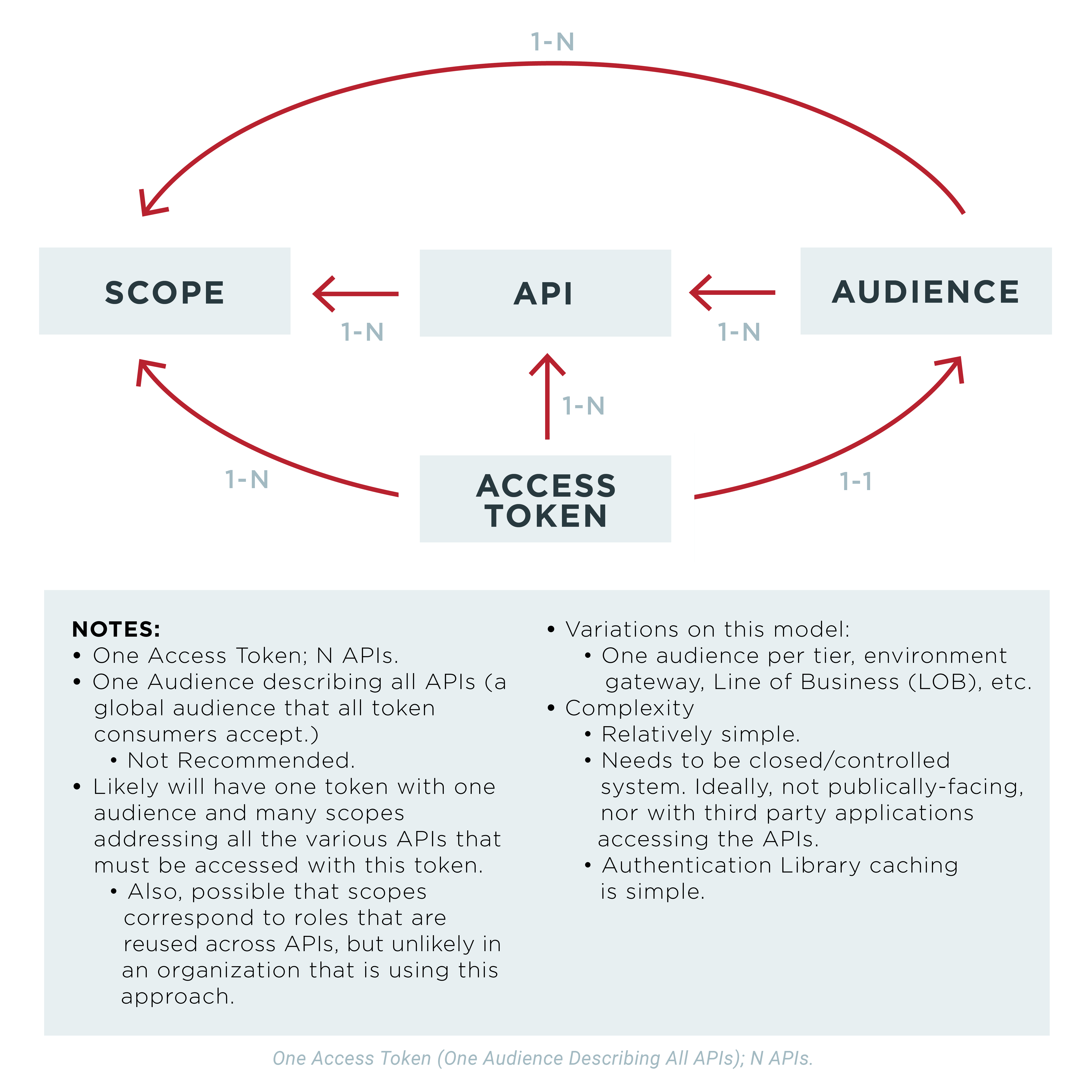
Option 2 Single Access Token With Multiple Audiences When an application consumes a variety of different apis, often all endpoints require an oauth 2 access token issued from a common identity provider, with appropriate security token checks in place. gain an understanding of three primary approaches for best employing oauth 2 access tokens. In the first post of this series, “ oauth 2 access token usage strategies for multiple resources (apis): part 1, ” we explored several options for using oauth 2 access tokens with.
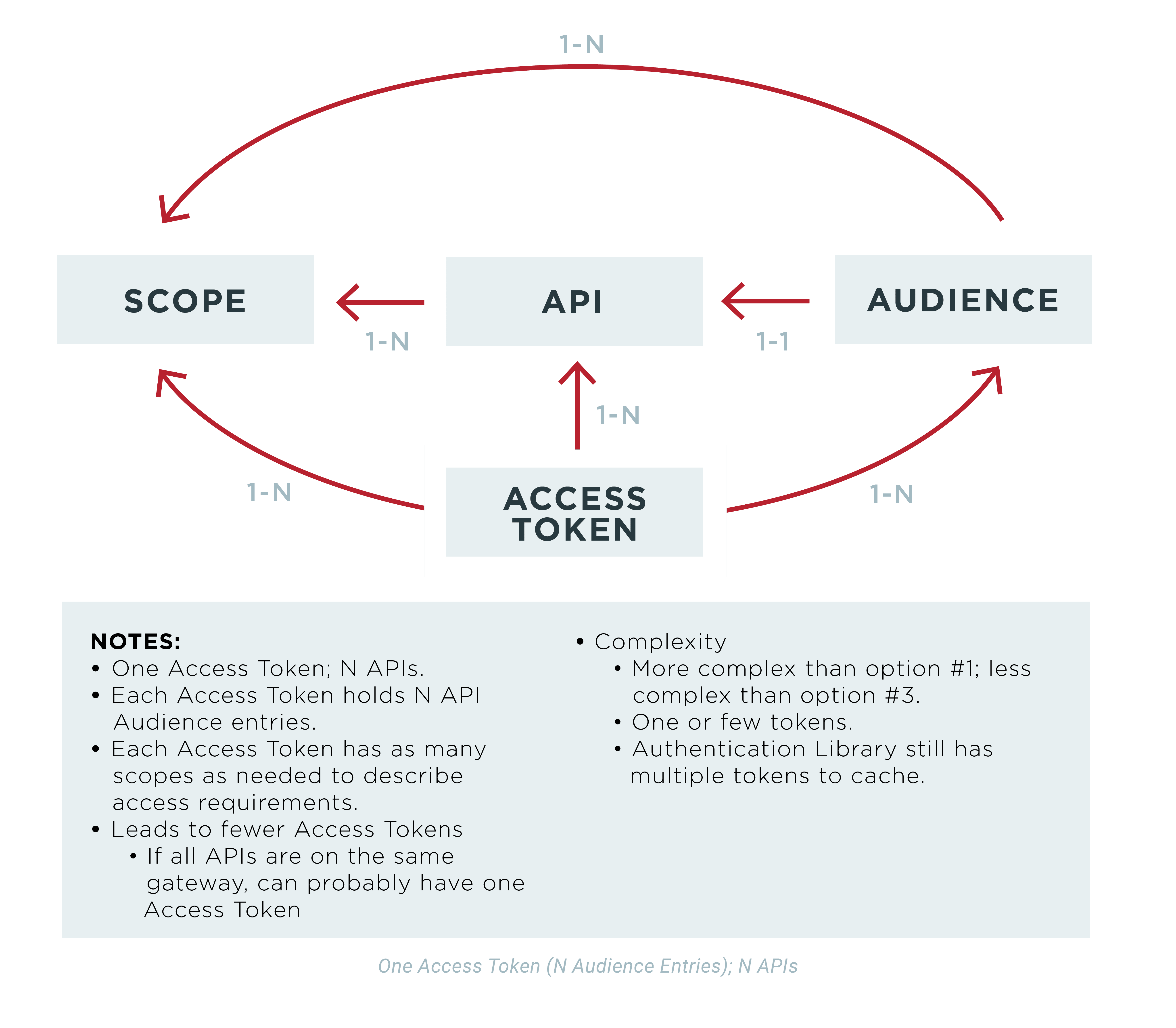
Option 3 Multiple Access Tokens Below i'm explaining how you can make this scenario work by reusing refresh tokens and without passing both resource ids in same call. (note: this approach will work for authorization code grant flow but not for implicit grant flow like a javascript based spa, because no refresh token is returned in that case). Oauth 2.0 is an open authorization framework that allows for secure authorization across systems. this delegated authorization works without exposing the user’s credentials. instead, the process uses tokens, which clients and servers can use to authorize access on behalf of the user. Should the application obtain a single access token that is used against all apis, use multiple access tokens where each has the limited information needed for a particular api, or do. In this article, we will explore best practices for securing apis, focusing on the effective use of oauth 2.0, api keys, and other authentication and authorization methods. additionally,.
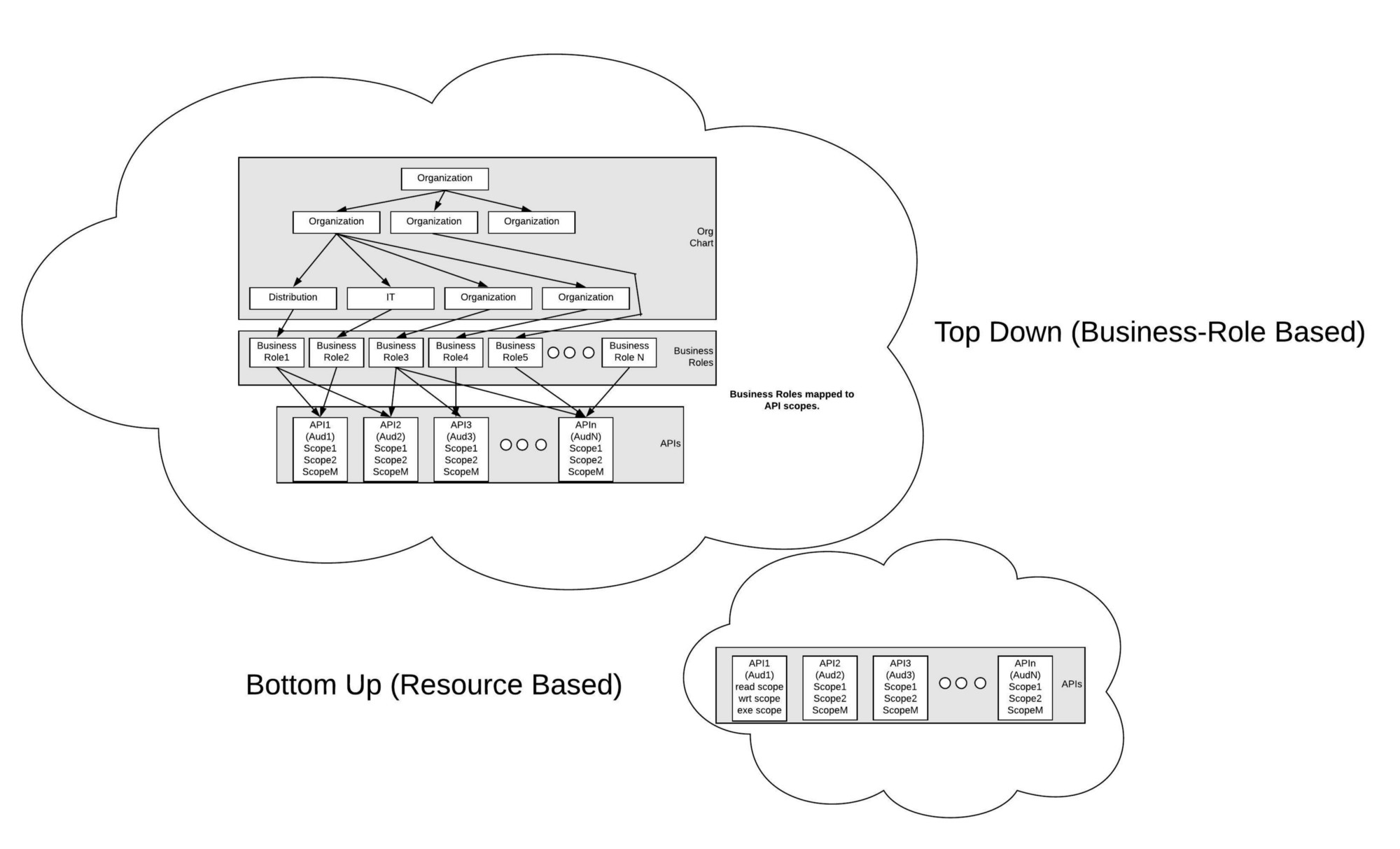
You Can See An Example Of Each Approach Of Building An Authorization Should the application obtain a single access token that is used against all apis, use multiple access tokens where each has the limited information needed for a particular api, or do. In this article, we will explore best practices for securing apis, focusing on the effective use of oauth 2.0, api keys, and other authentication and authorization methods. additionally,. Apps using the oauth 2.0 authorization code flow acquire an access token to include in requests to resources protected by the microsoft identity platform (typically apis). apps can also request new id and access tokens for previously authenticated entities by using a refresh mechanism. this diagram shows a high level view of the authentication. There are several options for using oauth 2 access tokens with multiple back end resources (apis) with single page applications or mobile applications. read this post to discover how scope and audience are used to describe resources and how these different options might be implemented. Token redirect: an attacker uses a token generated for consumption by one resource server to gain access to a different resource server that mistakenly believes the token to be for it. Oauth 2.0 is a key technology in web development, especially when it comes to login and permissions. it allows apps to get limited access to user accounts on services like facebook, google,.
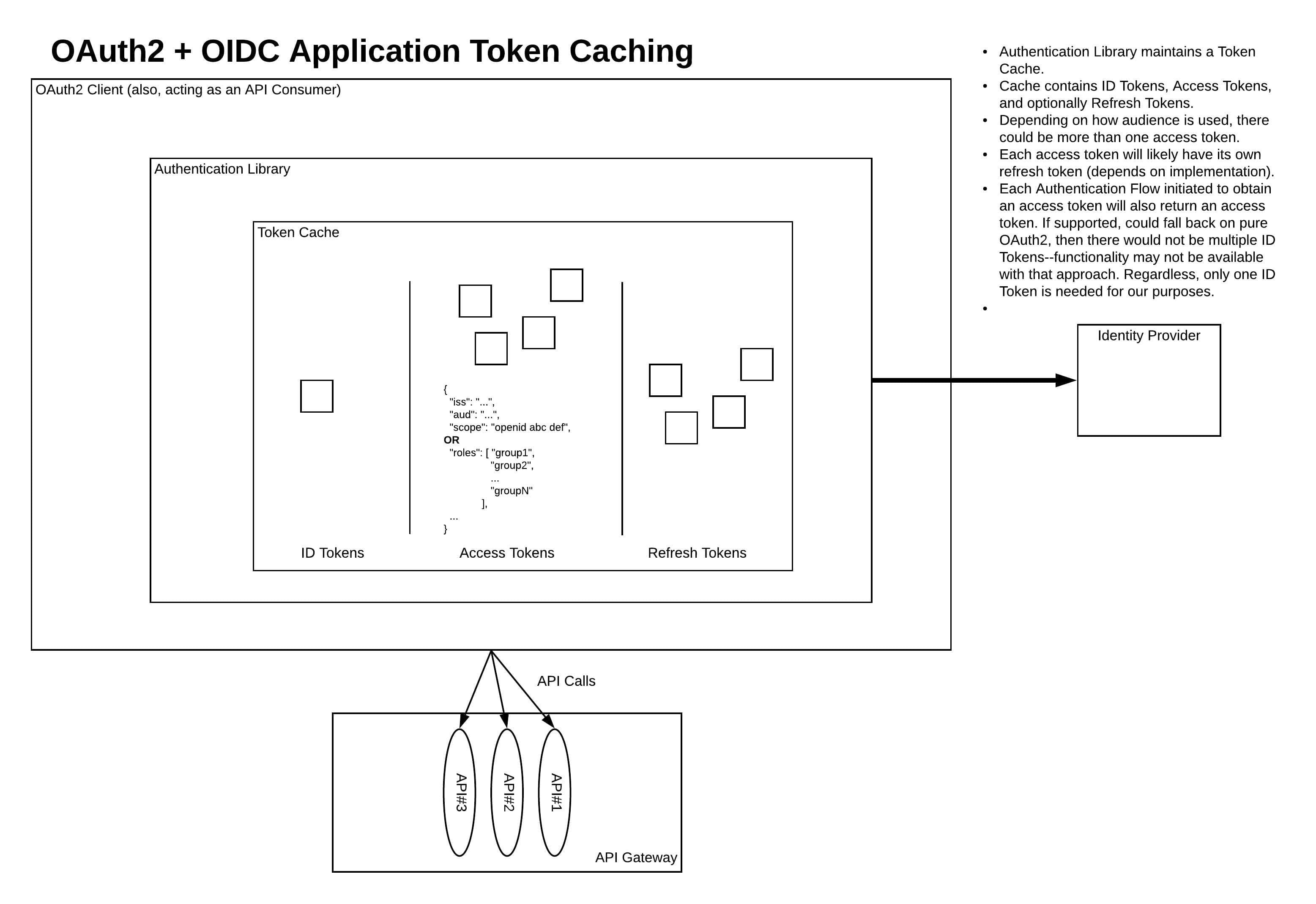
Click Here To View A Larger Version Apps using the oauth 2.0 authorization code flow acquire an access token to include in requests to resources protected by the microsoft identity platform (typically apis). apps can also request new id and access tokens for previously authenticated entities by using a refresh mechanism. this diagram shows a high level view of the authentication. There are several options for using oauth 2 access tokens with multiple back end resources (apis) with single page applications or mobile applications. read this post to discover how scope and audience are used to describe resources and how these different options might be implemented. Token redirect: an attacker uses a token generated for consumption by one resource server to gain access to a different resource server that mistakenly believes the token to be for it. Oauth 2.0 is a key technology in web development, especially when it comes to login and permissions. it allows apps to get limited access to user accounts on services like facebook, google,.

Related Posts Token redirect: an attacker uses a token generated for consumption by one resource server to gain access to a different resource server that mistakenly believes the token to be for it. Oauth 2.0 is a key technology in web development, especially when it comes to login and permissions. it allows apps to get limited access to user accounts on services like facebook, google,.