Oauth2 Protocol Flow Access Token Flow Strategies Flow are ways of retrieving an access token. deciding which one is suited for your use case depends mostly on your application type, but other parameters weigh in as well, like the level of trust for the client, or the experience you want your users to have. Oauth 2.0 is an authorization framework that enables applications to obtain limited access to user accounts on an http service. it works by delegating user authentication to the service that.
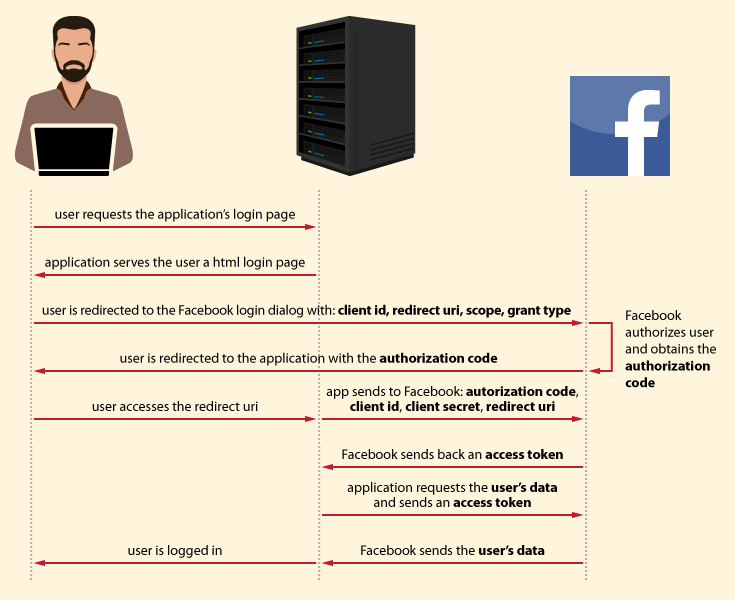
Oauth2 Protocol Flow Access Token Flow Strategies Learn about different oauth flows, including authorization code, implicit, and more. discover their use cases to secure user authentication. Apps using the oauth 2.0 authorization code flow acquire an access token to include in requests to resources protected by the microsoft identity platform (typically apis). apps can also request new id and access tokens for previously authenticated entities by using a refresh mechanism. this diagram shows a high level view of the authentication. Oauth 2.0 is an industry standard authorization protocol. oauth flows are different ways of retrieving access tokens. depending on your app’s needs and requirements, you’ll need to select the right oauth flow to keep your platform secure and functional. To get an initial token that represents the client and not a user, use the client credentials flow. use the client credentials flow to get an access token in machine to machine scenarios. can users authenticate on the same device?.
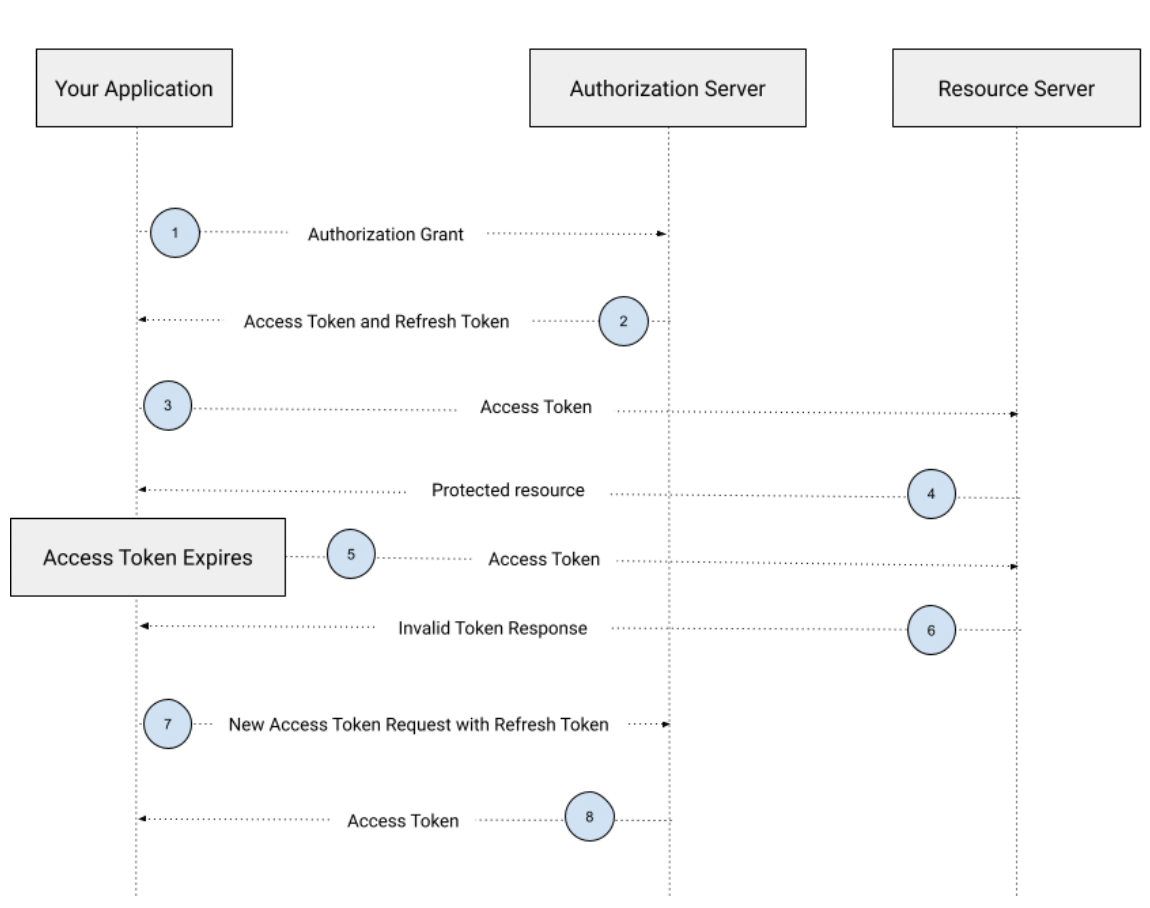
Oauth2 Protocol Flow Access Token Flow Strategies Oauth 2.0 is an industry standard authorization protocol. oauth flows are different ways of retrieving access tokens. depending on your app’s needs and requirements, you’ll need to select the right oauth flow to keep your platform secure and functional. To get an initial token that represents the client and not a user, use the client credentials flow. use the client credentials flow to get an access token in machine to machine scenarios. can users authenticate on the same device?. A developer's guide to understanding oauth 2.0: roles, grant types (authorization code, client credentials), tokens (access, refresh), scopes, security best practices, and an example flow. While this flow was originally designed for scenarios such as token requests from single page applications (spas), the authorization code flow with pkce is now the recommended approach for spas. Diagrams and movies of all the 4 authorization flows defined in rfc 6749 (the oauth 2.0 authorization framework) and one more flow to re issue an access token using a refresh token. Oauth 2.0 defines several authorization flows to cater to different scenarios: authorization code flow: ideal for server side applications, where an authorization code is exchanged for an access token. implicit flow: used for browser based applications, returning the access token directly in the url fragment.
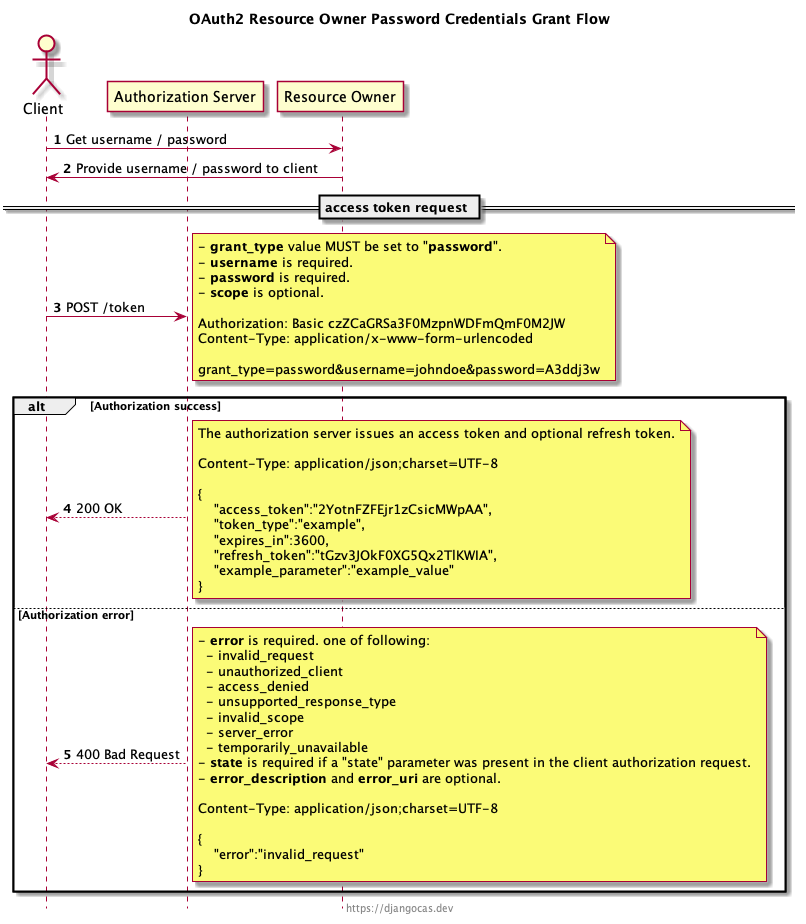
Oauth2 Protocol Flow Access Token Flow Strategies A developer's guide to understanding oauth 2.0: roles, grant types (authorization code, client credentials), tokens (access, refresh), scopes, security best practices, and an example flow. While this flow was originally designed for scenarios such as token requests from single page applications (spas), the authorization code flow with pkce is now the recommended approach for spas. Diagrams and movies of all the 4 authorization flows defined in rfc 6749 (the oauth 2.0 authorization framework) and one more flow to re issue an access token using a refresh token. Oauth 2.0 defines several authorization flows to cater to different scenarios: authorization code flow: ideal for server side applications, where an authorization code is exchanged for an access token. implicit flow: used for browser based applications, returning the access token directly in the url fragment.