
Openid Connect Authentication Google For Developers I'm really trying to understand the difference between openid and oauth? maybe they're two totally separate things?. I am a little curious to know about how openid authentication works. is there any difference between openid authentication and the authentication which sites use exclusively for themselves?.

Openid Connect Sign In With Google Google For Developers It serves as a token validation parameter and is introduced from openid connect specification. nonce string value used to associate a client session with an id token, and to mitigate replay attacks. With openid, a user login is usually an http address of the resource which is responsible for the authentication. on the other hand, saml is based on an explicit trust between your site and the identity provider so it's rather uncommon to accept credentials from an unknown site. openid identities are easy to get around the net. The thing that this client communicates with using the openid connect protocol is called an openid connect provider (op) and is often also referred to as an identity provider (idp). the first part of the client implementation will show a view that contains a button. this button will be the typical "login" or "sign in" button. 8 when you make the first request to the authorization endpoint, you have to include openid in the scope request parameter. openid connect core 1.0, 3.1.2.1. authentication request says as follows. scope required. openid connect requests must contain the openid scope value. if the openid scope value is not present, the behavior is entirely.
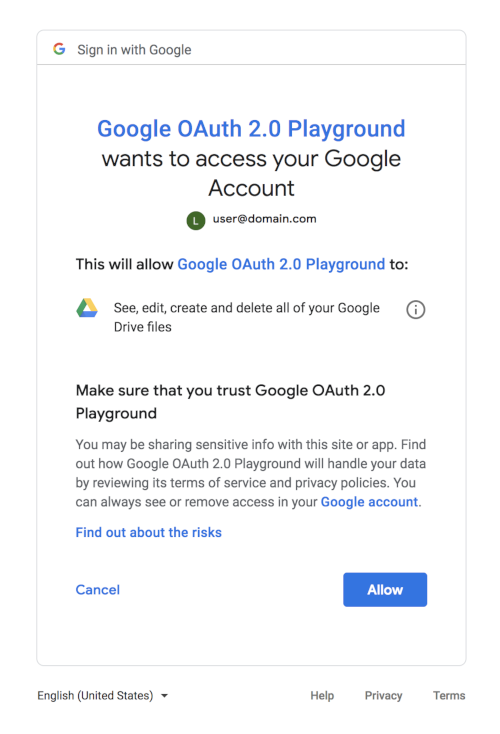
Openid Connect Sign In With Google Google For Developers The thing that this client communicates with using the openid connect protocol is called an openid connect provider (op) and is often also referred to as an identity provider (idp). the first part of the client implementation will show a view that contains a button. this button will be the typical "login" or "sign in" button. 8 when you make the first request to the authorization endpoint, you have to include openid in the scope request parameter. openid connect core 1.0, 3.1.2.1. authentication request says as follows. scope required. openid connect requests must contain the openid scope value. if the openid scope value is not present, the behavior is entirely. I've read repeatedly that openid is better for authentication than oauth (which is for authorization), including several other posts on so. the case also seems to be made in this often cited article. however, i'm a bit unclear on why i should favor openid for authentication, vs. an honest oauth provider (e.g. twitter or facebook oauth 2.0). We are not interested in using keycloak's own client library, we want to use standard oauth2 openid connect client libraries, as the client applications using the keycloak server will be written in a wide range of languages (php, ruby, node, java, c#, angular). therefore the examples that use the keycloak client aren't of use for us. Originally, oauth and openid are designed for different purpose: openid for authentication and oauth for authorization. openid connect is a unification of the two and serves for both, but does not change their original functionalities. keeping that in mind, you should be able to find out yourself. ; ) the id token is used to identify the authenticated user, e.g. for sso. the access token must. How would you design and implement openid components? (was "how does openid work") i realize this question is somewhat of a duplicate, and yes, i have read the spec and the article. af.
Openid Connect Sign In With Google Google For Developers I've read repeatedly that openid is better for authentication than oauth (which is for authorization), including several other posts on so. the case also seems to be made in this often cited article. however, i'm a bit unclear on why i should favor openid for authentication, vs. an honest oauth provider (e.g. twitter or facebook oauth 2.0). We are not interested in using keycloak's own client library, we want to use standard oauth2 openid connect client libraries, as the client applications using the keycloak server will be written in a wide range of languages (php, ruby, node, java, c#, angular). therefore the examples that use the keycloak client aren't of use for us. Originally, oauth and openid are designed for different purpose: openid for authentication and oauth for authorization. openid connect is a unification of the two and serves for both, but does not change their original functionalities. keeping that in mind, you should be able to find out yourself. ; ) the id token is used to identify the authenticated user, e.g. for sso. the access token must. How would you design and implement openid components? (was "how does openid work") i realize this question is somewhat of a duplicate, and yes, i have read the spec and the article. af.

Google Identity Google Developers Originally, oauth and openid are designed for different purpose: openid for authentication and oauth for authorization. openid connect is a unification of the two and serves for both, but does not change their original functionalities. keeping that in mind, you should be able to find out yourself. ; ) the id token is used to identify the authenticated user, e.g. for sso. the access token must. How would you design and implement openid components? (was "how does openid work") i realize this question is somewhat of a duplicate, and yes, i have read the spec and the article. af.
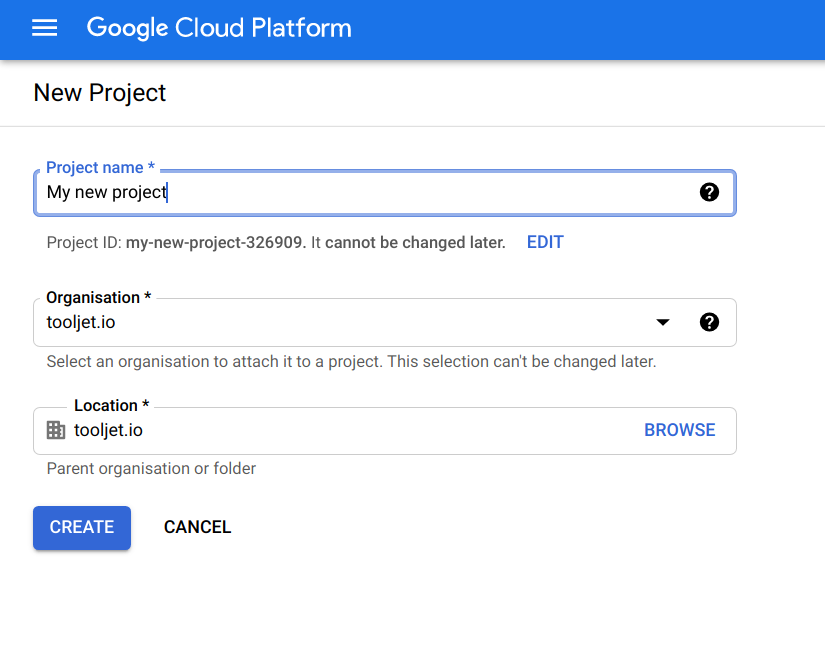
Google Open Id Tooljet