Download Lock Key Radial Brain Powerpoint Infographic Template Secret key systems encrypting a small block of text (say 64 bits) general considerations: encrypted data should look random. as though someone flipped a fair coin 64 times and heads means 1 and tails 0. This document summarizes classical encryption techniques such as secret key cryptography, stream ciphers, block ciphers, substitution techniques like the caesar cipher and playfair cipher, polyalphabetic ciphers like the vigenère cipher, and the theoretically unbreakable one time pad cipher.

Security Lock Key Powerpoint Template Presentationpro Secret key encryption • also known as symmetric encryption • encrypted message = encrypt (key, message) • message = decrypt (key, encrypted message) • example: encrypt = division • 433 = 48 r 1 (using divisor of 9). Transformation to the ciphertext block using the same secret key. 6 properties of good ciphersconfusion and diffusion in cryptography, confusion and diffusion are two properties of the operation of a secure cipher which were identified by shannon in his paper, "communication theory of secrecy systems" published in 1949. The document discusses secret key cryptography, which involves using the same key for both encryption and decryption, and is classified into block and stream ciphers. Secret key cryptography goal: take a reasonable length key and generate a one to one mapping to ciphertext that looks random to someone who doesn’t know the key.

Lock And Key Security Powerpoint Templates Ppt Themes And Graphics 0113 The document discusses secret key cryptography, which involves using the same key for both encryption and decryption, and is classified into block and stream ciphers. Secret key cryptography goal: take a reasonable length key and generate a one to one mapping to ciphertext that looks random to someone who doesn’t know the key. Des intro • des – data encryption standard • published in 1977 by national bureau of standards (now nist) with input from nsa • based on ibm lucifer cipher • encodes 64 bit blocks • uses 56 bit key • key consists of 8 octets, where 7 bits are useful and 8th is parity • efficient to implement in hardware, but slow in software. Use a public key cryptosystem to send negotiate a randomly generated secret key with the party to whom you wish to communicate. then use that secret key with a symmetric key cryptosystem. october 18, 2016. practical aspects of modern cryptography. encryption. you’ve got some data you want to protect. of course you’d encrypt. you take your key and …. Unit 2 symmetric key techniques (part 1).ppt free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. this document provides an overview of symmetric key encryption techniques, also known as classical or secret key encryption. Why public key cryptography? developed to address two key issues: key distribution – how to have secure communications in general without having to trust a kdc with your key digital signatures – how to verify a message comes intact from the claimed sender public invention due to whitfield diffie & martin hellman at stanford uni in 1976.

Key Locked With Chain Security Powerpoint Templates Ppt Backgrounds For Des intro • des – data encryption standard • published in 1977 by national bureau of standards (now nist) with input from nsa • based on ibm lucifer cipher • encodes 64 bit blocks • uses 56 bit key • key consists of 8 octets, where 7 bits are useful and 8th is parity • efficient to implement in hardware, but slow in software. Use a public key cryptosystem to send negotiate a randomly generated secret key with the party to whom you wish to communicate. then use that secret key with a symmetric key cryptosystem. october 18, 2016. practical aspects of modern cryptography. encryption. you’ve got some data you want to protect. of course you’d encrypt. you take your key and …. Unit 2 symmetric key techniques (part 1).ppt free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. this document provides an overview of symmetric key encryption techniques, also known as classical or secret key encryption. Why public key cryptography? developed to address two key issues: key distribution – how to have secure communications in general without having to trust a kdc with your key digital signatures – how to verify a message comes intact from the claimed sender public invention due to whitfield diffie & martin hellman at stanford uni in 1976.

2013 On Golden Key Security Powerpoint Templates Ppt Backgrounds For Unit 2 symmetric key techniques (part 1).ppt free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. this document provides an overview of symmetric key encryption techniques, also known as classical or secret key encryption. Why public key cryptography? developed to address two key issues: key distribution – how to have secure communications in general without having to trust a kdc with your key digital signatures – how to verify a message comes intact from the claimed sender public invention due to whitfield diffie & martin hellman at stanford uni in 1976.
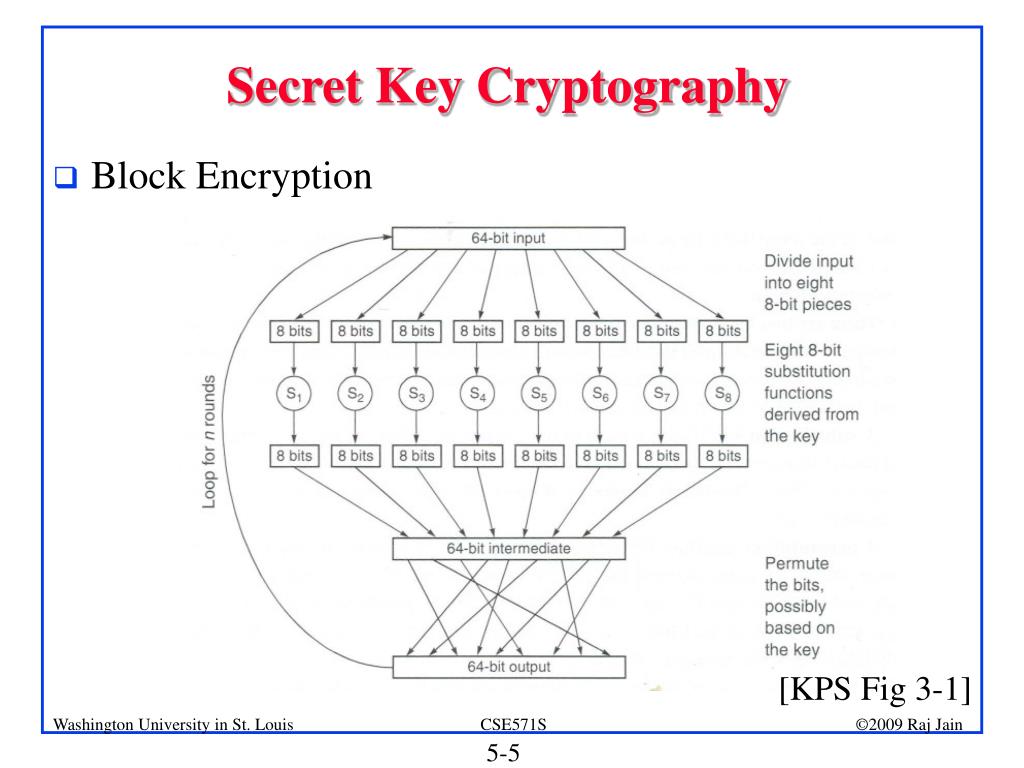
Ppt Secret Key Cryptography Powerpoint Presentation Free Download