
Module 5 Cyber Security 1 2 Pdf Module 2: written work: cyber security and secure cloud outsourcing 1. for this activity you must watch the cyber security video duration: (12:47) 2. based on this video and any other resources you research, what is your reaction to the information provided in the video regarding cyber security? 3. Since rest apis lack inherent security mechanisms, security must be meticulously integrated into data transmission and client interaction functions. this makes api security a critical consideration for this application. encapsulation provides an additional layer of security by restricting access to sensitive data.

Cybersecurity Module 2 Lesson 8 Notes Pdf Security Computer Security Cybersecurity module 2 adversarial artificial intelligence (ai) click the card to flip 👆 a technique that manipulates artificial intelligence (ai) and machine learning (ml) technology to conduct attacks more efficiently. Written assignment: cyber security and secure cloud outsourcing perform an analysis of the following case, related to secure subcontracting in the cloud. your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on. Module2 cs 305 module two written assignment template zach shackleton instructions replace the bracketed text with the relevant information in your own words. What is the role of problem solving in the context of cybersecurity? don't know? which of the following stores information such as user data, transaction details, or product records? which technical skill entails the knowledge of firewalls, intrusion detection systems, and secure network architectures?.
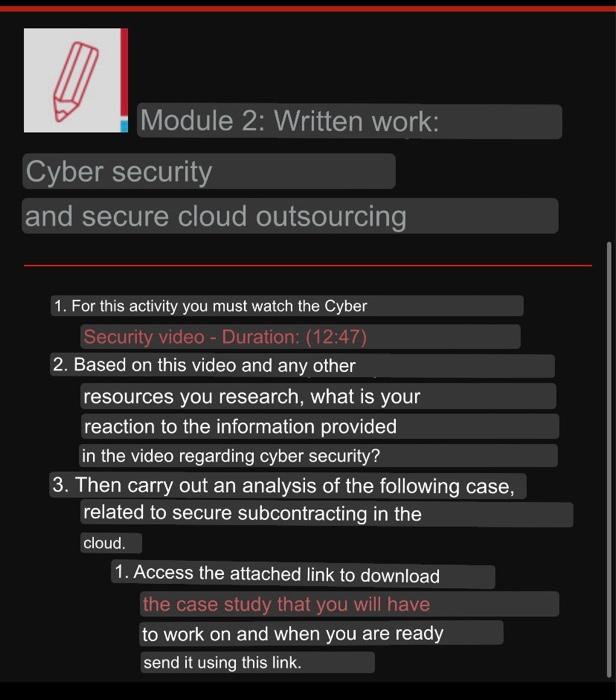
Solved Module 2 Written Work Cyber Security And Secure Chegg Module2 cs 305 module two written assignment template zach shackleton instructions replace the bracketed text with the relevant information in your own words. What is the role of problem solving in the context of cybersecurity? don't know? which of the following stores information such as user data, transaction details, or product records? which technical skill entails the knowledge of firewalls, intrusion detection systems, and secure network architectures?. Our expert help has broken down your problem into an easy to learn solution you can count on. here’s the best way to solve it. not the question you’re looking for? post any question and get expert help quickly. © 2003 2025 chegg inc. all rights reserved. Specify which fundamental security design principle best applies by marking all appropriate cells with an x. indicate which security objective (confidentiality, availability, or integrity) best reflects your selected control recommendation. Study with quizlet and memorize flashcards containing terms like information security, four important functions of information security, data security and more. Cyb 240 module two lab worksheet course: application security (cyb 240) 361 documents university: southern new hampshire university.

Assignment 2 Cyber Security Pdf Our expert help has broken down your problem into an easy to learn solution you can count on. here’s the best way to solve it. not the question you’re looking for? post any question and get expert help quickly. © 2003 2025 chegg inc. all rights reserved. Specify which fundamental security design principle best applies by marking all appropriate cells with an x. indicate which security objective (confidentiality, availability, or integrity) best reflects your selected control recommendation. Study with quizlet and memorize flashcards containing terms like information security, four important functions of information security, data security and more. Cyb 240 module two lab worksheet course: application security (cyb 240) 361 documents university: southern new hampshire university.

Chapter 2 Cyber Security Pdf Cloud Computing Malware Study with quizlet and memorize flashcards containing terms like information security, four important functions of information security, data security and more. Cyb 240 module two lab worksheet course: application security (cyb 240) 361 documents university: southern new hampshire university.